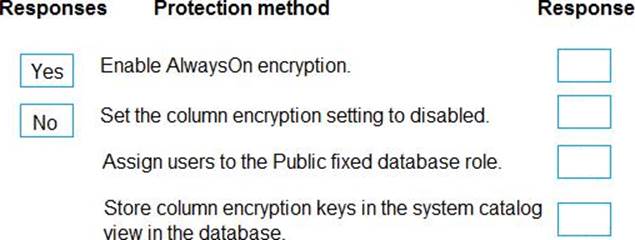
Will each protection method meet the requirement?
DRAG DROP
You must ensure that the external party cannot access the data in the SSN column of the Person table.
Will each protection method meet the requirement? To answer, drag the appropriate responses to the correct protection methods. Each response may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Answer: 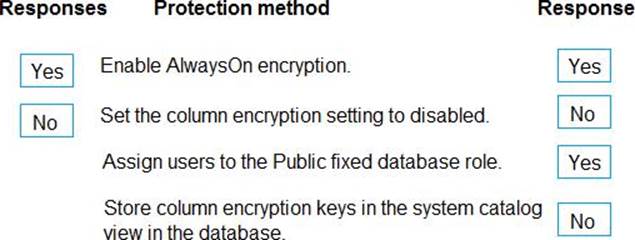
Explanation:
Box 1: Yes
You can configure Always Encrypted for individual database columns containing your sensitive data. When setting up encryption for a column, you specify the information about the encryption algorithm and cryptographic keys used to protect the data in the column.
Box 2: No
Box 3: Yes
In SQL Database, the VIEW permissions are not granted by default to the public fixed database role. This enables certain existing, legacy tools (using older versions of DacFx) to work properly. Consequently, to work with encrypted columns (even if not decrypting them) a database administrator must explicitly grant the two VIEW permissions.
Box 4: No
All cryptographic keys are stored in an Azure Key Vault.
References: https://docs.microsoft.com/en-us/sql/relational-databases/security/encryption/always-encrypted-database-engine
Latest AZ-204 Dumps Valid Version with 254 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

