Cisco 350-701 Implementing and Operating Cisco Security Core Technologies (SCOR) Online Training
Cisco 350-701 Online Training
The questions for 350-701 were last updated at Jan 13,2026.
- Exam Code: 350-701
- Exam Name: Implementing and Operating Cisco Security Core Technologies (SCOR)
- Certification Provider: Cisco
- Latest update: Jan 13,2026
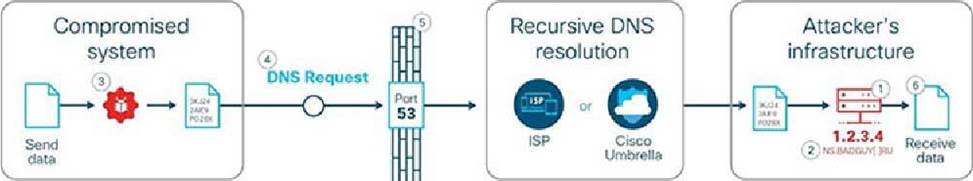
How is DNS tunneling used to exfiltrate data out of a corporate network?
- A . It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks.
- B . It encodes the payload with random characters that are broken into short strings and the DNS server
rebuilds the exfiltrated data. - C . It redirects DNS requests to a malicious server used to steal user credentials, which
allows further damage
and theft on the network. - D . It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers.
How is DNS tunneling used to exfiltrate data out of a corporate network?
- A . It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks.
- B . It encodes the payload with random characters that are broken into short strings and the DNS server
rebuilds the exfiltrated data. - C . It redirects DNS requests to a malicious server used to steal user credentials, which
allows further damage
and theft on the network. - D . It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers.
Which two descriptions of AES encryption are true? (Choose two)
- A . AES is less secure than 3DES.
- B . AES is more secure than 3DES.
- C . AES can use a 168-bit key for encryption.
- D . AES can use a 256-bit key for encryption.
- E . AES encrypts and decrypts a key three times in sequence.
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
- A . Cisco Identity Services Engine and AnyConnect Posture module
- B . Cisco Stealth watch and Cisco Identity Services Engine integration
- C . Cisco ASA firewall with Dynamic Access Policies configured
- D . Cisco Identity Services Engine with PxGrid services enabled
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0380739941 address 0.0.0.0 command on host A. The tunnel is not being established to host B.
What action is needed to authenticate the VPN?
- A . Change isakmp to ikev2 in the command on host A.
- B . Enter the command with a different password on host B.
- C . Enter the same command on host B.
- D . Change the password on host A to the default password.
What is the function of the Context Directory Agent?
- A . maintains users’ group memberships
- B . relays user authentication requests from Web Security Appliance to Active Directory
- C . reads the Active Directory logs to map IP addresses to usernames
- D . accepts user authentication requests on behalf of Web Security Appliance for user identification
Latest 350-701 Dumps Valid Version with 327 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund