- All Exams Instant Download
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
Device event logs sources from MDM software as follows:
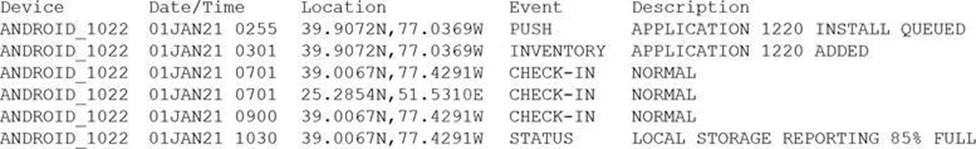
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
A . Malicious installation of an application; change the MDM configuration to remove application ID 1220.
B . Resource leak; recover the device for analysis and clean up the local storage.
C . Impossible travel; disable the device’s account and access while investigating.
D . Falsified status reporting; remotely wipe the device.
Answer: C
Explanation:
The device event logs show that the device was in two different locations (New York and London) within a short time span (one hour), which indicates impossible travel. This could be a sign of a compromised device or account. The best response action is to disable the device’s account and access while investigating the incident. Malicious installation of an application is not evident from the logs, nor is resource leak or falsified status reporting.
Verified Reference:
https://www.comptia.org/blog/what-is-impossible-travel https://partners.comptia.org/docs/default-source/resources/casp-content-guide
Latest CAS-004 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

