Cisco 300-710 Securing Networks with Cisco Firepower (SNCF) Online Training
Cisco 300-710 Online Training
The questions for 300-710 were last updated at Jan 12,2026.
- Exam Code: 300-710
- Exam Name: Securing Networks with Cisco Firepower (SNCF)
- Certification Provider: Cisco
- Latest update: Jan 12,2026
In a Cisco AMP for Networks deployment, which disposition is returned if the cloud cannot be reached?
- A . unavailable
- B . unknown
- C . clean
- D . disconnected
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two.)
- A . dynamic null route configured
- B . DHCP pool disablement
- C . quarantine
- D . port shutdown
- E . host shutdown
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
- A . pxGrid
- B . FTD RTC
- C . FMC RTC
- D . ISEGrid
What is the maximum SHA level of filtering that Threat Intelligence Director supports?
- A . SHA-1024
- B . SHA-4096
- C . SHA-512
- D . SHA-256
Refer to the exhibit.
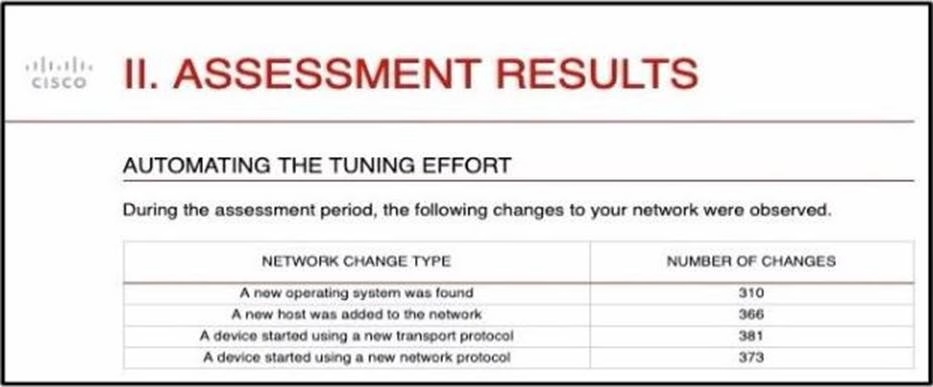
And engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network.
How is the Firepower configuration updated to protect these new operating systems?
- A . Cisco Firepower automatically updates the policies.
- B . The administrator requests a Remediation Recommendation Report from Cisco Firepower
- C . Cisco Firepower gives recommendations to update the policies.
- D . The administrator manually updates the policies.
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic segmentation.
Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
- A . multiple deployment
- B . single-context
- C . single deployment
- D . multi-instance
A network engineer is extending a user segment through an FTD device for traffic inspection without creating another IP subnet.
How is this accomplished on an FTD device in routed mode?
- A . by leveraging the ARP to direct traffic through the firewall
- B . by assigning an inline set interface
- C . by using a BVI and create a BVI IP address in the same subnet as the user segment
- D . by bypassing protocol inspection by leveraging pre-filter rules
An engineer is configuring a second Cisco FMC as a standby device but is unable to register with the active unit.
What is causing this issue?
- A . The primary FMC currently has devices connected to it.
- B . The code versions running on the Cisco FMC devices are different
- C . The licensing purchased does not include high availability
- D . There is only 10 Mbps of bandwidth between the two devices.
After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user.
Which widget should be configured to provide this visibility on the Cisco Firepower dashboards?
- A . Custom Analysis
- B . Current Status
- C . Current Sessions
- D . Correlation Events
An engineer has been asked to show application usages automatically on a monthly basis and send the information to management.
What mechanism should be used to accomplish this task?
- A . event viewer
- B . reports
- C . dashboards
- D . context explorer
Latest 300-710 Dumps Valid Version with 153 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

