Cisco 300-465 Designing the Cisco Cloud Online Training
Cisco 300-465 Online Training
The questions for 300-465 were last updated at Dec 10,2025.
- Exam Code: 300-465
- Exam Name: Designing the Cisco Cloud
- Certification Provider: Cisco
- Latest update: Dec 10,2025
A UCS Director administrator must convert a VM to an image.
Which option lists the steps to accomplish this task?
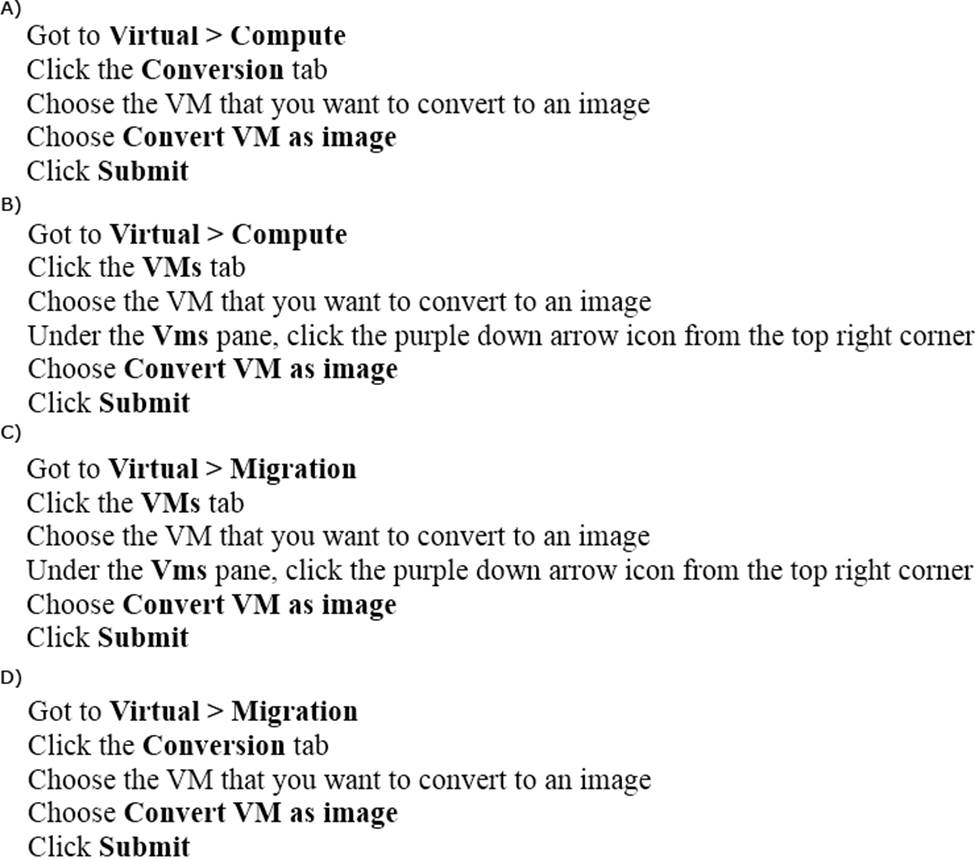
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which large-scale Layer 2 connectivity protocol is best for VLAN address space that is limited in large networks?
- A . VXLAN
- B . OTV
- C . LISP
- D . VPN
- E . NvGRE
Which three network services are offered by Microsoft Azure? (Choose three.)
- A . elastic load balancing
- B . traffic manager route incoming traffic for high performance and availability
- C . intrusion detection systems, load balancing, firewalls
- D . virtual private networks to be deployed and managed
- E . virtual network provision private networks, optionally connect to on-premises datacenters
- F . express route dedicated private network fiber connections to Azure
Which two options are Cisco Intercloud Fabric Deployment Models? (Choose two.)
- A . enterprise managed
- B . enterprise DMZ controlled
- C . small office home office deployment
- D . service provider managed hybrid cloud
Which statement about VACS is true?
- A . It provides centralized provisioning and orchestration for physical and virtual networking.
- B . It is designed around open standards and open APIs.
- C . It provides scalable and multi protocol controller infrastructure for supporting multiple service providers and services.
- D . Delivers a comprehensive cloud management solution spanning service offerings from underlying infrastructure to anything-as-a-service platforms.
From which module must a manager or supervisor review and authorize the service when an end user submits an order in the prime service catalog?
- A . Order Management
- B . Service Request
- C . Requisition
- D . Administration
Which protocol is used to extend Layer 2 for long-distance bridging?
- A . OTV
- B . VXLAN
- C . LISP
- D . VPN
- E . NvGRE
A cloud administrator is considering methods for securing the cloud infrastructure.
Which three statements about data plane protection are true? (Choose three.)
- A . You must preplan security policies and test them thoroughly before you implement them in an automated fashion.
- B . Define security policies after the creation of virtual machine environments.
- C . Storing sensitive information on the cloud is permissible as long as the data center architecture is resilient.
- D . Out-of-date corporate security policies contribute to data exposure.
- E . Encrypting data at rest on the disk is extremely helpful in assuring data protection within a cloud-based data center.
- F . Data encryption is enforced only when an application requires it.
A system administrator must use Cisco UCS Director to migrate several virtual machines from one host to another without disrupting the workload.
In which two ways can the administrator accomplish this task?
- A . migrate VM policy
- B . migrate VM wizard
- C . hot VM migration wizard
- D . hot VM workflow task
- E . migrate VM workflow task
A cloud administrator is designing role-based access control security policies for a private Cloud.
Which two statements are the goals of these policies? (Choose two.)
- A . to ensure that no known security vulnerabilities are present
- B . to protect data center integrity in case of a link failure in any layer
- C . to provide content security services
- D . to reduce security risks when accessing the data center
- E . to control access so that administrators have access only to systems for which they have administrative responsibilities
Latest 300-465 Dumps Valid Version with 118 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

