How should you configure the system?
HOTSPOT
You need to troubleshoot the sales department issues.
How should you configure the system? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
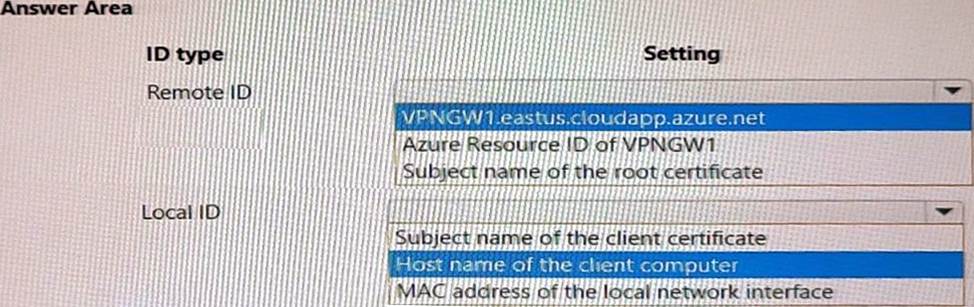
Answer: 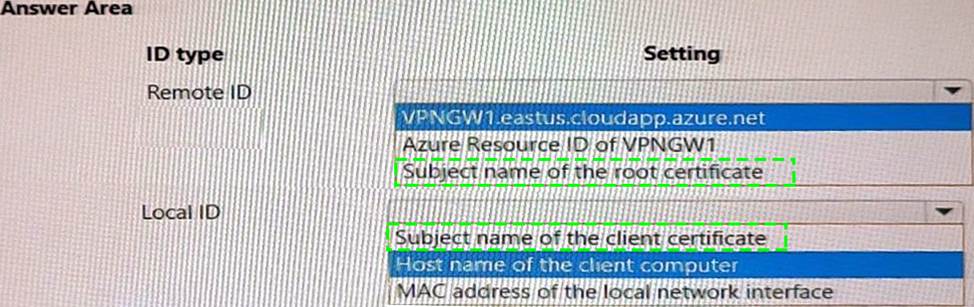
Explanation:
Box 1: Subject name of the root certificate.
This is the value that should be configured as the system Remote ID for the VPN client on the sales department devices. The system Remote ID is used to identify the VPN server that the client is connecting to, and it must match the value that is configured on the VPN gateway in Azure. For Azure VPN Gateway, the system Remote ID is the subject name of the root certificate that is used for authentication1. Therefore, option C is correct. A detailed explanation with references is as follows:
As mentioned in the scenario, the sales department devices are using Point-to-Site VPN connections to access Azure resources. A Point-to-Site VPN connection lets you create a secure connection to your virtual network from an individual client computer2. To configure a Point-to-Site VPN connection, you need to create a virtual network gateway of type VPN in Azure, and then install a VPN client on each device that needs to connect2. The VPN client configuration includes several settings, such as the VPN server address, the tunnel type, and the authentication method. One of these settings is the system Remote ID, which is used to identify the VPN server that the client is connecting to1. The system Remote ID must match the value that is configured on the VPN gateway in Azure, otherwise the connection will fail.
For Azure VPN Gateway, there are three authentication methods available for Point-to-Site
VPN connections: certificate-based authentication, OpenVPN with Azure AD authentication, and OpenVPN with certificate-based authentication2. For certificate-based authentication, which is used in this scenario, the system Remote ID is the subject name of the root certificate that is used for authentication1. The root certificate is uploaded to Azure when creating a Point-to-Site VPN connection, and it must be installed on each device that needs to connect2. The subject name of the root certificate can be obtained by using PowerShell or OpenSSL commands1. For example, using PowerShell:
$cert = Get-ChildItem -Path Cert:CurrentUserMy | Where-Object {$_.Subject -like “ContosoRootCert”} $cert.Subject
The output of this command will show the subject name of the root certificate that matches ContosoRootCert. This value should be configured as the system Remote ID for the VPN client on each device.
Box 2: Subject name of the client certificate
In the provided scenario, the sales department is using a VPN to connect to the corporate network, and the VPN server is configured to use certificate-based authentication. To troubleshoot the sales department issues, you should configure the system Local ID to use the subject name of the client certificate. The subject name of a client certificate uniquely identifies the client and is used during the certificate-based authentication process. This allows the VPN server to verify the client’s identity and grant access to the corporate network.
This is the value that should be configured as the system Local ID for the VPN client on the sales department devices. The system Local ID is used to identify the VPN client that is connecting to the VPN server, and it must match the value that is configured on the VPN gateway in Azure. For Azure VPN Gateway, the system Local ID is the subject name of the client certificate that is used for authentication1. Therefore, option A is correct. A detailed explanation with references is as follows:
As mentioned in the scenario, the sales department devices are using Point-to-Site VPN connections to access Azure resources. A Point-to-Site VPN connection lets you create a secure connection to your virtual network from an individual client computer2. To configure a Point-to-Site VPN connection, you need to create a virtual network gateway of type VPN in Azure, and then install a VPN client on each device that needs to connect2. The VPN client configuration includes several settings, such as the VPN server address, the tunnel type, and the authentication method. One of these settings is the system Local ID, which is used to identify the VPN client that is connecting to the VPN server1. The system Local ID must match the value that is configured on the VPN gateway in Azure, otherwise the connection will fail.
For Azure VPN Gateway, there are three authentication methods available for Point-to-Site VPN connections: certificate-based authentication, OpenVPN with Azure AD
authentication, and OpenVPN with certificate-based authentication2. For certificate-based authentication, which is used in this scenario, the system Local ID is the subject name of the client certificate that is used for authentication1. The client certificate is generated from a root certificate that is uploaded to Azure when creating a Point-to-Site VPN connection, and it must be installed on each device that needs to connect2. The subject name of the client certificate can be obtained by using PowerShell or OpenSSL commands1. For example, using PowerShell:
$cert = Get-ChildItem -Path Cert:CurrentUserMy | Where-Object {$_.Subject -like “ContosoClientCert”} $cert.Subject
The output of this command will show the subject name of the client certificate that matches ContosoClientCert. This value should be configured as the system Local ID for the VPN client on each device.
Latest AZ-720 Dumps Valid Version with 81 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


that is a repeated question and is correct.