- All Exams Instant Download
Which of the following options fulfills this requirement?
A company hosted an e-commerce website on an Auto Scaling group of EC2 instances behind an Application Load Balancer. The Solutions Architect noticed that the website is receiving a large number of illegitimate external requests from multiple systems with IP addresses that constantly change. To resolve the performance issues, the Solutions Architect must implement a solution that would block the illegitimate requests with minimal impact on legitimate traffic .
Which of the following options fulfills this requirement?
A . Create a custom rule in the security group of the Application Load Balancer to block the offending requests.
B . Create a custom network ACL and associate it with the subnet of the Application Load Balancer to block the offending requests.
C . Create a rate-based rule in AWS WAF and associate the web ACL to an Application Load Balancer.
D . Create a regular rule in AWS WAF and associate the web ACL to an Application Load Balancer.
Answer: C
Explanation:
AWS WAF is tightly integrated with Amazon CloudFront, the Application Load Balancer (ALB), Amazon API Gateway, and AWS AppSync C services that AWS customers commonly use to deliver content for their websites and applications. When you use AWS WAF on Amazon CloudFront, your rules run in all AWS Edge Locations, located around the world close to your end-users. This means security doesn’t come at the expense of performance. Blocked requests are stopped before they reach your web servers. When you use AWS WAF on regional services, such as Application Load Balancer, Amazon API Gateway, and AWS AppSync, your rules run in the region and can be used to protect Internet-facing resources as well as internal resources.
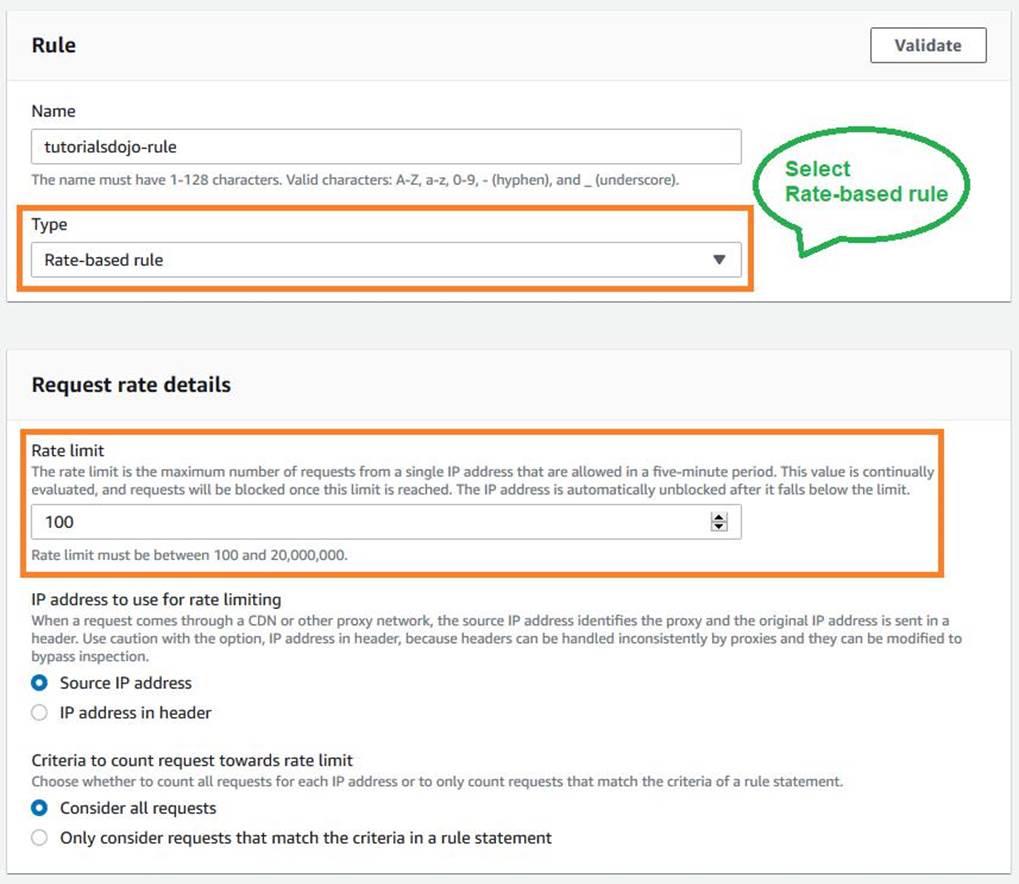
A rate-based rule tracks the rate of requests for each originating IP address and triggers the rule action on IPs with rates that go over a limit. You set the limit as the number of requests per 5-minute time span. You can use this type of rule to put a temporary block on requests from an IP address that’s sending excessive requests.
Based on the given scenario, the requirement is to limit the number of requests from the illegitimate requests without affecting the genuine requests. To accomplish this requirement, you can use AWS WAF web ACL. There are two types of rules in creating your own web ACL rule: regular and rate-based rules. You need to select the latter to add a rate limit to your web ACL. After creating the web ACL, you can associate it with ALB. When the rule action triggers, AWS WAF applies the action to additional requests from the IP address until the request rate falls below the limit.
Hence, the correct answer is: Create a rate-based rule in AWS WAF and associate the web ACL to an Application Load Balancer.
The option that says: Create a regular rule in AWS WAF and associate the web ACL to an Application Load Balancer is incorrect because a regular rule only matches the statement defined in the rule. If you need to add a rate limit to your rule, you should create a rate-based rule.
The option that says: Create a custom network ACL and associate it with the subnet of the Application Load Balancer to block the offending requests is incorrect. Although NACLs can help you block incoming traffic, this option wouldn’t be able to limit the number of requests from a single IP address that is dynamically changing.
The option that says: Create a custom rule in the security group of the Application Load Balancer to
block the offending requests is incorrect because the security group can only allow incoming traffic.
Remember that you can’t deny traffic using security groups. In addition, it is not capable of limiting the
rate of traffic to your application unlike AWS WAF.
References:
https://docs.aws.amazon.com/waf/latest/developerguide/waf-rule-statement-type-rate-based.html
https://aws.amazon.com/waf/faqs/
Check out this AWS WAF Cheat Sheet:
https://tutorialsdojo.com/aws-waf/
AWS Security Services Overview – WAF, Shield, CloudHSM, KMS:
https://www.youtube.com/watch?v=-1S-RdeAmMo
Latest SAA-C03 Dumps Valid Version with 400 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

