- All Exams Instant Download
You are preparing a local audit policy for your workstation. No auditing is enabled
HOTSPOT
You are preparing a local audit policy for your workstation. No auditing is enabled.
The settings of your policy are shown in the following image:
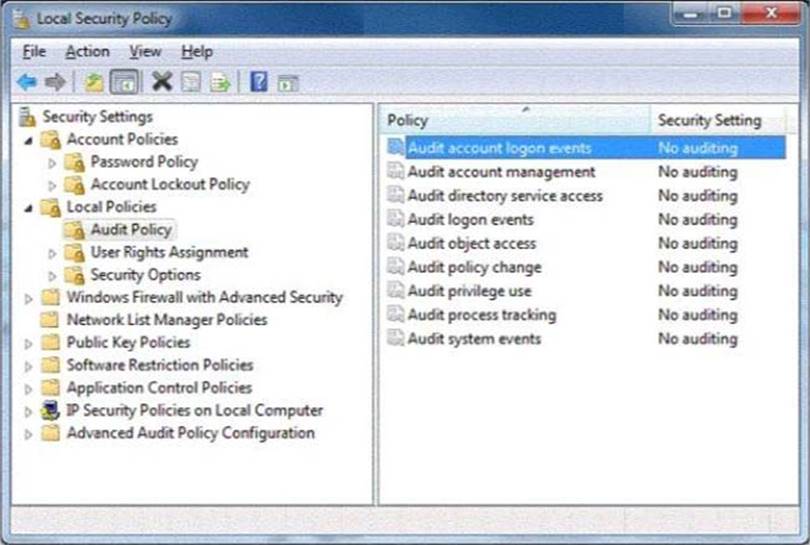
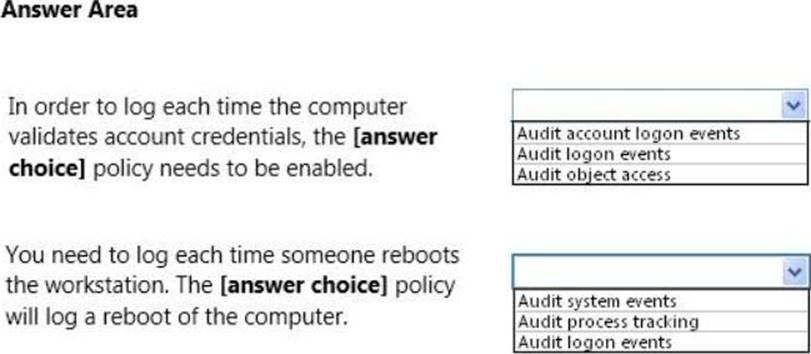
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
Answer: 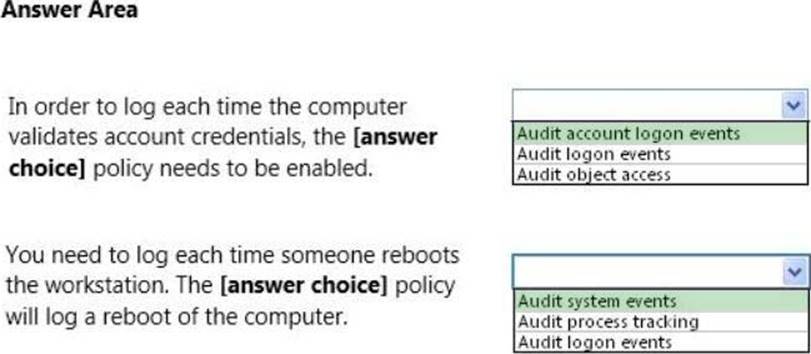
Explanation:
Dozens of events can be audited in Windows.
The events fall into several categories:
– Audit account logon events – audit each instance of a user logging on to or logging off from another computer in which this computer is used to validate the account. This event category is applicable to domain controllers only since DC’s are used to validate accounts in domains.
– Audit account management – audit each event of account management on a computer. Examples of account maintenance include password changes, user account and group modifications.
– Audit directory service access – audit the event of a user accessing an Active Directory object that has its own system access control list (SACL) specified.
– Audit logon events – audit each instance of a user logging on to or logging off from a computer. Note that this is different than the ‘Audit account login events’ category. This tracks the logon event to a specific server. The former tracks which domain controller authenticated the user.
– Audit object access – audit the event of a user accessing an object that has its own system access control list (SACL) specified. Examples of objects are files, folders, registry keys, printers, etc.
– Audit policy change – audit every incident of a change to user rights assignment policies, audit policies, or trust policies.
– Audit privilege use – audit each instance of a user exercising a user right.
– Audit process tracking – audit detailed tracking information for events such as program activation, process exit, handle duplication, and indirect object access.
– Audit system events – audit when a user restarts or shuts down the computer or when an event occurs
that affects either the system security or the security log.
Reference: http://www.petri.co.il/windows_auditing.htm
Latest 98-367 Dumps Valid Version with 168 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

