How should you configure network security?
HOTSPOT
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case.
However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other question on this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next sections of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question on this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Background
General
Trey Research is the global leader in analytical data collection and research. Trey Research houses its servers in a highly secure server environment. The company has continuous monitoring, surveillance, and support to prevent unauthorized access and data security.
The company uses advanced security measures including firewalls, security guards, and surveillance to ensure the continued service and protection of data from natural disaster, intruders, and disruptive events.
Trey Research has recently expanded its operations into the cloud by using Microsoft Azure. The company creates an Azure virtual network and a Virtual Machine (VM) for moving on-premises Subversion repositories to the cloud. Employees access Trey Research applications hosted on-premises and in the cloud by using credentials stored on-premises.
Applications
Trey Research hosts two mobile apps on Azure, DataViewer and DataManager. The company uses Azure-hosted web apps for internal and external users. Federated partners of Trey Research have a single sign-on (SSO) experience with the DataViewer application.
Architecture
You have an Azure Virtual Network (VNET) named TREYRESEARCH_VNET. The VNET includes all hosted VMs. The virtual network includes a subnet Frontend and a subnet named RepoBackend. A resource group has been created to contain the TREYRESEARCH_VNET, DataManager and DataViewer. You manage VMs by using System Center VM Manager (SCVMM). Data for specific high security projects and clients are hosted on-premises. Data for other projects and clients are hosted in the cloud.
Azure Administration
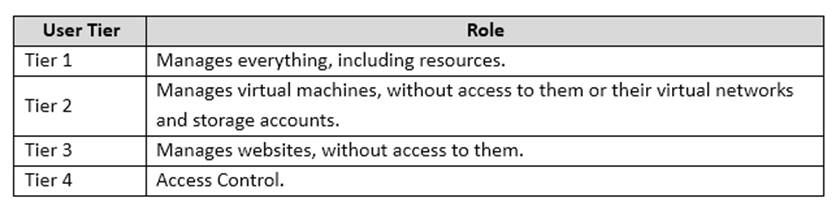
DataManager
The DataManager app connects to a RESTful service. It allows users to retrieve, update, and delete Trey Research data.
Requirements
General
You have the following general requirements:
Disaster recovery
Disaster recovery and business continuity plans must use a single, integrated service that supports the following features:
Security
You identify the following security requirements:
Subversion server
Subversion Server Sheet
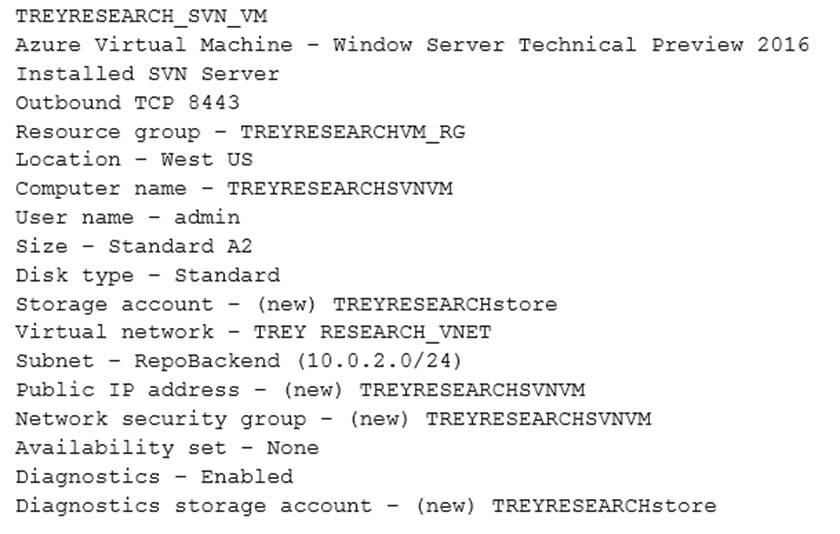
You need to enforce the security requirements for all subversion servers.
How should you configure network security? To answer, select the appropriate answer from each list in the answer area.
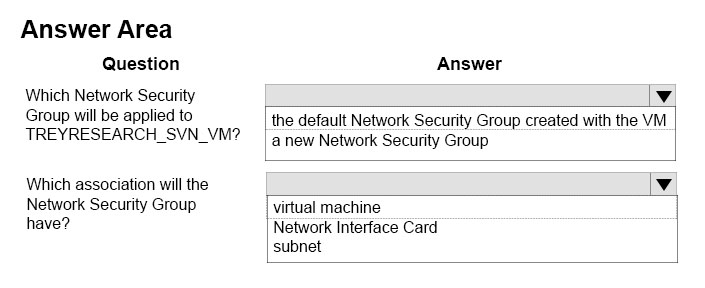
Answer: 
Explanation:
/ You host multiple subversion (SVN) repositories in the RepoBackend subnet. The SVN servers on this subnet must use inbound and outbound TCP at port 8443.
Latest 70-535 Dumps Valid Version with 458 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

