- All Exams Instant Download
You have a Microsoft 365 E5 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com
HOTSPOT
You have a Microsoft 365 E5 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
Azure AD Identity Protection alerts for contoso.com are configured as shown in the following exhibit.
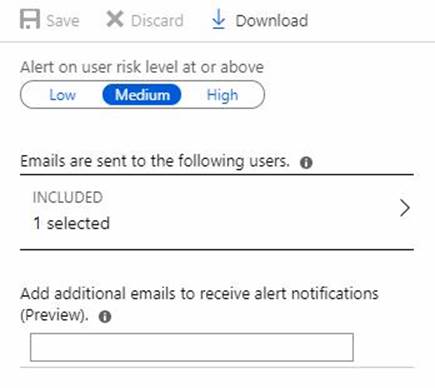
A user named User1 is configured to receive alerts from Azure AD Identity Protection.
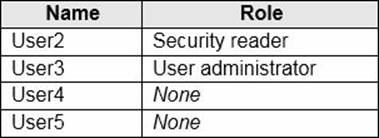
You create users in contoso.com as shown in the following table.
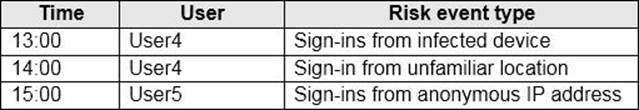
The users perform the sign-ins shown in the following table.
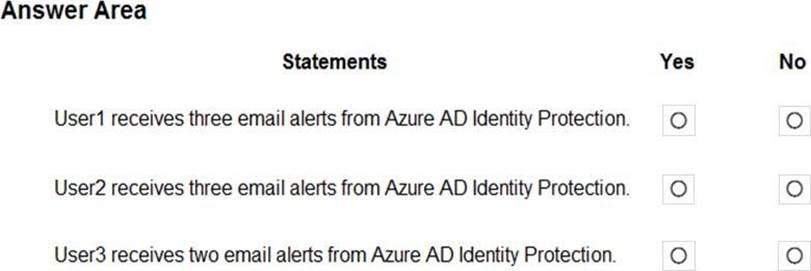
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Answer: 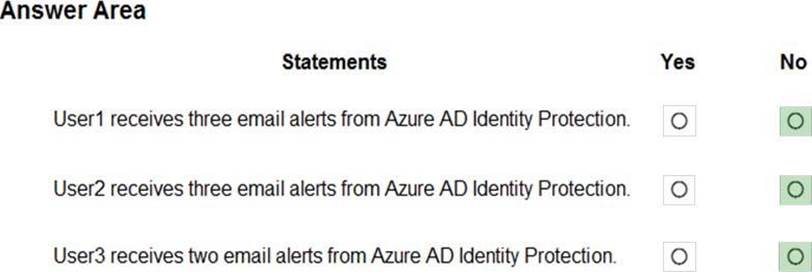
Explanation:
Box 1: No
User1 will receive the two alerts classified as medium or higher. Sign-ins from infected device is classified as low. This risk detection identifies IP addresses, not user devices. If several devices are behind a single IP address, and only some are controlled by a bot network, sign-ins from other devices my trigger this event unnecessarily, which is why this risk detection is classified as Low.
Box 2: No
User2 will receive the two alerts classified as medium or higher.
Email alerts are sent to all global admins, security admins and security readers Sign-ins from infected device is classified as low. This risk detection identifies IP addresses, not user devices. If several devices are behind a single IP address, and only some are controlled by a bot network, sign-ins from other devices my trigger this event unnecessarily, which is why this risk detection is classified as Low.
Box 3: No
User3 will not receive alters.
Email alerts are sent to all global admins, security admins and security readers.
Latest MS-500 Dumps Valid Version with 193 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

