Splunk SPLK-1003 Splunk Enterprise Certified Admin Online Training
Splunk SPLK-1003 Online Training
The questions for SPLK-1003 were last updated at Jun 21,2025.
- Exam Code: SPLK-1003
- Exam Name: Splunk Enterprise Certified Admin
- Certification Provider: Splunk
- Latest update: Jun 21,2025
In this source definition the MAX_TIMESTAMP_LOOKHEAD is missing.
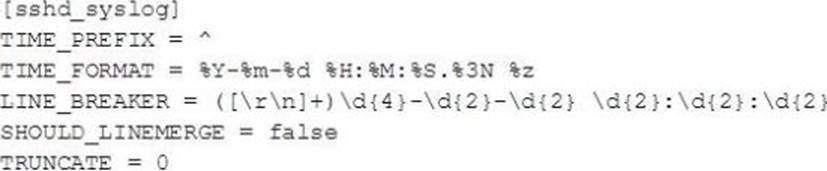
Event example:
![]()
Which value would fit best?
- A . MAX_TIMESTAMP_L0CKAHEAD = 5
- B . MAX_TIMESTAMP_LOOKAHEAD – 10
- C . MAX_TIMESTAMF_LOOKHEAD = 20
- D . MAX TIMESTAMP LOOKAHEAD – 30
D
Explanation:
https://docs.splunk.com/Documentation/Splunk/6.2.0/Data/Configuretimestamprecognition "Specify how far (how many characters) into an event Splunk software should look for a timestamp." since TIME_PREFIX = ^ and timestamp is from 0-29 position, so D=30 will pick up the WHOLE timestamp correctly.
Which of the following are required when defining an index in indexes. conf? (select all that apply)
- A . coldPath
- B . homePath
- C . frozenPath
- D . thawedPath
ABD
Explanation:
homePath = $SPLUNK_DB/hatchdb/db
coldPath = $SPLUNK_DB/hatchdb/colddb
thawedPath = $SPLUNK_DB/hatchdb/thaweddb
https://docs.splunk.com/Documentation/Splunk/latest/Admin/Indexesconf
https://docs.splunk.com/Documentation/Splunk/7.3.1/Admin/Indexesconf#PER_INDEX_OPTIONS
Which of the following apply to how distributed search works? (select all that apply)
- A . The search head dispatches searches to the peers
- B . The search peers pull the data from the forwarders.
- C . Peers run searches in parallel and return their portion of results.
- D . The search head consolidates the individual results and prepares reports
ACD
Explanation:
Users log on to the search head and run reports: C The search head dispatches searches to the peers
C Peers run searches in parallel and return their portion of results C The search head consolidates the individual results and prepares reports
What hardware attribute would need to be changed to increase the number of simultaneous searches (ad-hoc and scheduled) on a single search head?
- A . Disk
- B . CPUs
- C . Memory
- D . Network interface cards
B
Explanation:
https://docs.splunk.com/Documentation/Splunk/7.3.1/DistSearch/SHCarchitecture
Scroll down to section titled, How the cluster handles concurrent search quotas, "Overall search quota. This quota determines the maximum number of historical searches (combined scheduled and ad hoc) that the cluster can run concurrently. This quota is configured with max_Searches_per_cpu and related settings in limits.conf."
Which authentication methods are natively supported within Splunk Enterprise? (select all that apply)
- A . LDAP
- B . SAML
- C . RADIUS
- D . Duo Multifactor Authentication
ABC
Explanation:
Reference: https://docs.splunk.com/Documentation/Splunk/7.3.1/Security/SetupuserauthenticationwithSplunk
Splunk authentication: Provides Admin, Power and User by default, and you can define your own roles using a list of capabilities. If you have an Enterprise license, Splunk authentication is enabled by default. See Set up user authentication with Splunk’s built-in system for more information. LDAP: Splunk Enterprise supports authentication with its internal authentication services or your existing LDAP server. See Set up user authentication with LDAP for more information. Scripted authentication API: Use scripted authentication to integrate Splunk authentication with an external authentication system, such as RADIUS or PAM. See Set up user authentication with external systems for more information. Note: Authentication, including native authentication, LDAP, and scripted authentication, is not available in Splunk Free.
Which configuration files are used to transform raw data ingested by Splunk? (Choose all that apply.)
- A . props.conf
- B . inputs.conf
- C . rawdata.conf
- D . transforms.conf
AD
Explanation:
https://docs.splunk.com/Documentation/Splunk/8.1.1/Knowledge/Configureadvancedextractionswithfieldtransforms
use transformations with props.conf and transforms.conf to:
C Mask or delete raw data as it is being indexed COverride sourcetype or host based upon event values
C Route events to specific indexes based on event content
C Prevent unwanted events from being indexed
Explanation:
Reference: https://docs.splunk.com/Documentation/Splunk/8.0.5/Data/Configuretimestamprecognition
What conf file needs to be edited to set up distributed search groups?
- A . props.conf
- B . search.conf
- C . distsearch.conf
- D . distibutedsearch.conf
C
Explanation:
"You can group your search peers to facilitate searching on a subset of them. Groups of search peers are known as "distributed search groups." You specify distributed search groups in the distsearch.conf file"
Reference: https://docs.splunk.com/Documentation/Splunk/8.0.5/DistSearch/Distributedsearchgroups
After configuring a universal forwarder to communicate with an indexer, which index can be checked via the Splunk Web UI for a successful connection?
- A . index=main
- B . index=test
- C . index=summary
- D . index=_internal
D
Explanation:
Reference: https://docs.splunk.com/Documentation/Splunk/8.0.5/Security/Validateyourconfiguration
Which of the following are available input methods when adding a file input in Splunk Web? (Choose all that apply.)
- A . Index once.
- B . Monitor interval.
- C . On-demand monitor.
- D . Continuously monitor.
AD
Explanation:
https://docs.splunk.com/Documentation/Splunk/8.2.2/Data/Howdoyouwanttoadddata
The fastest way to add data to your Splunk Cloud instance or Splunk Enterprise deployment is to use Splunk Web. After you access the Add Data page, choose one of three options for getting data into your Splunk platform deployment with Splunk Web: (1) Upload, (2) Monitor, (3) Forward The Upload option lets you upload a file or archive of files for indexing. When you choose Upload option, Splunk Web opens the upload process page. Monitor. For Splunk Enterprise installations, the Monitor option lets you monitor one or more files, directories, network streams, scripts, Event Logs (on Windows hosts only), performance metrics, or any other type of machine data that the Splunk Enterprise instance has access to.
Which is a valid stanza for a network input?
- A . [udp://172.16.10.1:9997] connection = dns sourcetype = dns
- B . [any://172.16.10.1:10001] connection_host = ip sourcetype = web
- C . [tcp://172.16.10.1:9997] connection_host = web sourcetype = web
- D . [tcp://172.16.10.1:10001] connection_host = dns sourcetype = dns
D
Explanation:
https://docs.splunk.com/Documentation/Splunk/8.1.1/Data/Monitornetworkports
Reference: https://docs.splunk.com/Documentation/SplunkCloud/8.0.2006/Data/Bypassautomaticsourcetypeassignment
Latest SPLK-1003 Dumps Valid Version with 119 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

