What should you do?
HOTSPOT
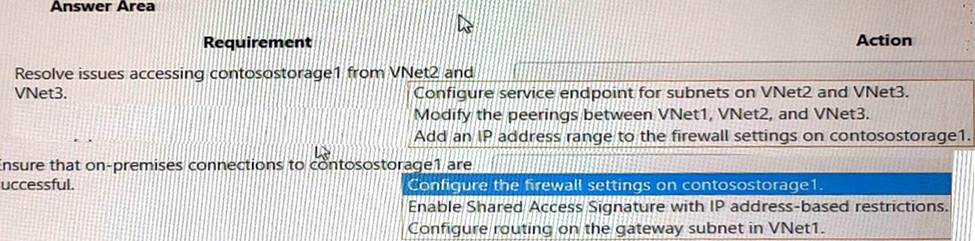
You need to troubleshoot and resolve issues reported for contosostorage1.
What should you do? To answer, select the appropriate option in the answer area. NOTE: Each correct selection is worth one point.
Answer: 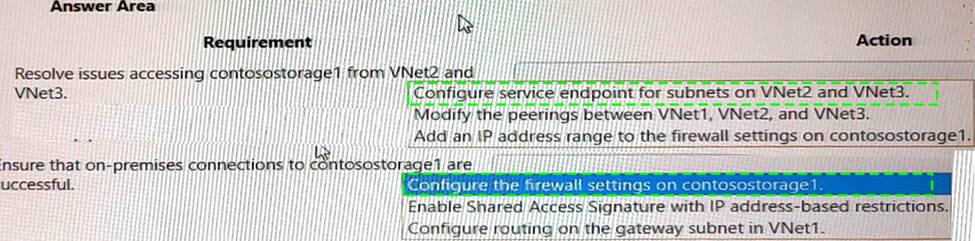
Explanation:
Box 1: Configure service endpoint for subnet on VNet2 and VNet3.
This is what you should do to resolve issues accessing contosostorage1 from VNet2 and VNet3. A service endpoint is a feature that enables you to secure your Azure Storage account to a specific virtual network subnet1.
As mentioned in the scenario, contosostorage1 is a storage account that has firewall and virtual network settings enabled. This means that only requests from allowed networks can access the storage account2. By default, storage accounts accept connections from clients on any network, but you can configure firewall rules to allow or deny access based on the source IP address or virtual network subnet2.
In this scenario, you want to allow access to contosostorage1 from VNet2 and VNet3, which are peered with VNet1. To do this, you need to configure service endpoints for the subnets on VNet2 and VNet3 that need to access the storage account1. A service endpoint is a feature that enables you to secure your Azure Storage account to a specific virtual network subnet1. When you enable a service endpoint for a subnet, you can then grant access to the storage account only from that subnet1. This way, you can restrict access to your storage account and improve network performance by routing traffic through an optimal path.
To configure service endpoints for a subnet using the Azure portal, follow these steps1:
✑ In the Azure portal, navigate to the Virtual Network resource.
✑ Select Subnets, then select the subnet that needs to access the storage account.
✑ Under Service endpoints, select Microsoft.Storage from the drop-down list.
✑ Select Save to apply the changes.
To configure service endpoints for a subnet using the Azure CLI or PowerShell, see Enable a service endpoint.
After configuring service endpoints for the subnets on VNet2 and VNet3, you also need to grant access to contosostorage1 from those subnets. To do this, you need to modify the firewall rules on the storage account2.
To modify the firewall rules on the storage account using the Azure portal, follow these steps2:
✑ In the Azure portal, navigate to the Storage Account resource.
✑ Select Firewalls and virtual networks under Settings.
✑ Under Allow access from selected networks, select Add existing virtual network.
✑ Select the virtual network and subnet that have service endpoints enabled for Microsoft.Storage.
✑ Select Add to save the changes.
To modify the firewall rules on the storage account using the Azure CLI or PowerShell, see Configure Azure Storage firewalls and virtual networks.
Box 2: Configure the firewall settings on contosostorage1.
The issue reported is that on-premises connections to contosostorage1 are unsuccessful. The main reason for this could be that the firewall settings on the storage account are blocking the connections. By configuring the firewall settings on contosostorage1 to allow the on-premises IP addresses, you can ensure that the on-premises connections are successful.
As mentioned in the scenario, contosostorage1 is a storage account that has firewall and virtual network settings enabled. This means that only requests from allowed networks can access the storage account1. By default, storage accounts accept connections from clients on any network, but you can configure firewall rules to allow or deny access based on the source IP address or virtual network subnet1.
In this scenario, you want to allow access to contosostorage1 from the on-premises environment, which is connected to Azure using a Site-to-Site VPN connection. A Site-to-Site VPN connection lets you create a secure connection between your on-premises network and an Azure virtual network over an IPsec/IKE VPN tunnel2. To allow access to contosostorage1 from the on-premises environment, you need to configure the firewall settings on contosostorage1 to include the public IP address of your VPN device or gateway3.
To configure the firewall settings on contosostorage1 using the Azure portal, follow these steps1:
✑ In the Azure portal, navigate to the Storage Account resource.
✑ Select Firewalls and virtual networks under Settings.
✑ Under Allow access from selected networks, select Add existing virtual network.
✑ Select VNet1 and the subnet that has service endpoints enabled for Microsoft.Storage.
✑ Under Firewall, enter the public IP address of your VPN device or gateway under Address Range.
✑ Select Save to apply the changes.
To configure the firewall settings on contosostorage1 using the Azure CLI or PowerShell, see Configure Azure Storage firewalls and virtual networks.
Latest AZ-720 Dumps Valid Version with 81 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

