Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR) Online Training
Cisco 350-701 Online Training
The questions for 350-701 were last updated at Jan 12,2026.
- Exam Code: 350-701
- Exam Name: Implementing and Operating Cisco Security Core Technologies (SCOR)
- Certification Provider: Cisco
- Latest update: Jan 12,2026
How does Cisco Stealthwatch Cloud provide security for cloud environments?
- A . It delivers visibility and threat detection.
- B . It prevents exfiltration of sensitive data.
- C . It assigns Internet-based DNS protection for clients and servers.
- D . It facilitates secure connectivity between public and private networks.
Which VPN technology can support a multivendor environment and secure traffic between sites?
- A . SSL VPN
- B . GET VPN
- C . FlexVPN
- D . DMVPN
What is a characteristic of Firepower NGIPS inline deployment mode?
- A . ASA with Firepower module cannot be deployed.
- B . It cannot take actions such as blocking traffic.
- C . It is out-of-band from traffic.
- D . It must have inline interface pairs configured.
A malicious user gained network access by spoofing printer connections that were authorized using MAB on four different switch ports at the same time.
What two catalyst switch security features will prevent further violations? (Choose two)
- A . DHCP Snooping
- B . 802.1AE MacSec
- C . Port security
- D . IP Device track
- E . Dynamic ARP inspection
- F . Private VLANs
Refer to the exhibit.
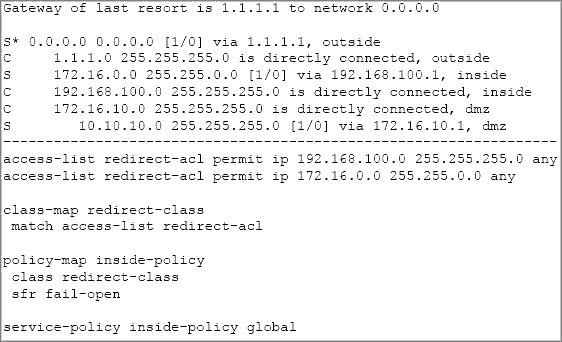
What is a result of the configuration?
- A . Traffic from the DMZ network is redirected
- B . Traffic from the inside network is redirected
- C . All TCP traffic is redirected
- D . Traffic from the inside and DMZ networks is redirected
Which compliance status is shown when a configured posture policy requirement is not met?
- A . compliant
- B . unknown
- C . authorized
- D . noncompliant
Which two preventive measures are used to control cross-site scripting? (Choose two)
- A . Enable client-side scripts on a per-domain basis.
- B . Incorporate contextual output encoding/escaping.
- C . Disable cookie inspection in the HTML inspection engine.
- D . Run untrusted HTML input through an HTML sanitization engine.
- E . Same Site cookie attribute should not be used.
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
- A . biometric factor
- B . time factor
- C . confidentiality factor
- D . knowledge factor
- E . encryption factor
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two)
- A . Patch for cross-site scripting.
- B . Perform backups to the private cloud.
- C . Protect against input validation and character escapes in the endpoint.
- D . Install a spam and virus email filter.
- E . Protect systems with an up-to-date antimalware program
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
- A . NetFlow
- B . desktop client
- C . ASDM
- D . API
Latest 350-701 Dumps Valid Version with 327 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

