Microsoft MD-102 Endpoint Administrator Online Training
Microsoft MD-102 Online Training
The questions for MD-102 were last updated at Feb 27,2026.
- Exam Code: MD-102
- Exam Name: Endpoint Administrator
- Certification Provider: Microsoft
- Latest update: Feb 27,2026
You have a Microsoft 365 E5 subscription.
You need to ensure that when a Windows device is joined to the Microsoft Entra tenant, the device is enrolled automatically in Microsoft Intune.
What should you configure?
- A . the Windows Information Protection (WIP) user scope
- B . the Enterprise State Roaming settings
- C . the Microsoft Entra join and registration settings
- D . the mobile device management (MDM) user scope
Manage identity and compliance
Testlet 1
Case study
Overview
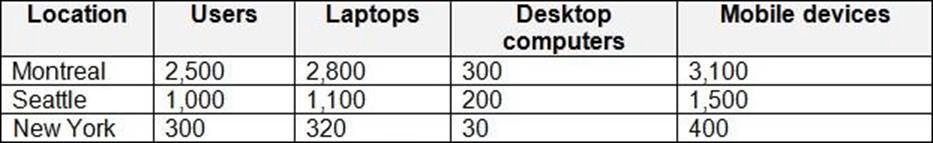
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
Contoso has the users and computers shown in the following table.
The company has IT, human resources (HR), legal (LEG), marketing (MKG), and finance (FIN) departments.
Contoso recently purchased a Microsoft 365 subscription.
The company is opening a new branch office in Phoenix. Most of the users in the Phoenix office will work from home.
Existing Environment
The network contains an Active Directory domain named contoso.com that is synced to Azure AD.
All member servers run Windows Server 2016. All laptops and desktop computers run Windows 10 Enterprise.
The computers are managed by using Microsoft Configuration Manager. The mobile devices are managed by using Microsoft Intune.
The naming convention for the computers is the department acronym, followed by a hyphen, and then four numbers, for example FIN-6785. All the computers are joined to the on-premises Active Directory domain.
Each department has an organizational unit (OU) that contains a child OU named Computers. Each computer account is in the Computers OU of its respective department.
Intune Configuration
The domain has the users shown in the following table.

User2 is a device enrollment manager (DEM) in Intune.
The devices enrolled in Intune are shown in the following table.
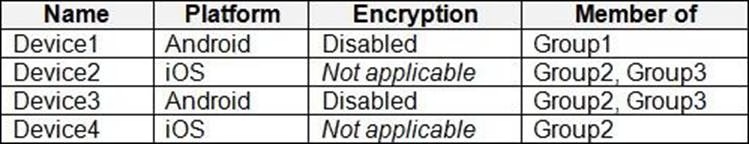
The device compliance policies in Intune are configured as shown in the following table.
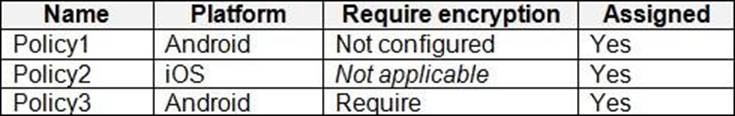
The device compliance policies have the assignments shown in the following table.
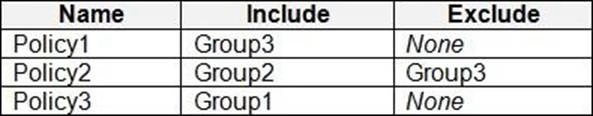
The device limit restrictions in Intune are configured as shown in the following table.
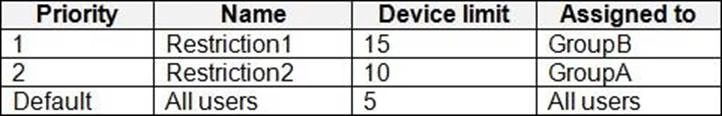
Requirements
Planned changes
Contoso plans to implement the following changes:
• Provide new computers to the Phoenix office users. The new computers have Windows 10 Pro preinstalled and were purchased already.
• Implement co-management for the computers.
Technical Requirements
Contoso must meet the following technical requirements:
• Ensure that the users in a group named Group4 can only access Microsoft Exchange Online from devices that are enrolled in Intune.
• Deploy Windows 10 Enterprise to the computers of the Phoenix office users by using Windows Autopilot.
• Create a provisioning package for new computers in the HR department.
• Block iOS devices from sending diagnostic and usage telemetry data.
• Use the principle of least privilege whenever possible.
• Enable the users in the MKG department to use App1.
• Pilot co-management for the IT department.
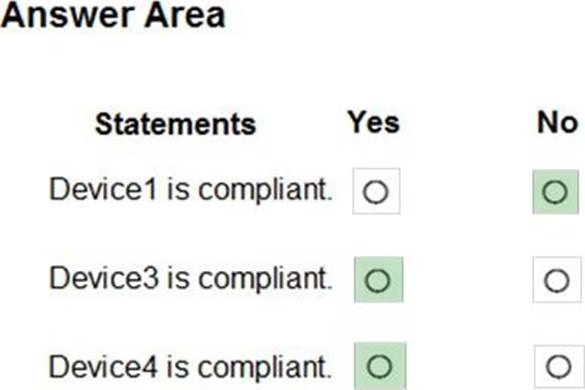
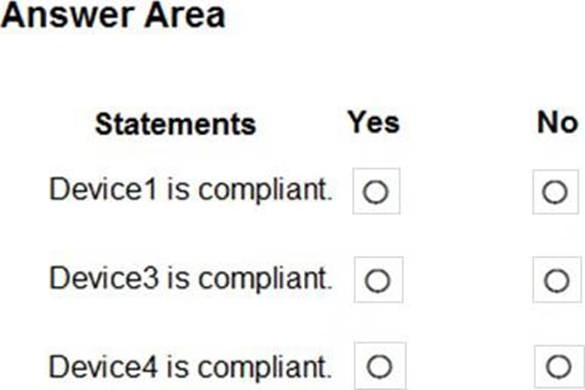
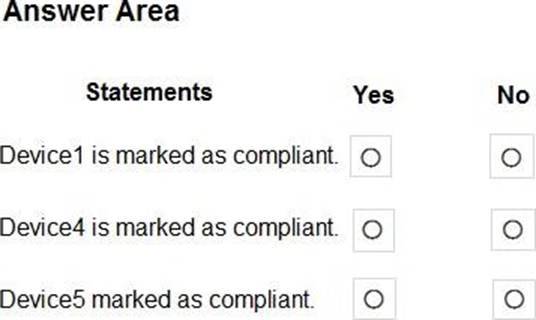
HOTSPOT
You are evaluating which devices are compliant.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Manage identity and compliance
Testlet 2
Case study
Overview
ADatum Corporation is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
ADatum has a Microsoft 365 E5 subscription.
Environment
Network Environment
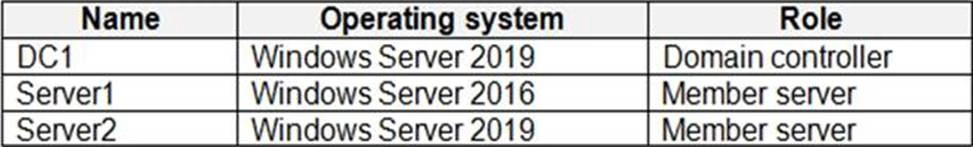
The network contains an on-premises Active Directory domain named adatum.com.
The domain contains the servers shown in the following table.
ADatum has a hybrid Azure AD tenant named adatum.com.
Users and Groups
The adatum.com tenant contains the users shown in the following table.
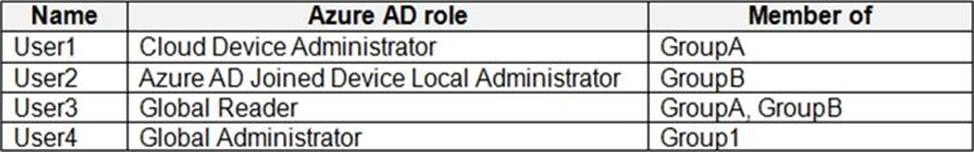
All users are assigned a Microsoft Office 365 license and an Enterprise Mobility + Security E3 license.
Enterprise State Roaming is enabled for Group1 and GroupA.
Group1 and Group2 have a Membership type of Assigned.
Devices
ADatum has the Windows 10 devices shown in the following table.
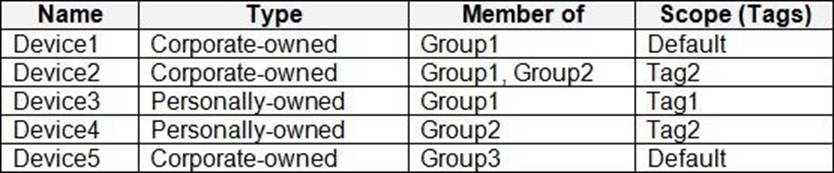
The Windows 10 devices are joined to Azure AD and enrolled in Microsoft Intune.
The Windows 10 devices are configured as shown in the following table.
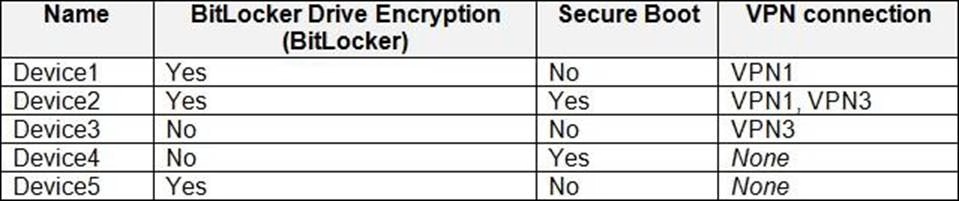
All the Azure AD joined devices have an executable file named C:AppA.exe and a folder named D:
Folder1.
Microsoft Intune Configuration
Microsoft Intune has the compliance policies shown in the following table.
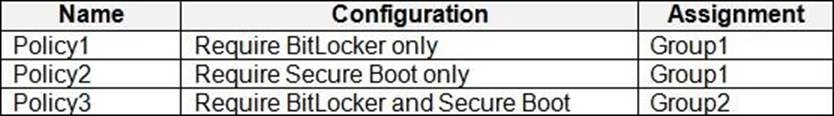
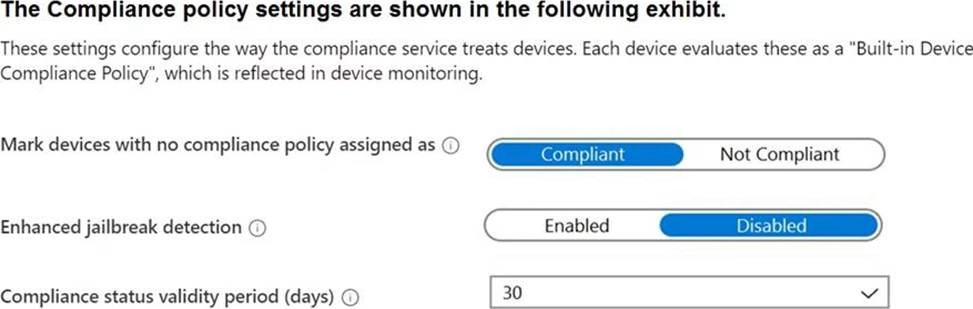
The Automatic Enrolment settings have the following configurations:
• MDM user scope GroupA
• MAM user scope: GroupB
You have an Endpoint protection configuration profile that has the following Controlled folder access settings:
• Name: Protection1
• Folder protection: Enable
• List of apps that have access to protected folders: CVAppA.exe
• List of additional folders that need to be protected: D:Folderi1
• Assignments – Included groups: Group2, GroupB
Windows Autopilot Configuration
ADatum has a Windows Autopilot deployment profile configured as shown in the following exhibit.
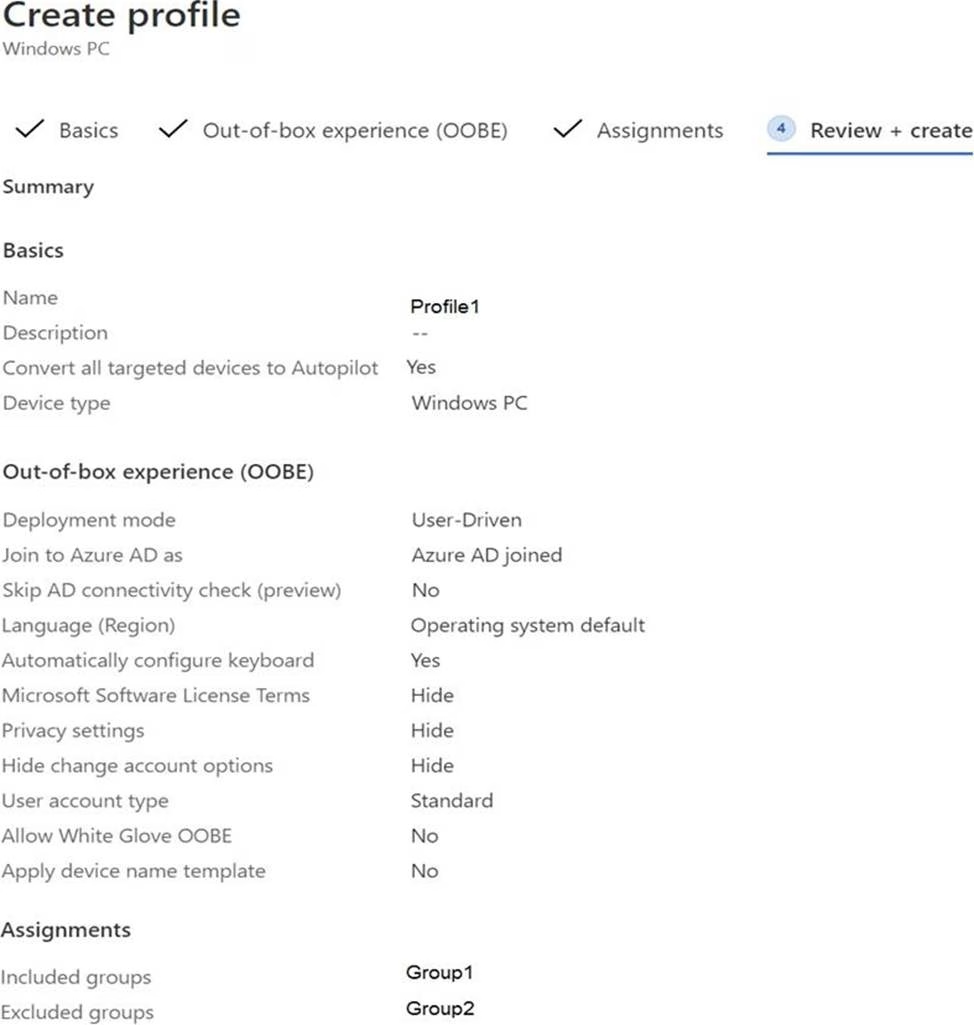
Currently, there are no devices deployed by using Windows Autopilot.
The Intune connector for Active Directory is installed on Server1.
Requirements
Planned Changes
ADatum plans to implement the following changes:
• Purchase a new Windows 10 device named Device6 and enroll the device in Intune
• New computers will be deployed by using Windows Autopilot and will be hybrid Azure AD joined.
• Deployed a network boundary configuration profile that will have the following settings:
– Name: Boundary1
– Network boundary: 192.168.1.0/24
– Scope tags: Tag1
– Assignments:
* Included groups: Group1, Group2
• Deploy two VPN configuration profiles named Connection1 and Connection2 that will have the following settings:
– Name: Connection1
– Connection name: VPN1
– Connection type: L2TP
– Assignments:
* Included groups: Group1, Group2, GroupA
* Excluded groups: —
– Name: Connection2
– Connection name: VPN2
– Connection type: IKEv2
– Assignments:
* Included groups: GroupA
* Excluded groups: GroupB
Technical Requirements
ADatum must meet the following technical requirements:
• Users in GroupA must be able to deploy new computers.
• Administrative effort must be minimized.
Which devices are registered by using the Windows Autopilot deployment service?
- A . Device1 only
- B . Device3 only
- C . Device1 and Device3 only
- D . Device1, Device2, and Device3
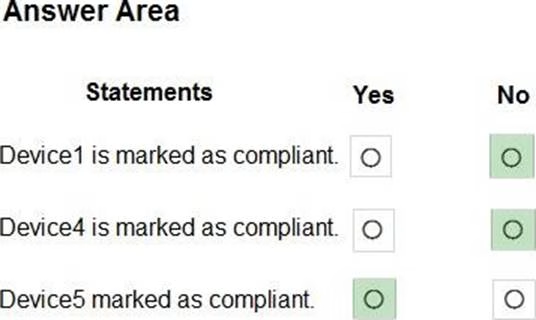
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
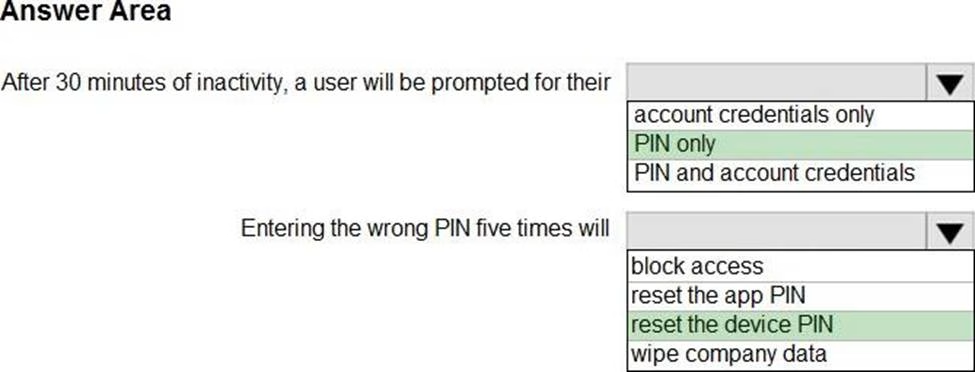
You have a Microsoft 365 subscription.
You use Microsoft Intune Suite to manage devices.
You have the iOS app protection policy shown in the following exhibit.
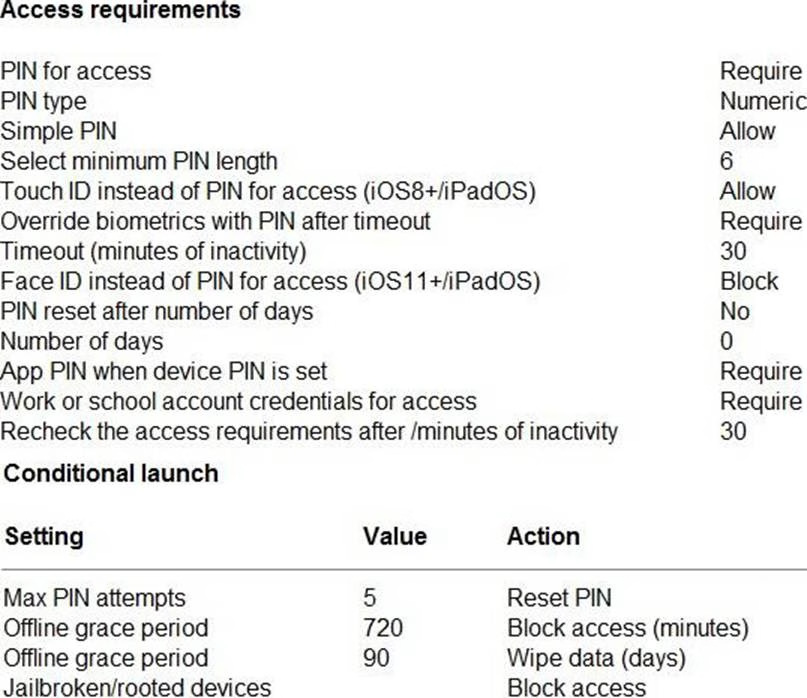
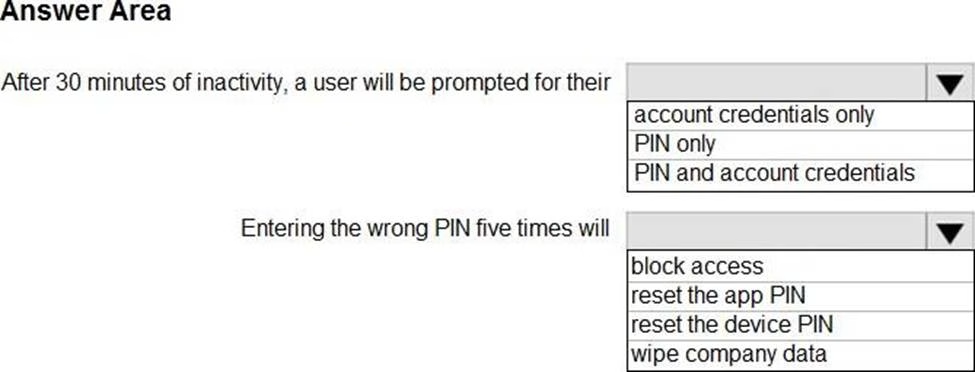
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
DRAG DROP
You have a Microsoft 365 subscription that includes Microsoft Intune.
You need to implement a Microsoft Defender for Endpoint solution that meets the following requirements:
• Enforces compliance for Defender for Endpoint by using Conditional Access
• Prevents suspicious scripts from running on devices
What should you configure? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.

Your network contains an on-premises Active Directory domain and an Azure AD tenant.
The Default Domain Policy Group Policy Object (GPO) contains the settings shown in the following table.
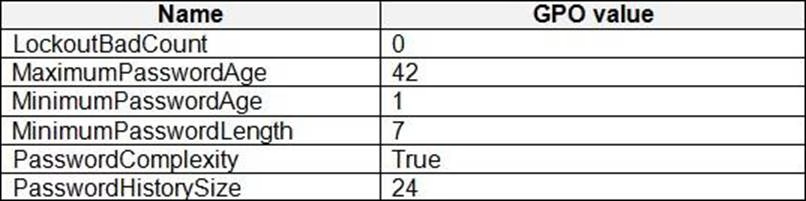
You need to migrate the existing Default Domain Policy GPO settings to a device configuration profile.
Which device configuration profile type template should you use?
- A . Administrative Templates
- B . Endpoint protection
- C . Device restrictions
- D . Custom
You have 100 computers that run Windows 10 and connect to an Azure Log Analytics workspace.
Which three types of data can you collect from the computers by using Log Analytics? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . failure events from the Security log
- B . the list of processes and their execution times
- C . the average processor utilization
- D . error events from the System log
- E . third-party application logs stored as text files
You use Microsoft Intune and Intune Data Warehouse.
You need to create a device inventory report that includes the data stored in the data warehouse.
What should you use to create the report?
- A . the Company Portal app
- B . Endpoint analytics
- C . the Azure portal app
- D . Microsoft Power BI
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows 10.
You have the groups shown in the following table.
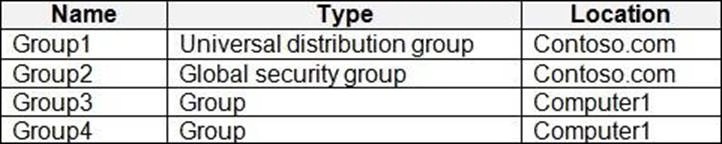
Which groups can you add to Group4?
- A . Group2 only
- B . Group1 and Group2 only
- C . Group2 and Group3 only
- D . Group1, Group2, and Group3
Latest MD-102 Dumps Valid Version with 98 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund