- All Exams Instant Download
What needs to be configured outside of the VPC for them to have a successful site-to-site VPN connection?
An insurance company utilizes SAP HANA for its day-to-day ERP operations. Since they can’t migrate this database due to customer preferences, they need to integrate it with the current AWS workload in the VPC in which they are required to establish a site-to-site VPN connection.
What needs to be configured outside of the VPC for them to have a successful site-to-site VPN connection?
A . An EIP to the Virtual Private Gateway
B . A dedicated NAT instance in a public subnet
C . An Internet-routable IP address (static) of the customer gateway’s external interface for the on-premises network
D . The main route table in your VPC to route traffic through a NAT instance
Answer: C
Explanation:
By default, instances that you launch into a virtual private cloud (VPC) can’t communicate with your own network. You can enable access to your network from your VPC by attaching a virtual private gateway to the VPC, creating a custom route table, updating your security group rules, and creating an AWS managed VPN connection.
Although the term VPN connection is a general term, in the Amazon VPC documentation, a VPN connection refers to the connection between your VPC and your own network. AWS supports Internet Protocol security (IPsec) VPN connections.
A customer gateway is a physical device or software application on your side of the VPN connection. To create a VPN connection, you must create a customer gateway resource in AWS, which provides information to AWS about your customer gateway device. Next, you have to set up an Internet-routable IP address (static) of the customer gateway’s external interface.
The following diagram illustrates single VPN connections. The VPC has an attached virtual private gateway, and your remote network includes a customer gateway, which you must configure to enable
the VPN connection. You set up the routing so that any traffic from the VPC bound for your network is routed to the virtual private gateway.
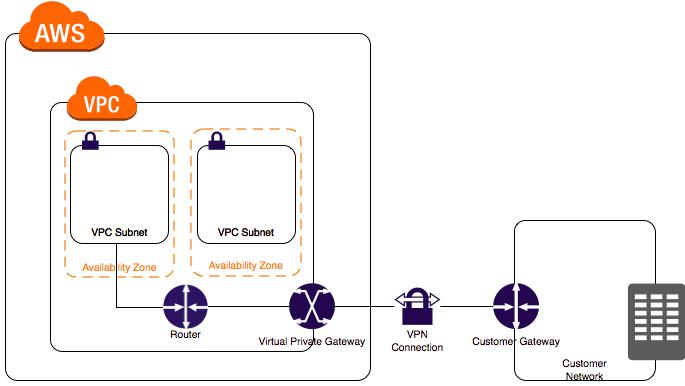
The options that say: A dedicated NAT instance in a public subnet and the main route table in your VPC to route traffic through a NAT instance are incorrect since you don’t need a NAT instance for you to be able to create a VPN connection.
An EIP to the Virtual Private Gateway is incorrect since you do not attach an EIP to a VPG.
References:
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_VPN.html
https://docs.aws.amazon.com/vpc/latest/userguide/SetUpVPNConnections.html
Check out this Amazon VPC Cheat Sheet:
https://tutorialsdojo.com/amazon-vpc/
Latest SAA-C03 Dumps Valid Version with 400 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

