Which Cisco IOS security feature can you configure on R1 to drop requests from the attacker to hast A?
Refer to the exhibit.
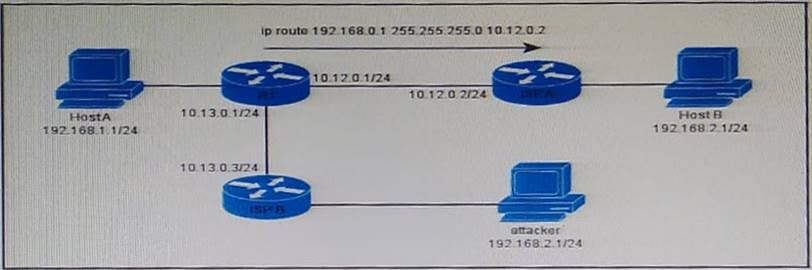
You have configured R1 to connect to two different ISPs, which allows remote users to access host A through both ISPs.
Which Cisco IOS security feature can you configure on R1 to drop requests from the attacker to hast A?
A . uRPF loose mode
B . IP source guard
C . port security
D . uRPF strict mode
Answer: A
Latest 400-101 Dumps Valid Version with 150 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Loose mode will allow the attacker to achieve his goal as it would only check for the presence of the route in the RIB. We need strict mode here as there’s the clear intent (see the static route) of reaching host b network through ISP A. I take it, anyway, that the static route should be for 192.168.2/24
I think it’s C
I guess it should be D , as loose mode will still allow attacks from 192.168.2.1 as long as the route “192.168.2.1” is in the routing table .