HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
Select the answer that correctly completes the sentence.
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/get-started/
HOTSPOT
Select the answer that correctly completes the sentence.
Explanation:
eDiscovery
https://docs.microsoft.com/en-us/microsoft-365/compliance/ediscovery?view=o365-worldwide
Reference: https://docs.microsoft.com/en-us/azure/security/fundamentals/customer-lockbox-overview
HOTSPOT
Select the answer that correctly completes the sentence.
Explanation:
Federation is a collection of domains that have established trust.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-fed
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Yes
System updates reduces security vulnerabilities, and provide a more stable environment for end users. Not applying updates leaves unpatched vulnerabilities and results in environments that are susceptible to attacks.
Box 2: Yes
Box 3: Yes
If you only use a password to authenticate a user, it leaves an attack vector open. With MFA enabled, your accounts are more secure.
Reference: https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls
Which score measures an organization’s progress in completing actions that help reduce risks associated to data protection and regulatory standards?
- A . Microsoft Secure Score
- B . Productivity Score
- C . Secure score in Azure Security Center
- D . Compliance score
D
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365- worldwide
What do you use to provide real-time integration between Azure Sentinel and another security source?
- A . Azure AD Connect
- B . a Log Analytics workspace
- C . Azure Information Protection
- D . a data connector
D
Explanation:
To on-board Azure Sentinel, you first need to connect to your security sources. Azure Sentinel comes with a number of connectors for Microsoft solutions, including Microsoft 365 Defender solutions, and Microsoft 365 sources, including Office 365, Azure AD, Microsoft Defender for Identity, and Microsoft Cloud App Security, etc.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)?
- A . the Microsoft Endpoint Manager admin center
- B . Azure Cost Management + Billing
- C . Microsoft Service Trust Portal
- D . the Azure Active Directory admin center
C
Explanation:
The Microsoft Service Trust Portal contains details about Microsoft’s implementation of controls and processes that protect our cloud services and the customer data therein.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365- worldwide
In the shared responsibility model for an Azure deployment, what is Microsoft solely responsible for managing?
- A . the management of mobile devices
- B . the permissions for the user data stored in Azure
- C . the creation and management of user accounts
- D . the management of the physical hardware
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Yes
Box 2: Yes
Box 3: No
The Zero Trust model does not assume that everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originated from an uncontrolled network.
Reference: https://docs.microsoft.com/en-us/security/zero-trust/
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://privacy.microsoft.com/en-US/
What can you use to provide a user with a two-hour window to complete an administrative task in Azure?
- A . Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
- B . Azure Multi-Factor Authentication (MFA)
- C . Azure Active Directory (Azure AD) Identity Protection
- D . conditional access policies
D
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management: Provide just-in-time privileged access to Azure AD and Azure resources Assign time-bound access to resources using start and end dates Require approval to activate privileged roles Enforce multi-factor authentication to activate any role Use justification to understand why users activate Get notifications when privileged roles are activated Conduct access reviews to ensure users still need roles Download audit history for internal or external audit Prevents removal of the last active Global Administrator role assignment
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory (Azure AD)?
- A . Active Directory Federation Services (AD FS)
- B . Azure Sentinel
- C . Azure AD Connect
- D . Azure Ad Privileged Identity Management (PIM)
C
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-azure-ad-connect
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Yes
Azure AD supports custom roles.
Box 2: Yes
Global Administrator has access to all administrative features in Azure Active Directory.
Box 3: No
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/roles/concept-understand-roles
https://docs.microsoft.com/en-us/azure/active-directory/roles/permissions-reference
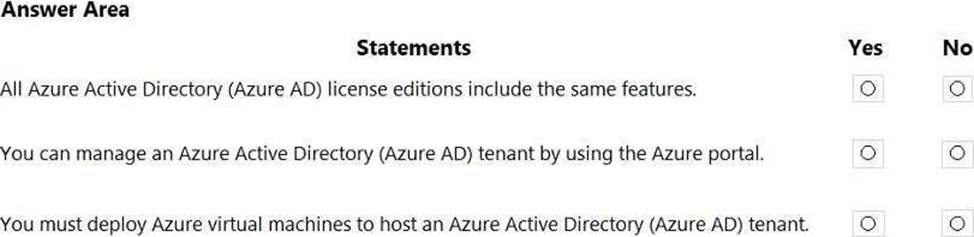
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: No
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Box 2: Yes
Microsoft 365 uses Azure Active Directory (Azure AD). Azure Active Directory (Azure AD) is included with your Microsoft 365 subscription.
Box 3: Yes
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Reference: https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
HOTSPOT
Select the answer that correctly completes the sentence.
Explanation:
Biometrics templates are stored locally on a device.
Reference: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
What is the purpose of Azure Active Directory (Azure AD) Password Protection?
- A . to control how often users must change their passwords
- B . to identify devices to which users can sign in without using multi-factor authentication (MFA)
- C . to encrypt a password by using globally recognized encryption standards
- D . to prevent users from using specific words in their passwords
D
Explanation:
Azure AD Password Protection detects and blocks known weak passwords and their variants, and can also block additional weak terms that are specific to your organization.
With Azure AD Password Protection, default global banned password lists are automatically applied to all users in an Azure AD tenant. To support your own business and security needs, you can define entries in a custom banned password list.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad-on-premises
Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group?
- A . access reviews
- B . managed identities
- C . conditional access policies
- D . Azure AD Identity Protection
A
Explanation:
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview