Symantec 250-428 Administration of Symantec Endpoint Protection 14 Online Training
Symantec 250-428 Online Training
The questions for 250-428 were last updated at Dec 15,2025.
- Exam Code: 250-428
- Exam Name: Administration of Symantec Endpoint Protection 14
- Certification Provider: Symantec
- Latest update: Dec 15,2025
A Symantec Endpoint Protection (SEP) administrator receives multiple reports that machines are experiencing performance issues. The administrator discovers that the reports happen about the same time as the scheduled LiveUpdate.
Which setting should the SEP administrator configure to minimize I/O when LiveUpdate occurs?
- A . Disable Allow user-defined scans to run when the scan author is logged off
- B . Change the LiveUpdate schedule
- C . Disable Run an Active Scan when new definitions arrive
- D . Change the Administrator-defined scan schedule
Which action must a Symantec Endpoint Protection administrator take before creating custom Intrusion Prevention signatures?
- A . Define signature variables
- B . Enable signature logging
- C . Change the custom signature order
- D . Create a Custom Intrusion Prevention Signature library
Which tool should the administrator run before starting the Symantec Endpoint Protection Manager upgrade according to best practices?
- A . CollectLog.cmd
- B . DBValidator.bat
- C . LogExport.cmd
- D . Upgrade.exe
A company allows users to create firewall rules. During the course of business, users are accidentally adding rules that block a custom internal application.
Which steps should the Symantec Endpoint Protection administrator take to prevent users from blocking the custom application?
- A . Create an Allow All Firewall rule for the fingerprint of the file and place it at the bottom of the firewall rules above the blue line
- B . Create an Allow firewall rule for the application and place it at the bottom of the firewall rules below the blue line
- C . Create an Allow for the network adapter type used by the application and place it at the top of the firewall rules below the blue line.
- D . Create an Allow Firewall rule for the application and place it at the top of the firewall rules above the blue line.
Which action does SONAR take before convicting a process?
- A . Checks the reputation of the process
- B . Restarts the system
- C . Quarantines the process
- D . Blocks suspicious behavior
An administrator is re-adding an existing Replication Partner to the local Symantec Endpoint Protection Manager site.
Which two parameters are required to re-establish this replication partnership? (Select two.)
- A . Remote site Encryption Password
- B . Remote server IP Address and port
- C . Remote SQL database account credentials
- D . Remote server Administrator credentials
- E . Remote site Domain ID
A company uses a remote administration tool that is detected and quarantined by Symantec Endpoint Protection (SEP).
Which step can an administrator perform to continue using the remote administration tool without detection by SEP?
- A . Create a Tamper Protect exception for the tool
- B . Create a SONAR exception for the tool
- C . Create an Application to Monitor exception for the tool
- D . Create a Known Risk exception for the tool
A Symantec Endpoint Protection (SEP) administrator performed a disaster recovery without a database backup.
In which file should the SEP administrator add “scm.agent.groupcreation=true” to enable the automatic creation of client groups?
- A . conf.properties
- B . httpd.conf
- C . settings.conf
- D . catalina.out
Why does Power Eraser need Internet access?
- A . Validate root certificates on all portable executables (PXE) files
- B . Leverage Symantec Insight
- C . Ensure the Power Eraser tool is the latest release
- D . Look up CVE vulnerabilities
Why is Notepad unable to save the changes to the file in the image below?
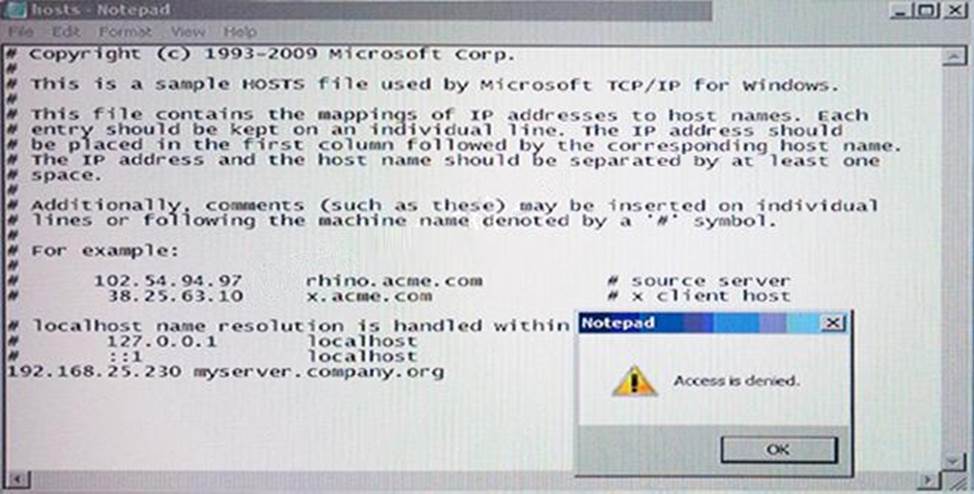
- A . SONAR High Risk detection is set to Block
- B . SONAR is set to block host file modifications.
- C . Tamper Protection is preventing Notepad from modifying the host file.
- D . System Lockdown is enabled.
Latest 250-428 Dumps Valid Version with 135 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

