Cisco 350-201 Performing CyberOps Using Core Security Technologies (CBRCOR) Online Training
Cisco 350-201 Online Training
The questions for 350-201 were last updated at Feb 28,2026.
- Exam Code: 350-201
- Exam Name: Performing CyberOps Using Core Security Technologies (CBRCOR)
- Certification Provider: Cisco
- Latest update: Feb 28,2026
Refer to the exhibit.
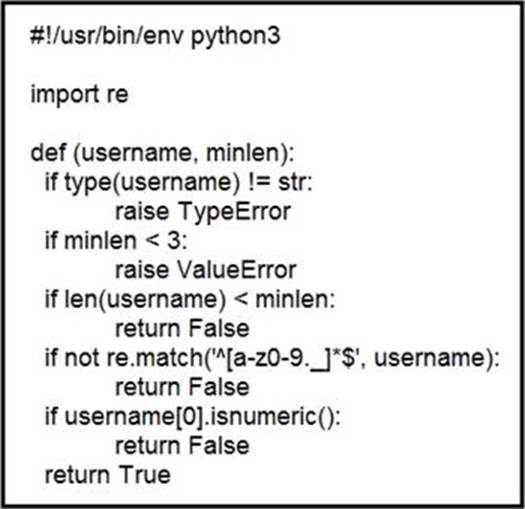
An organization is using an internal application for printing documents that requires a separate registration on the website.
The application allows format-free user creation, and users must match these required conditions to comply with the company’s user creation policy:
– minimum length: 3
– usernames can only use letters, numbers, dots, and underscores
– usernames cannot begin with a number
The application administrator has to manually change and track these daily to ensure compliance. An engineer is tasked to implement a script to automate the process according to the company user creation policy. The engineer implemented this piece of code within the application, but users are still able to create format-free usernames.
Which change is needed to apply the restrictions?
- A . modify code to return error on restrictions def return false_user(username, minlen)
- B . automate the restrictions def automate_user(username, minlen)
- C . validate the restrictions, def validate_user(username, minlen)
- D . modify code to force the restrictions, def force_user(username, minlen)
The SIEM tool informs a SOC team of a suspicious file. The team initializes the analysis with an automated sandbox tool, sets up a controlled laboratory to examine the malware specimen, and proceeds with behavioral analysis .
What is the next step in the malware analysis process?
- A . Perform static and dynamic code analysis of the specimen.
- B . Unpack the specimen and perform memory forensics.
- C . Contain the subnet in which the suspicious file was found.
- D . Document findings and clean-up the laboratory.
What is a limitation of cyber security risk insurance?
- A . It does not cover the costs to restore stolen identities as a result of a cyber attack
- B . It does not cover the costs to hire forensics experts to analyze the cyber attack
- C . It does not cover the costs of damage done by third parties as a result of a cyber attack
- D . It does not cover the costs to hire a public relations company to help deal with a cyber attack
Refer to the exhibit.
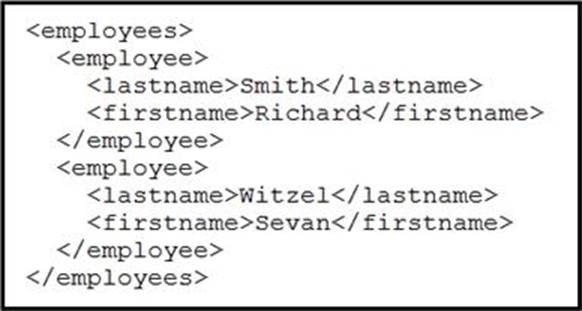
Which data format is being used?
- A . JSON
- B . HTML
- C . XML
- D . CSV
Refer to the exhibit.
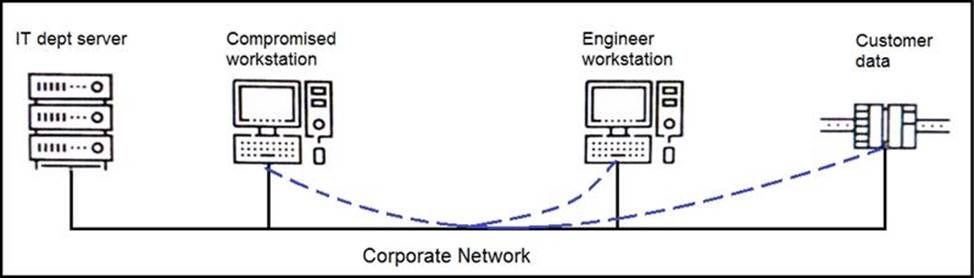
An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols .
Which action prevents this type of attack in the future?
- A . Use VLANs to segregate zones and the firewall to allow only required services and secured protocols
- B . Deploy a SOAR solution and correlate log alerts from customer zones
- C . Deploy IDS within sensitive areas and continuously update signatures
- D . Use syslog to gather data from multiple sources and detect intrusion logs for timely responses
Refer to the exhibit.
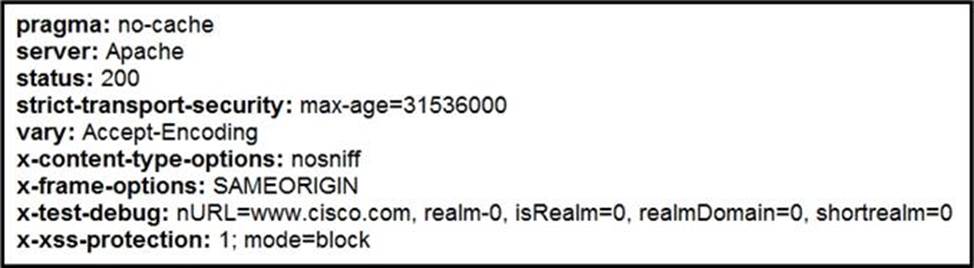
Where does it signify that a page will be stopped from loading when a scripting attack is detected?
- A . x-frame-options
- B . x-content-type-options
- C . x-xss-protection
- D . x-test-debug
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the playbook to mitigate the threat .
What is the first action for the incident response team?
- A . Assess the network for unexpected behavior
- B . Isolate critical hosts from the network
- C . Patch detected vulnerabilities from critical hosts
- D . Perform analysis based on the established risk factors
Refer to the exhibit.
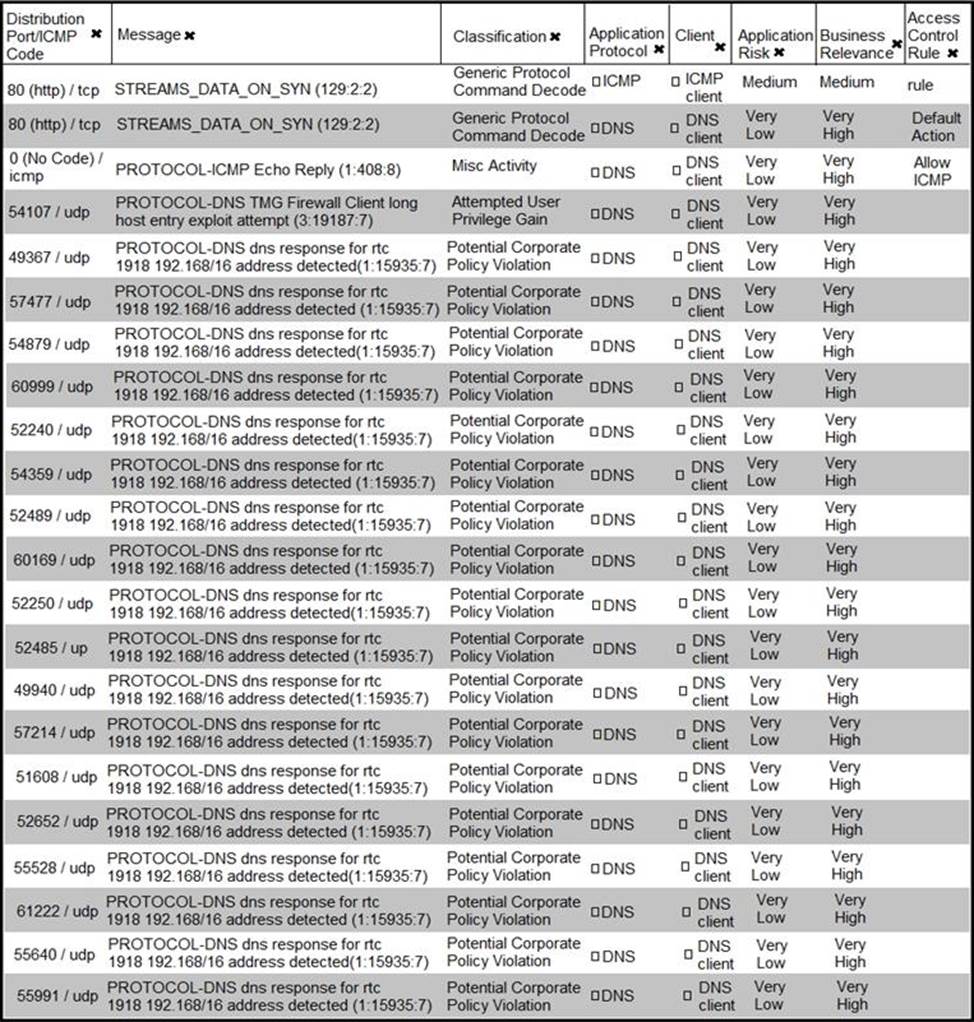
What is the connection status of the ICMP event?
- A . blocked by a configured access policy rule
- B . allowed by a configured access policy rule
- C . blocked by an intrusion policy rule
- D . allowed in the default action
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall.
Which action will improve the effectiveness of the process?
- A . Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
- B . Inform the user by enabling an automated email response when the rule is triggered.
- C . Inform the incident response team by enabling an automated email response when the rule is triggered.
- D . Create an automation script for blocking URLs on the firewall when the rule is triggered.
A security engineer discovers that a spreadsheet containing confidential information for nine of their employees was fraudulently posted on a competitor’s website. The spreadsheet contains names, salaries, and social security numbers .
What is the next step the engineer should take in this investigation?
- A . Determine if there is internal knowledge of this incident.
- B . Check incoming and outgoing communications to identify spoofed emails.
- C . Disconnect the network from Internet access to stop the phishing threats and regain control.
- D . Engage the legal department to explore action against the competitor that posted the spreadsheet.
Latest 350-201 Dumps Valid Version with 139 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

