What should you do?
Topic 2, Fabrikam Inc.
Fabrikam Inc. runs an online reservation service that allows agents to manage online registrations for various hotels, vacation rentals, and customers.
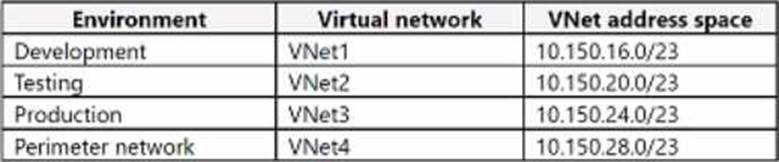
The company has on-premises infrastructure and services that are hosted in Azure. The on-premises infrastructure includes servers that run Active Directory Domain Services (AD DS). Azure services include virtual machines (VMs) that are in one subscription and the following environments: development, testing, and production. Each environment is located in a different virtual network (VNet).
The company has a perimeter network that supports connections to the internet. The perimeter network is also hosted in a separate VNet All of the VNets are connected by using virtual network peering.
The company’s subscription contains the following Azure virtual machines (VMs):
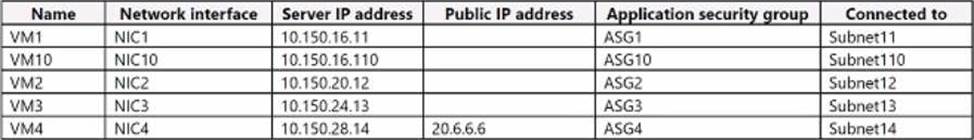
The Web Server (IIS) role is installed on VM4 The operating system firewall for each VM allows inbound ping requests.
The company’s subscription includes the following network security groups (NSGs):
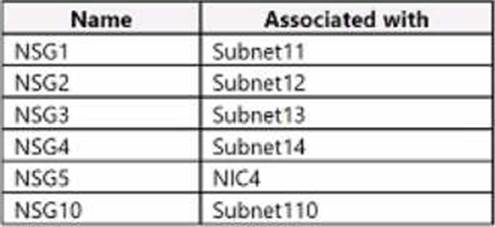
NSG1, NSG2. NSG3, and NSG5 use the default inbound security rules. NSG4. NSG5. and NSG10 use the default outbound security rules.
NSG4 has the following inbound security rule:
![]()
NSG10 has the following inbound security rules:

Network Policy Server (NPS) is installed on an on-premises server named SRV2. The NPS extension for Azure AD multi-factor authentication (MFA) is configured on the server as well.
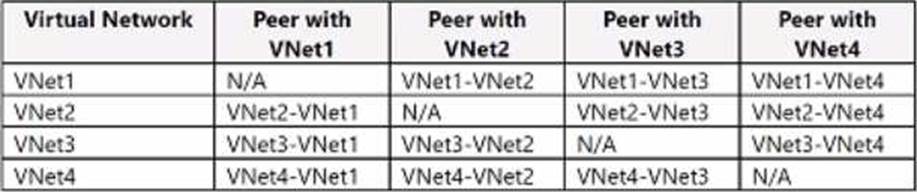
The virtual network peering connections are in the following table.
You provision a virtual network gateway named VNetGW in the perimeter network. The virtual network gateway uses SKU VpnGw1 and the public IP address 16.4.4.4.
The virtual network gateway will provide:
• Network routing to customer data centers using site-to-site VPN connections.
• Network routing to Azure for the scheduling agents and sales employees using a point-to-site VPN connection.
The company’s site-to-site VPN connections with customers are shown in the following table.
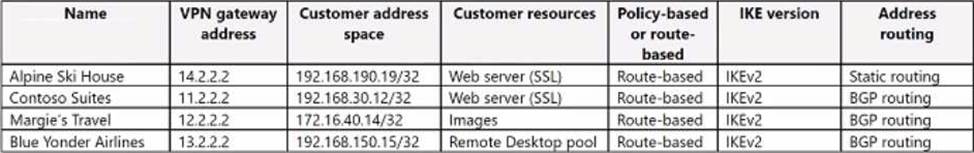
The point-to-site VPN is configured as shown in the following table;
![]()
The company’s user and group memberships are shown in the following table:
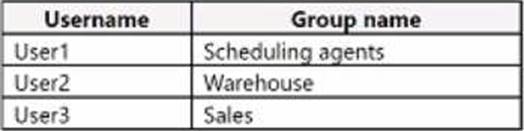
The scheduling agents, warehouse, and sales groups are members of the self-service password reset (SSPR) group named SSPR-group.
Azure AD Connect is installed on an on-premises server named SRV1. In addition;
• The server uses a pass-through authentication agent.
• The SSPR feature is enabled
• The SSPR feature is applied only to a group named SSPR-group
• The scheduling agents’ internet connectivity must be blocked when connected to the point-to-site VPN.
• Sales employees must use the default VPN client on MacOS computers to connect to Azure.
• Azure AD Connect must synchronize all user accounts from AD DS to Azure AD.
• Pass-through authentication is required for all users.
• Azure AD multi-factor authentication (MFA) is requited for all users.
• All admin user accounts must be in an organizational unit (OU) named Admins.
VM3
Users report issues connecting from VM3 to resources at Margie’s Travel. The administrator for Margie’s Travel has verified that their VPN gateway is working correctly. You must verify whether the Fabrikam virtual network gateway is available.
VM10
All ping tests bust be performed by using the ICMP protocol. You are unable to ping VM10 from VM1 Alpine Ski House
You discover during testing that scheduling agents are experiencing latency when accessing resources at the Alpine Ski House. You suspect that the issue is related to
ICMP latency.
Contoso Suites
You receive reports that VM1 is unable to access resources at Contoso Suites Blue Yonder Airlines
The administrator of a partner company named Blue Yonder Airlines reports VPN disconnections and IPsec failure to connect errors.
Other resource issues
• MFA requests on SRV2 are failing with a security token error.
• You are unable to ping VM10 from VM1.
Admin1
You receive the following error on SRV1 only when trying to synchronize an administrator named Admin1: 8344 insufficient access rights to perform the operation
Admin2
An administrator named Admin2 reports they cannot connect to the web server public IP address on VM4 from VM2.
Agent 1
A scheduling agent named Agent1 reports issues authenticating to Azure AD.
Used 1
A scheduling agent named User1 reports that they can access the internet when connected to the point-to-site VPN.
User2
A user named User2 reports the following error when registering for SSPR: Your administrator has
not enabled you to use this feature.
Sales team
Sales team employees report that they are unable to connect by using point-to-site VPN.
You need to resolve the issue with Admin1.
What should you do?
A . Configure Azure AD Connect filtering to include the Admins organizational unit.
B . Reset the Azure AD Connect service account password in AD DS.
C . Enable security inheritance in Active Directory Domain Services (AD DS).
D . Start a full import in Azure AD Connect.
Answer: C
Explanation:
The error 8344 insufficient access rights to perform the operation indicates that the Azure AD Connect service account does not have the required permissions to synchronize the Admin1 account. This could be because the Admin1 account is in an organizational unit (OU) that has security inheritance disabled, which prevents the service account from inheriting the necessary permissions from the parent OU. To resolve this issue, you should enable security inheritance in AD DS for the OU that contains the Admin1 account. This will allow the service account to synchronize the Admin1 account to Azure AD. Alternatively, you could also grant the service account explicit permissions on the Admin1 account, but this would be more tedious and less scalable than enabling security inheritance.
Latest AZ-720 Dumps Valid Version with 81 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

