Cisco 300-725 Securing the Web with Cisco Web Security Appliance (SWSA) Online Training
Cisco 300-725 Online Training
The questions for 300-725 were last updated at Jan 23,2026.
- Exam Code: 300-725
- Exam Name: Securing the Web with Cisco Web Security Appliance (SWSA)
- Certification Provider: Cisco
- Latest update: Jan 23,2026
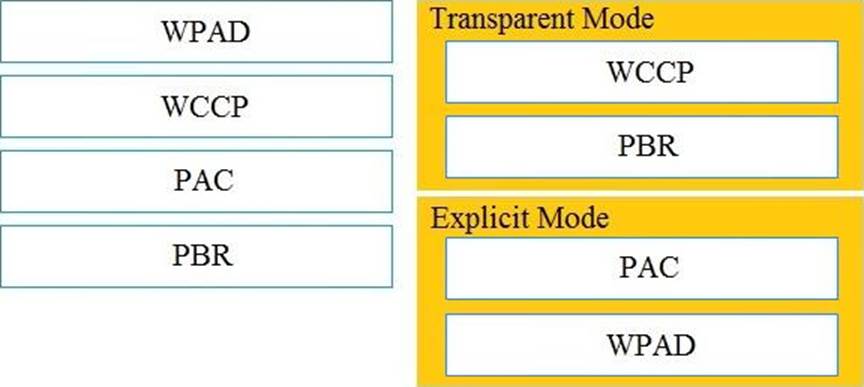
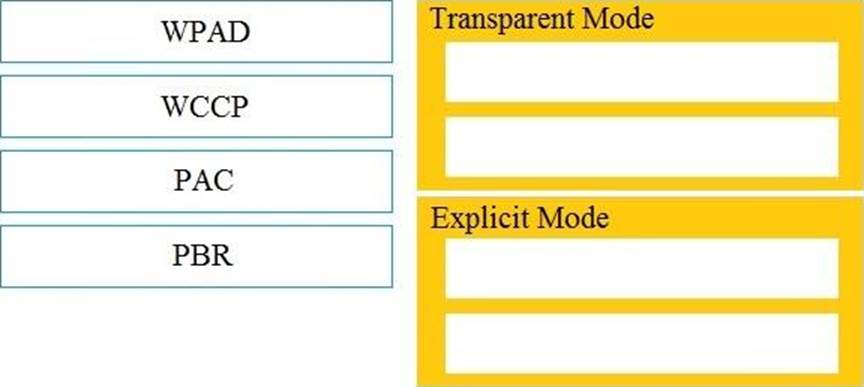
DRAG DROP
Drag and drop the Cisco WSA methods from the left onto the correct deployment modes on the right.
What causes authentication failures on a Cisco WSA when LDAP is used for authentication?
- A . when the passphrase contains only 5 characters
- B . when the passphrase contains characters that are not 7-bit ASCI
- C . when the passphrase contains one of following characters ‘@ # $ % ^’
- D . when the passphrase contains 50 characters
Refer to the exhibit.

Which statement about the transaction log is true?
- A . The log does not have a date and time
- B . The proxy had the content and did not contact other servers
- C . The transaction used TCP destination port 8187
- D . The AnalizeSuspectTraffic policy group was applied to the transaction
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address? (Choose two.)
- A . X-Forwarded-For
- B . high availability
- C . web cache
- D . via
- E . IP spoofing
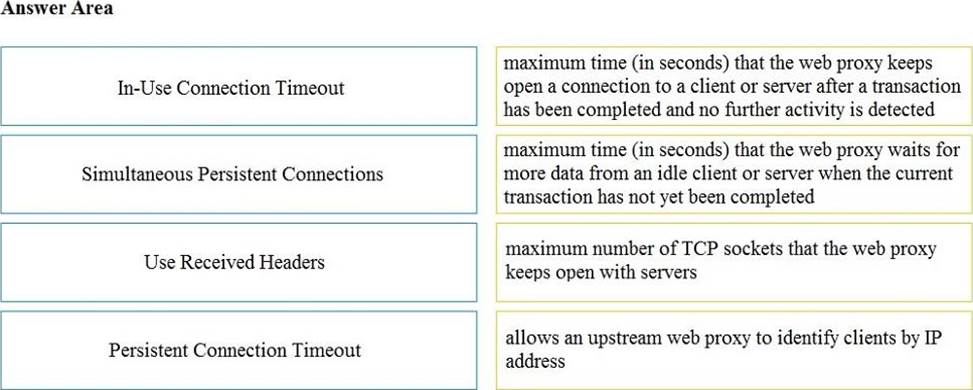
DRAG DROP
Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.
Which two configuration options are available on a Cisco WSA within a decryption policy? (Choose two.)
- A . Pass Through
- B . Warn
- C . Decrypt
- D . Allow
- E . Block
Which information in the HTTP request is used to determine if it is subject to the referrer exceptions feature in the Cisco WSA?
- A . protocol
- B . version
- C . header
- D . payload
What is used to configure WSA as an explicit proxy?
- A . IP Spoofing from router
- B . Network settings from user browser
- C . WCCP redirection from firewall
- D . Auto redirection using PBR from switch
Which key is needed to pair a Cisco WSA and Cisco ScanCenter for CTA?
- A . public SSH key that the Cisco WSA generates
- B . public SSH key that Cisco ScanCenter generates
- C . private SSH key that Cisco ScanCenter generates
- D . private SSH key that the Cisco WSA generates
What is a benefit of integrating Cisco Cognitive Threat Analytics with a Cisco WSA?
- A . It adds additional information to the Cisco WSA reports
- B . It adds additional malware protection to the Cisco WSA
- C . It provides the ability to use artificial intelligence to block viruses
- D . It reduces time to identify threats in the network
Latest 300-725 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund