- All Exams Instant Download
What are the correct commands to ensure that no rogue DHCP server will impact the network?
A customer has a large number of food-producing machines
* All machines are connected via Aruba CX6200 switches in VLANs 100.110. and 120
* Several external technicians are maintaining this special equipment
What are the correct commands to ensure that no rogue DHCP server will impact the network?
A)
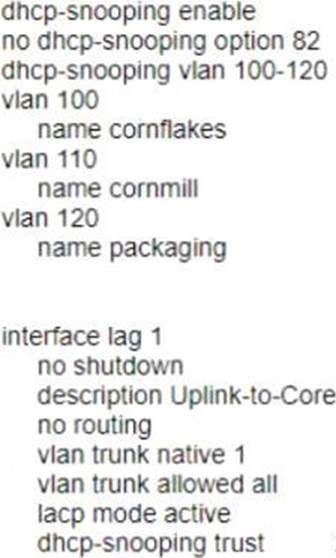
B)
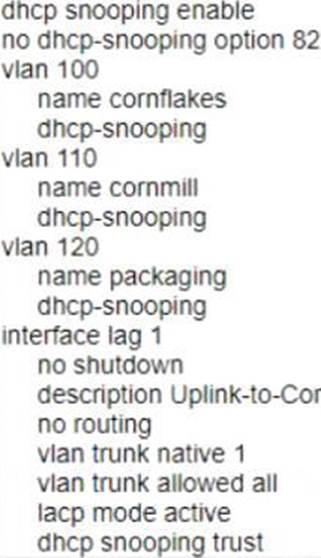
C)
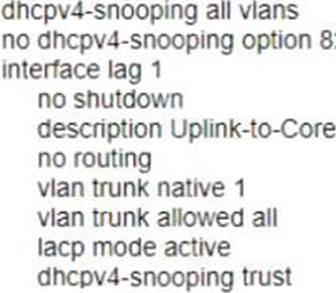
D)
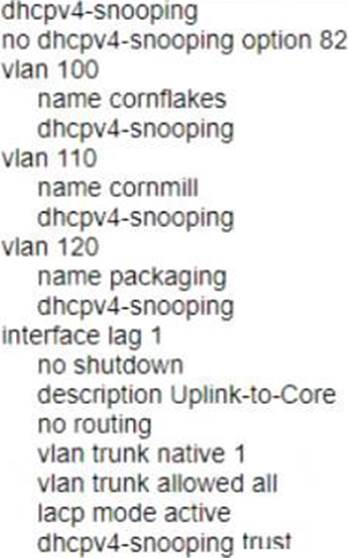
A . Option A
B. Option B
C. Option C
D. Option D
Answer: A
Explanation:
Option A shows the correct commands to ensure that no rogue DHCP server will impact the network.
The commands include the following steps:
* Enable DHCP snooping on the switch. DHCP snooping is a feature that prevents rogue DHCP servers from offering IP addresses to clients by filtering DHCP messages based on trusted and untrusted ports1.
* Configure VLANs 100, 110, and 120 as DHCP snooping VLANs. This means that DHCP snooping will be applied to these VLANs and any untrusted DHCP messages received on these VLANs will be dropped1.
* Configure LAG 1 as a trusted port for DHCP snooping. This means that any DHCP messages received on LAG 1 will be allowed and not filtered by DHCP snooping. LAG 1 is assumed to be connected to a legitimate DHCP server or a router that relays DHCP requests to a legitimate DHCP server1.
Option B is incorrect because it does not enable DHCP snooping on the switch or configure VLANs 100, 110, and 120 as DHCP snooping VLANs. Option C is incorrect because it does not configure LAG 1 as a trusted port for DHCP snooping. Option D is incorrect because it does not enable DHCP snooping on the switch or configure LAG 1 as a trusted port for DHCP snooping.
References: 1 https://techhub.hpe.com/eginfolib/Aruba/OS-CX_10.04/5200-6692/GUID-BD3E0A5F-FE4C-4B9B-BE1D-FE7
Latest HPE7-A01 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

