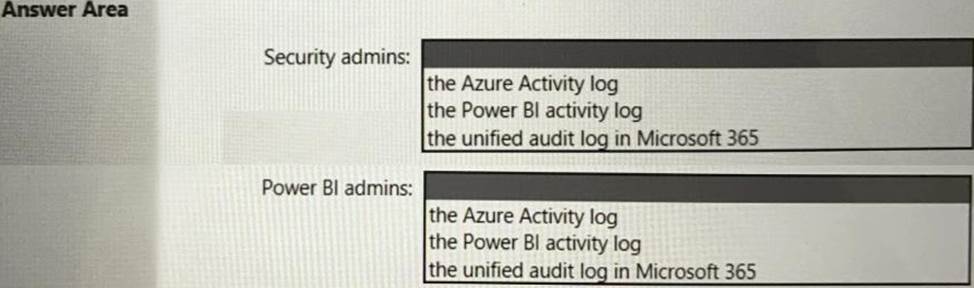
Which log should you include in the recommendation for each group?
HOTSPOT
You need to recommend an automated solution to monitor Power Bl user activity.
The solution must meet the following requirements:
• Security admins must identify when users export reports from Power Bl within five days of a new sensitivity label being applied to the artifacts in Power Bl.
• Power Bl admins must identify updates or changes to the Power Bl capacity.
• The principle of least privilege must be used.
Which log should you include in the recommendation for each group? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Answer: 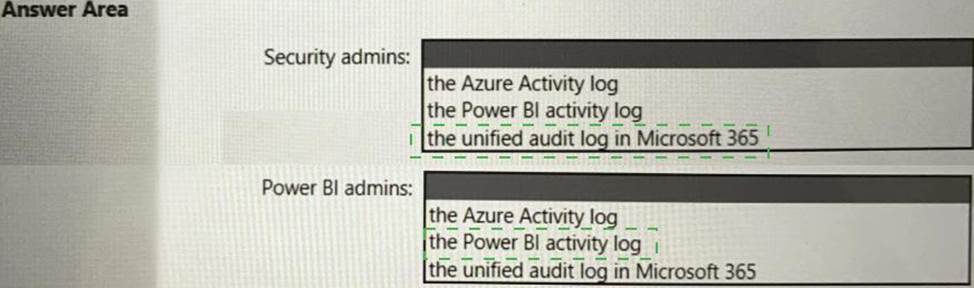
Explanation:
Box 1: the unified audit log in Microsoft 365
Security admins must identify when users export reports from Power BI within five days of a new sensitivity label being applied to the artifacts in Power BI.
Use the audit log
If your task is to track user activities across Power BI and Microsoft 365, you work with auditing in Microsoft 365 compliance or use PowerShell. Auditing relies on functionality in Exchange Online, which automatically supports Power BI.
You can filter the audit data by date range, user, dashboard, report, dataset, and activity type. You can also download the activities in a csv (comma-separated value) file to analyze offline.
Box 2: Power BI activity log
Power BI admins must identify updates or changes to the Power BI capacity.
Use the activity log
Power BI administrators can analyze usage for all Power BI resources at the tenant level by using custom reports that are based on the Power BI activity log.
Reference: https://docs.microsoft.com/en-us/power-bi/admin/service-admin-auditing
Latest DP-500 Dumps Valid Version with 83 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

