- All Exams Instant Download
In the screenshot above, which two pieces of information can be determined from the ACC configuration shown? (Choose two.)
In the screenshot above, which two pieces of information can be determined from the ACC configuration shown? (Choose two.)
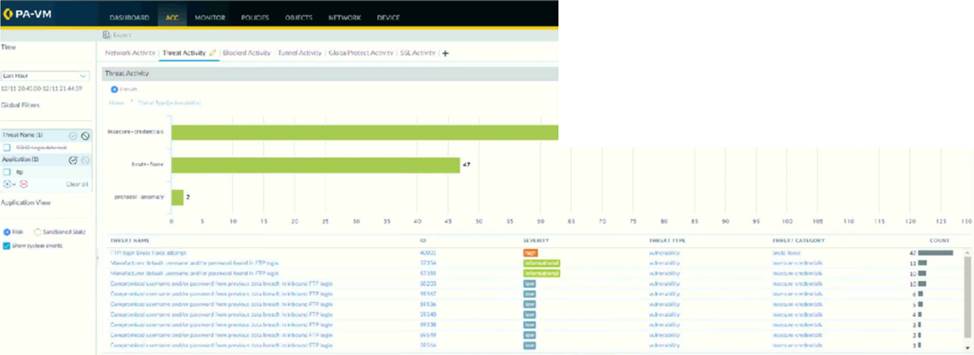
A . Threats with a severity of "high" are always listed at the top of the Threat Name list.
B . The ACC has been filtered to only show the FTP application.
C . The Network Activity tab will display all applications, including FT
E . Insecure-credentials, brute-force, and protocol-anomaly are all a part of the vulnerability Threat Type.
Answer: AD
Latest PCNSE Dumps Valid Version with 280 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

