Cisco 500-220 Engineering Cisco Meraki Solutions v1.0 Online Training
Cisco 500-220 Online Training
The questions for 500-220 were last updated at Feb 15,2026.
- Exam Code: 500-220
- Exam Name: Engineering Cisco Meraki Solutions v1.0
- Certification Provider: Cisco
- Latest update: Feb 15,2026
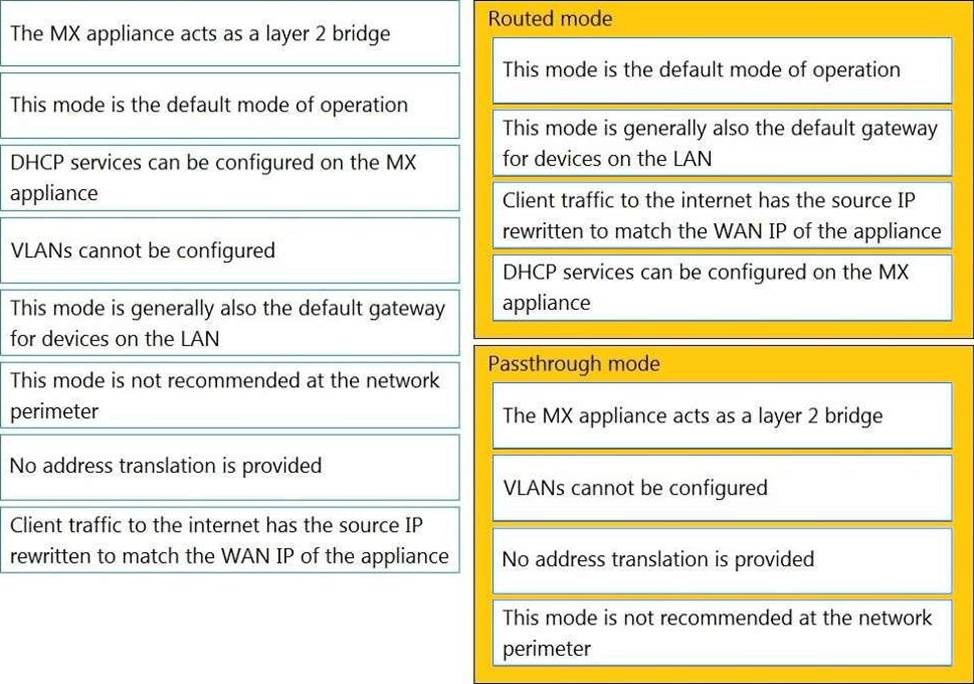
DRAG DROP
Drag and drop the descriptions from the left onto the corresponding MX operation mode on the right.
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
- A . Controller disconnection behavior
- B . Captive Portal strength
- C . Simultaneous logins
- D . Firewall & traffic shaping
- E . RADIUS for splash page settings
Refer to the exhibit.
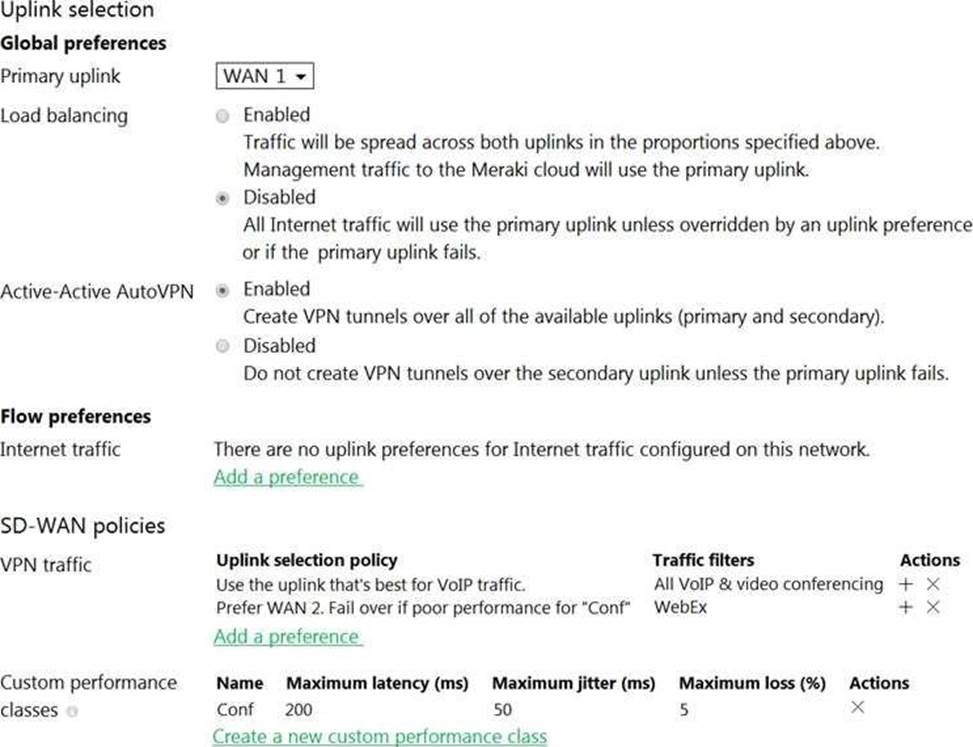
Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
- A . WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the “Conf” performance class.
- B . WebEx traffic will prefer WAN 1 as it is the primary uplink.
- C . WebEx traffic will prefer WAN 2 as long as it is up.
- D . WebEx traffic will be load-balanced between both active WAN links.
For which two reasons can an organization become “Out of License”? (Choose two.)
- A . licenses that are in the wrong network
- B . more hardware devices than device licenses
- C . expired device license
- D . licenses that do not match the serial numbers in the organization
- E . MR licenses that do not match the MR models in the organization
Refer to the exhibit.
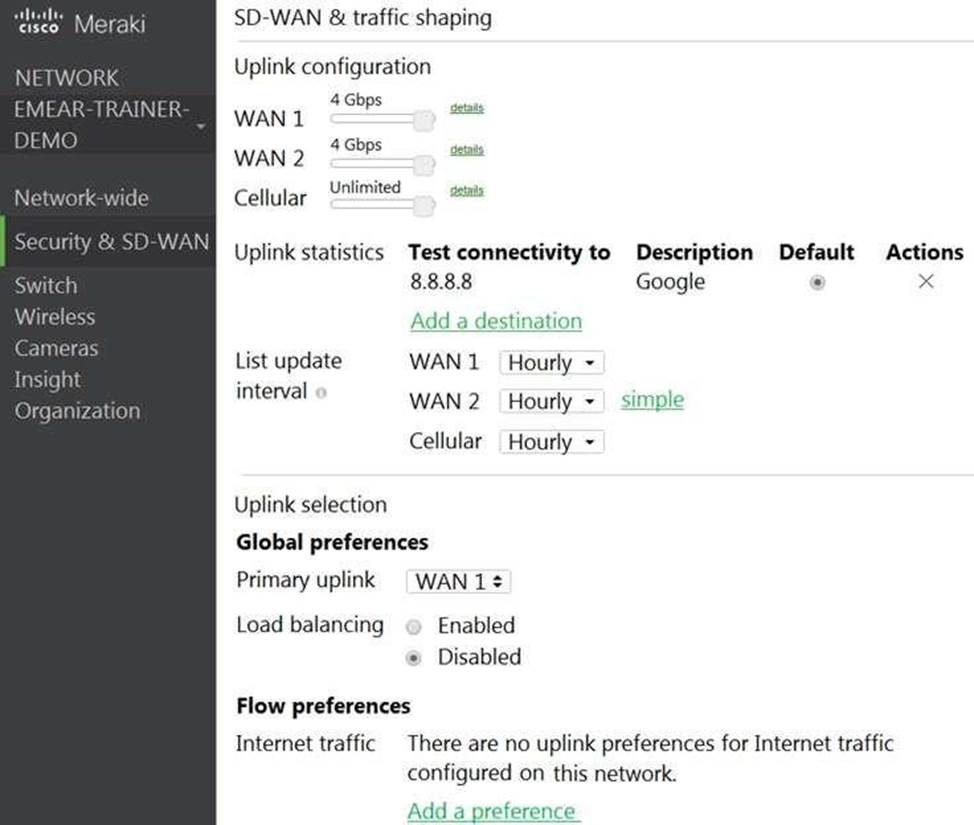
Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
- A . Change the primary uplink to "none".
- B . Add an internet traffic preference that defines the load-balancing ratio as 4:1.
- C . Enable load balancing.
- D . Set the speed of the cellular uplink to zero.
- E . Change the assigned speeds of WAN 1 and WAN 2 so that the ratio is 4:1.
Which Cisco Meraki best practice method preserves complete historical network event logs?
- A . Configuring the preserved event number to maximize logging.
- B . Configuring the preserved event period to unlimited.
- C . Configuring a syslog server for the network.
- D . Configuring Dashboard logging to preserve only certain event types.
Which design requirement is met by implementing syslog versus SNMP?
- A . when automation capabilities are needed
- B . when proactive alerts for critical events must be generated
- C . when organization-wide information must be collected
- D . when information such as flows and client connectivity must be gathered
Refer to the exhibit.
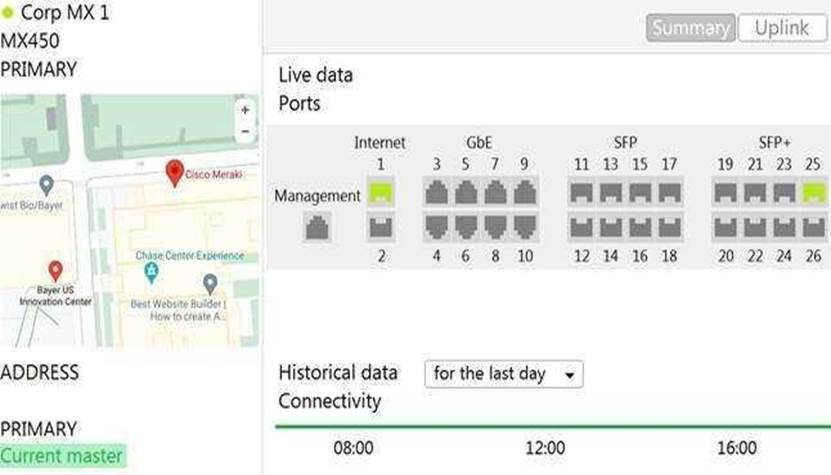
The VPN concentrator is experiencing issues.
Which action should be taken to ensure a stable environment?
- A . Add a deny any/any firewall rule to the end of the firewall rules.
- B . Remove the connection from Internet 1.
- C . Physically disconnect all LAN ports.
- D . Configure the MX appliance to Routed mode on the Addressing & VLANS page.
Refer to the exhibit.
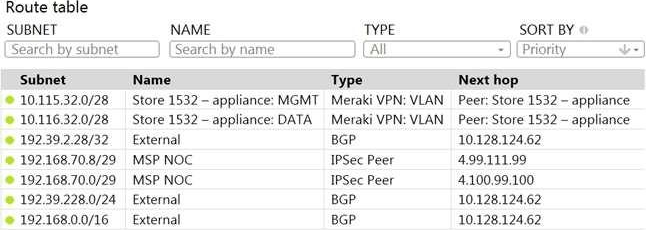
A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4.
What is the next hop for the packet, based on this concentrator routing table?
- A . The concentrator gateway (10.128.124.62) is the next hop.
- B . Not enough detail is available to determine the next hop.
- C . The packet is stopped.
- D . The Auto VPN peer “Store 1532 C appliance” is the next hop.
Company iPads are enrolled in Systems Manager without supervision, and profiles are pushed through Systems Manager.
Which outcome occurs when a user attempts to remove the “Meraki Management” profile on an iPad?
- A . The “Meraki Management” profile cannot be removed.
- B . The “Meraki Management” profile is removed and then pushed automatically by Systems Manager.
- C . The “Meraki Management” profile is removed. All the profiles that Systems Manager pushed are also removed.
- D . The “Meraki Management” profile is removed. All the profiles Systems Manager pushed remain.
Latest 500-220 Dumps Valid Version with 57 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund