What should you do?
Note This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of Repeated Scenario:
Your network contains an Active Directory domain named contoso.com The functional level of the forest and the domain is Windows Server 2008 R2 All servers in the domain run Windows Server 2016 Standard. The domain contains 300 client computers that run either Windows 8.1 or Windows 10.
The domain contains nine servers that are configured as shown in the following table.
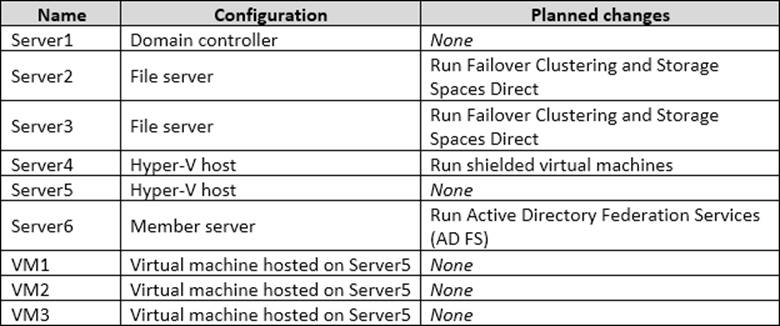
The virtual machines are configured as follows:
• E ach virtual machine has one virtual network adapter
• VM1 and VM2 are part of a Network Load Balancing (NIB) cluster.
• All of the servers on the network can communicate with all of the virtual machines.
End of repeated Scenario.
You need to minimize the likelihood that a virtual machine running malicious code will consume excessive resources on Server5.
What should you do?
A . Configure the virtual machines as shielded virtual machines.
B . Run the Set-VMProcessor cmdlet and specify the CEnableHostResourceProtection Parameter.
C . Run the Set-VMProcessor cmdlet and specify the CMaximumCountPerNumaNode Parameter.
D . Configure VM Network Adapter Isolation.
Answer: B
Latest 70-740 Dumps Valid Version with 334 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

