- All Exams Instant Download
Which of the following is the user attempting to do based on the log entries?
A security analyst notices the following proxy log entries:
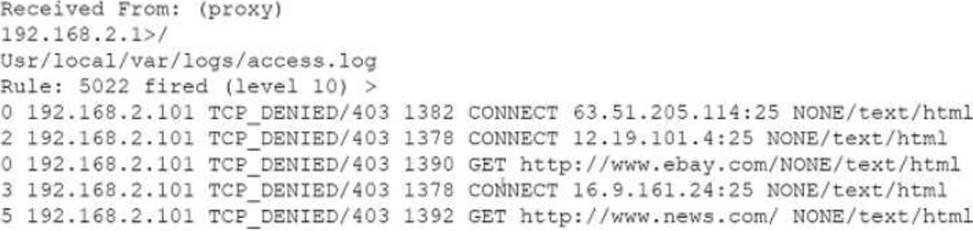
Which of the following is the user attempting to do based on the log entries?
A . Use a DoS attack on external hosts.
B . Exfiltrate data.
C . Scan the network.
D . Relay email.
Answer: D
Explanation:
Scanning the network is what the user is attempting to do based on the log entries. The log entries show that the user is sending ping requests to various IP addresses on different ports using a proxy server. Ping requests are a common network diagnostic tool that can be used to test network connectivity and latency by sending packets of data and measuring their response time. However, ping requests can also be used by attackers to scan the network and discover active hosts, open ports, or potential vulnerabilities.
Latest CS0-003 Dumps Valid Version with 128 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

