Refer to the exhibit.
Refer to the exhibit.
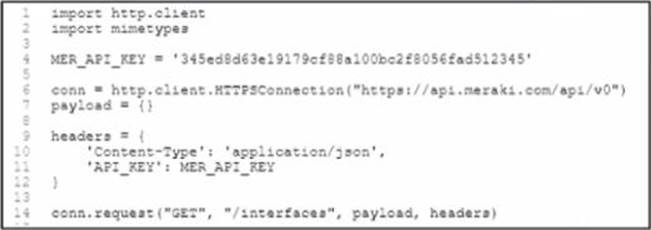
A developer created a Python script to retrieve information about Meraki devices in a local
network deployment After requesting a security review of the code the security analyst has
observed poor secret storage practices What is the appropriate secret storage approach”
A . Set the Base64 encoded version of the API key as MER_API_KEY m the code and Base64 decode before using m the header
B . Leverage an external secret vault to retrieve MER_API_KEY and embed the vault key as a new variable before running the code
C . Leverage an external secret vault to retrieve MER_APl_KEY and set the vault key as an OS environment variable before running the code
D . Set an OS environment variable for MER_API_KEY to the API key before running the code and no longer set MER_API_KEY within the code
Answer: C
Latest 350-901 Dumps Valid Version with 169 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

