HP HPE6-A81 Aruba Certified ClearPass Expert Written Exam Online Training
HP HPE6-A81 Online Training
The questions for HPE6-A81 were last updated at May 08,2024.
- Exam Code: HPE6-A81
- Exam Name: Aruba Certified ClearPass Expert Written Exam
- Certification Provider: HP
- Latest update: May 08,2024
Refer to the exhibit.
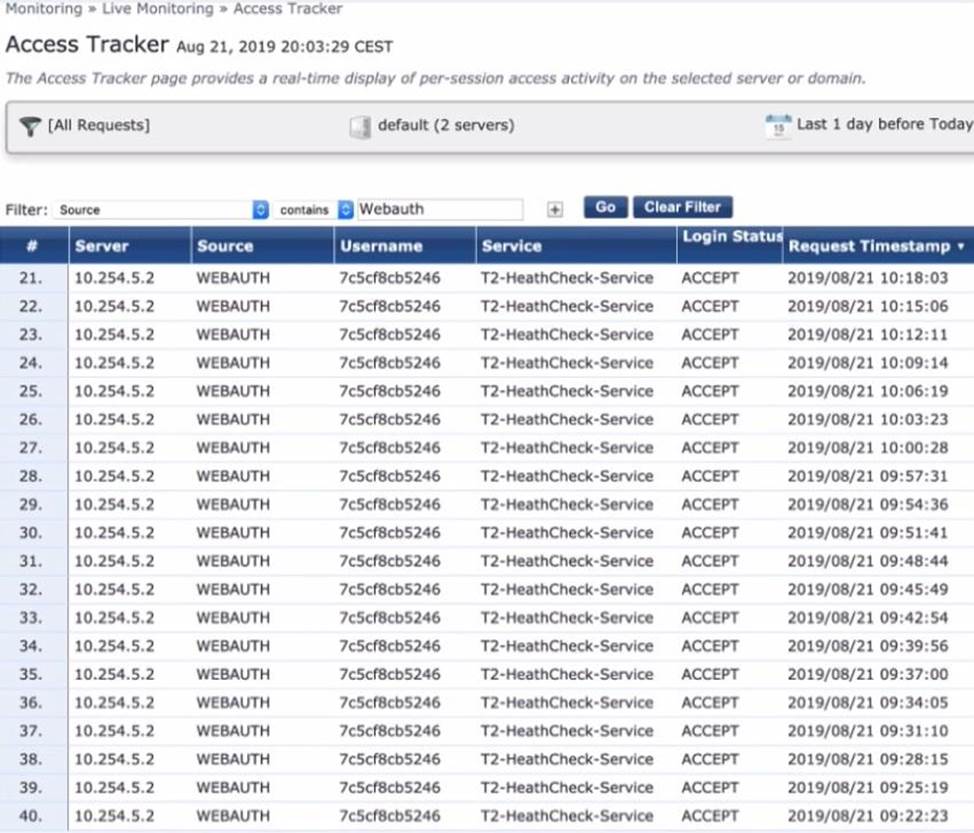
A customer has just configured a Posture Policy and the T 2 -Health check Service. Next they installed the OnGuard Agent on a test client connected to the Secure_Employee SSID. When they check Access Tracker they see many WEBAUTH requests are being triggered.
What could be the reason?
- A . The OnGuard Agent trigger the events based on changing the Health Status.
- B . The OnGuard Agent is connecting to the Data Port interface on ClearPass.
- C . TCP port 6658 is not allowed between the client and the ClearPass server.
- D . OnGuard Web-Based Health Check interval has been configured to three minutes.
Your customer has read about a feature in OnGuard for OnGuard Persistent Agent and Agentless OnGuard that can display a new Posture Results web page to notify that and users with posture results for unhealthy clients after the health check is done.
Where do you configure this option?
- A . Policy Manager > Configuration > Enforcement > Profiles > Add a new profiles with Agent Enforcement as the template, and on the Attributes tab add the new Show Posture Results in Guest Page attribute and set the value for the attribute to true.
- B . Policy Manager > Configuration > Enforcement > Profiles > Add new profile with Aruba Radius Enforcement as the template, and on the Attributes tab add the Aruba-User-Role configured with the captive portal profile mapped with default Posture Check web page URL.
- C . Policy Manager > Configuration > Services > Edit the Web-base Health Check Only service, and on the posture tab under Remediation URL add the default Quarantined Blocked web page URL and complete the service configuration by hitting save.
- D . Policy Manager > Configuration > Services > Edit the Web-base Health Check Only service, and on the posture tab enable the checkbox for the new option Show Posture Results in Guest Page and complete the service configuration by hitting save.
A customer would like to allow only the AD users with the "Manager" title from the "HO" location to Onboard their personal devices. Any other AD users should not be authorized to pass beyond the initial device provisioning page .
Which Onboard service will you use to implement this requirement?
- A . Onboard Authorization service
- B . Onboard Pre-Auth service
- C . Onboard Provisioning service
- D . Onboard CP login service
What configuration steps should you follow to add terms and conditions page on Guest seIf-registration for CPPM? (Select two).
- A . Edit the creetoraccepiterms form field in register page and change HTML section by pointing the hyperlink to the HTML file uploaded
- B . Edit the accept_terms form field in receipt page and change HTML section by pointing the hyper link to the HTML file uploaded m Guest Manager
- C . Create an HTML page with custom terms and condition and upload it to public files
under Clearpass Guest -> configuration -> content manager - D . Edit the creatoracceprterms form field in receipt page and change HTML section by pointing the hyperlink to the HTML file uploaded
- E . Create an HTML page with custom terms and condition and upload it to private files under Clearpass Guest -> configuration -> content manager
Refer to the exhibit.
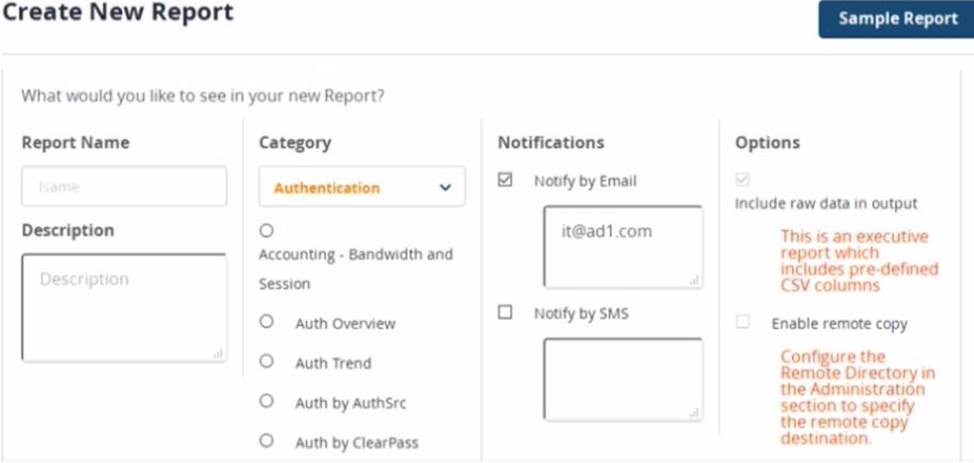
When creating a new report, there is in option to send report Notifications by Email Where is the email server configured?
- A . In the ClearPass Policy Manager Messaging Setup under Administration.
- B . In the Insight report on the next screen of the report definition
- C . In the Insight Reports Interface under Administration on the sidebar menu
- D . In the ClearPass Policy Manager Endpoint Context Servers under Administration.
Refer to the exhibit.
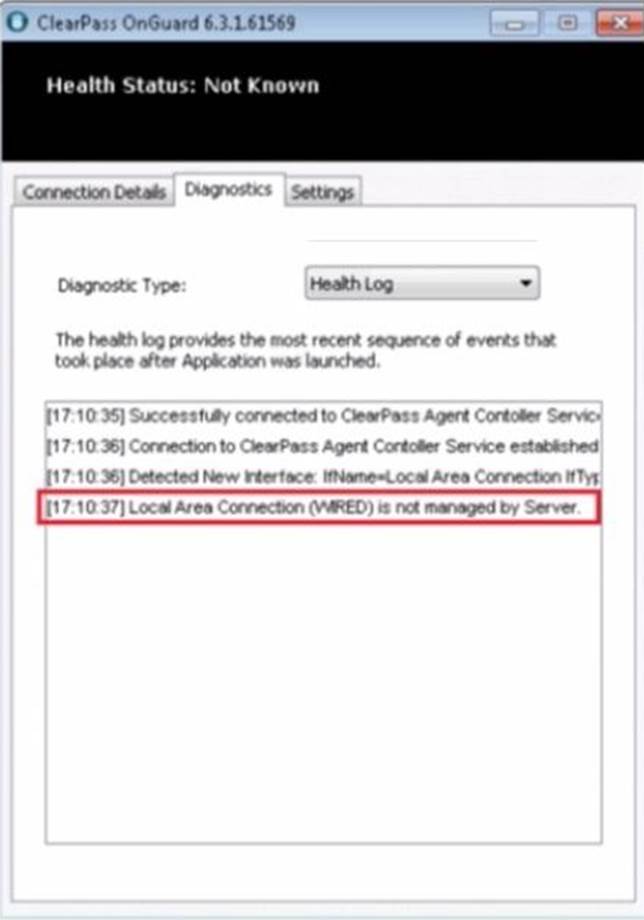
A customer it troubleshooting a client not getting the SHV posture updated and the OnGuard agent shows the Health Status Not Known .
What could the user do to update the health status?
- A . connect using an interface that is configured as Managed Interface
- B . reinstall the OnGuard agent from the Wired interface
- C . change the Policy Manager Zone mapping and add the WIRED interface range
- D . modify the agent.conf file and add the WIRED interface to it
A customer has acquired another company that has its own Active Directory infrastructure. The 802 1X PEAP authentication works with the customer’s original Active Directory servers but the customer would like to authenticate users from the acquired company as well.
What steps are required, in regards to the Authentication Sources, in order to support this request? (Select two.)
- A . Create a new Authentication Source, type Active Directory.
- B . Create a new Authentication Source, type Generic LDAP.
- C . Add the new AD server(s) as backup into the existing Authentication Source.
- D . There is no need to join ClearPass to the new AD domain.
- E . Join the ClearPass server(s) to the new AD domain.
You have designed a ClearPass solution for an Information Technology Business Park with 50,377 concurrent sessions including the visitors. The deployment includes eight ClearPass servers handling RADIUS authentication. Guest Self-Registration. Onboard and OnGuard. CPPM1 is acting as Publisher. CPPM2 to CPPM8 are added as subscriber nodes CPPM4 is the designated Standby Publisher. Servers CPPM2 and CPPM3 will be handling the Guest and Onboard HTTPS traffic. On a few devices, Corporate users will perform username and password based authentication with Active Directory accounts and on few devices, they will be using private CA signed TLS certificates to do the authentication The customer has three Active Directories (AD1, AD2 and A03) part of Multi-Domain Forest. To provide authentication redundancy, the customer has configured multiple Virtual IP settings between ClearPass servers in a cluster.
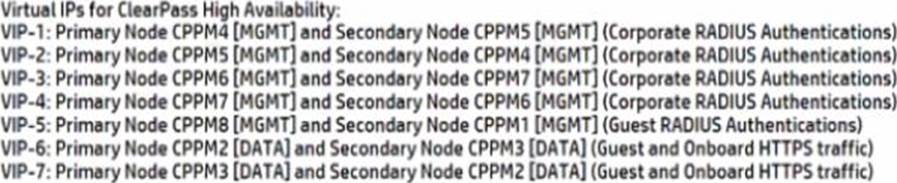
On all the Network Access Devices (NAD), the primary authentication server is configured as the VIP IP address and the secondary authentication server rs configured as CPPM1 MGMT IP address.
Based on the information provided, which ClearPass nodes will you join to the AD domain
- A . Join CPPM1. CPPM4 to CPPM7 servers to the AD root domain
- B . Join CPPM2 to CPPM7 ClearPass servers to the AD root domain.
- C . Join all the eight ClearPass servers to AD1, AD2 and AD3 domains.
- D . Join CPPM1. CPPM4 to CPPM8 to the AD1. AD2 and AD3 domains.
Refer to the exhibit.
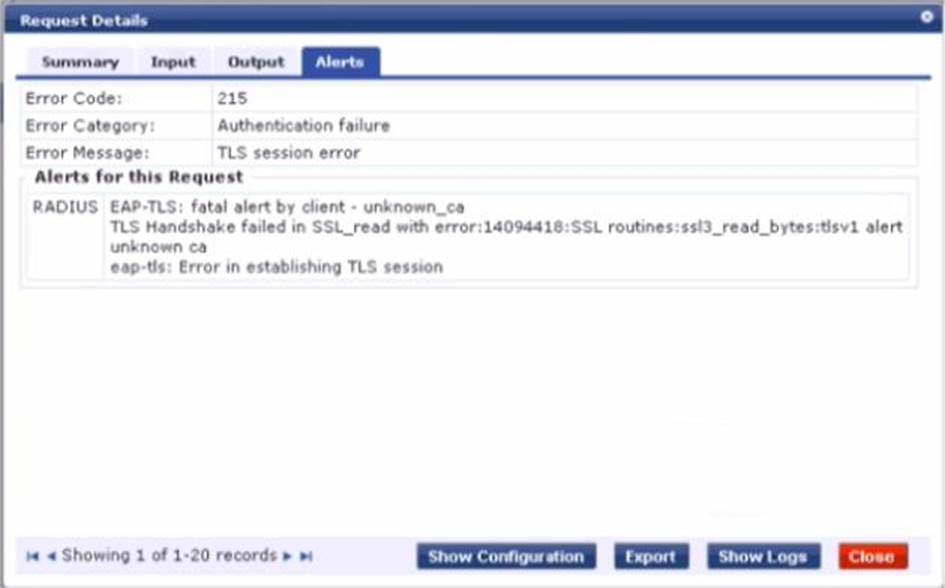
A customer has configured Onboard in a cluster with two nodes. All devices were onboarded in the network through node1 but those clients fail to authenticate through node2 with the error shown.
What steps would you suggest to make provisioning and authentication work across the entire cluster? (Select three)
- A . Configure the Network Settings in Onboard to trust the Policy Manager EAP certificate.
- B . Have all of the BYOO clients disconnect and reconnect to the network.
- C . Configure the Onboard Root CA to trust the Policy Manager EAP certificate root.
- D . Make sure that the EAP certificates on both nodes are issued by one common root Certificate Authority (CA).
The customer has a 19.940 loT devices connected to the network and would like to use Allow All Mac Auth to authenticate the users and enforce the action based on the condition defined with the fingerprint details of the device .
Which Authorization source would you use to decide the access of the devices?
- A . Clear Pass Profiler Database
- B . Endpoint Database
- C . Local User Database
- D . Guest Device Database
Latest HPE6-A81 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

