Based on the output above, from which of the following process IDs can the analyst begin an investigation?
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.
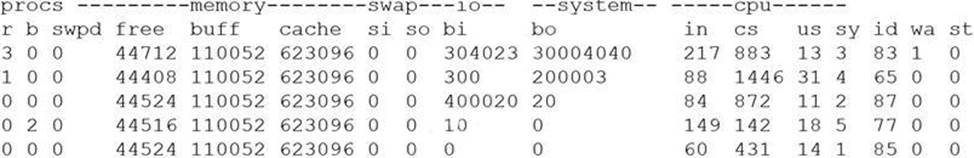
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
A . 65
B . 77
C . 83
D . 87
Answer: D
Explanation:
The process ID 87 can be the starting point for an investigation of a possible buffer overflow attack, as it shows a high percentage of CPU utilization (99.7%) and a suspicious command name (graphic.linux_randomization.prg). A buffer overflow attack is a type of attack that exploits a vulnerability in an application or system that allows an attacker to write data beyond the allocated buffer size, potentially overwriting memory segments and executing malicious code. A high CPU utilization could indicate that the process is performing intensive or abnormal operations, such as a buffer overflow attack. A suspicious command name could indicate that the process is trying to disguise itself or evade detection, such as by mimicking a legitimate program or using random characters. The other process IDs do not show signs of a buffer overflow attack, as they have low CPU utilization and normal command names.
Verified Reference:
https://www.comptia.org/blog/what-is-buffer-overflow
https://partners.comptia.org/docs/default-source/resources/casp-content-guide
Latest CAS-004 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

