- All Exams Instant Download
Which of the following attacks can be mitigated by these configuration settings?
Analyze the screenshot below.
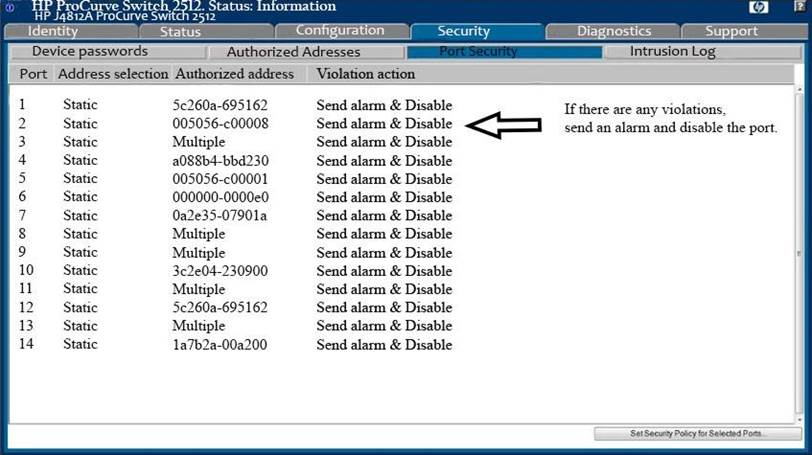
Which of the following attacks can be mitigated by these configuration settings?
A . A Denial-of-Service attack using network broadcasts
B . A Replay attack
C . An IP masquerading attack
D . A MAC Flood attack
Answer: D
Explanation:
Both BPDU Guard and Root Guard are used to prevent a new switch from becoming the Root Bridge. They are very similar but use different mechanisms.
Rootguard allows devices to use STP, but if they send superior BDPUs (i.e. they attempt to become the Root Bridge), Root Guard disables the port until the offending BPDUs cease. Recovery is automatic. If Portfast is enabled on a port, BPDU Guard will disable the port if a BPDU is received. The port stays disabled until it is manually re-enabled. Devices behind such ports cannot use STP, as the port would be disabled as soon as they send BPDUs (which is the default behavior of switches).
Latest GCED Dumps Valid Version with 88 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

