What are two high availability solution for routers with a single Routing Engine? (Choose two.)
- A . VRRP
- B . Non-stop active routing
- C . Graceful restart
- D . GRES
BC
Explanation:
https://www.juniper.net/documentation/us/en/software/junos/high-availability/topics/concept/high-availability-features-in-junos-introducing.html
The operations team reports that the network is now so large that it has become a challenge to manually create and maintain RSVP LSPs. You want to provide the team with the capability to create LSPs using a graphical interface.
Which system should you use in this scenario?
- A . OpenFlow
- B . Paragon Pathfinder
- C . Junos Space
- D . CSO
You are designing a new service provider network and need to select a label distribution mechanism that guides certain types of traffic along specific paths within the network.
Which two label distribution mechanisms would satisfy the requirements? (Choose two.)
- A . RSVP
- B . segment routing
- C . LDP
- D . BGP-LU
You are asked to design a WAN for a large enterprise. Each site must have multiple connections for redundancy. MPLS is not available at every site butit is preferred where available.
Which topology satisfies these design requirements?
- A . hub-and-spoke Internet WAN
- B . full mesh SD-WAN
- C . full mesh MPLS VPN
- D . hub-and-spoke SD-WAN
You are asked to provide a design proposal for a services provider’s core network. The network consists of both IPv2 and IPv4 addresses and must scale up to 50 core routing devices. As part of your design, you must in redundancy and ensure that future network expansion is easily incorporated.
In this scenario, which statement is correct regarding the BGP design?
- A . You should create a full mesh of EBGP neighbors in your core.
- B . You must use direct interface peering for your neighbors.
- C . You should use a pair of route reflectors with peering’s to all other core devices.
- D . You must separate the BGP network into multiple autonomous systems on geographic location.
What are two risks when using a source-based RTBH solution? (ChooseTWO)
- A . The attacker address could be a CGNAT address resulting in a larger service outage for users.
- B . The target of the attack may not support RTBH.
- C . The attacker’s address could be unknown.
- D . The target of an attack would be blocked resulting in a target being offline.
Which three statements are true about class-of-service (CoS) schedulers? (Choose three )
- A . Schedulers determine into which queue a packet should be assigned.
- B . Schedulers determine the packet transmission rate for each queue.
- C . Schedulers determine the packet markings that are used to prioritize traffic.
- D . Schedulers determine how packets are handled during times of congestion.
- E . Schedulers determine the size of buffer assigned to each queues.
Your organization expenenced a man-in-the-middle attack and must protect against future attacks.
In this scenario, what must you do to protect your network?
- A . Implement EVPN
- B . Implement MACsec.
- C . Implement destination-based RTBH
- D . Implement flowspec
Your company’s automation team is testing a controller-based solution for dynamic LSP management They do not want the topology acquisition process to allow the controller to become a transit node of the core network’s.
Which solution would fulfill the requirements?
- A . BGP-LS
- B . PCCD
- C . PCEP
- D . BGP-LU
Which statement describes Juniper Networks network management design best practices?
- A . You should ensure that automaton is used sparingly.
- B . You should ensure that only off-box automation scripts are used
- C . You should ensure that only on-box automaton scrips are used
- D . You should ensure that automation is used as much as possible.
Click the Exhibit button:
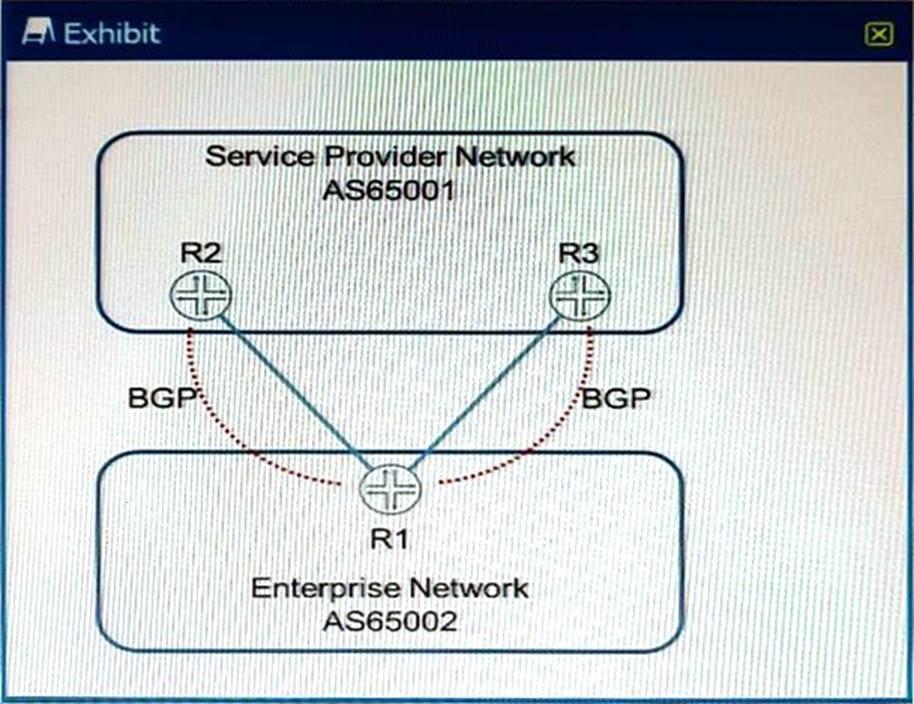
Referring to the exhibit, which mechanism is used to advertise routes from the enterprise network to the service provider network?
- A . BGP flowspec
- B . BGP export policies
- C . BGP import policies
- D . firewall filters
As a service provider network architect, you are working with a potential customer who wants to replace their WAN, consisting of two data centers, one HQ, and 76 branch offices Due to application latency requirements between branch offices, the customer insists that all traffic must take the most optimal path through the service provider network. The customer intends to encrypt all traffic between customer routers at each location.
Which WAN technology would you propose in this scenario?
- A . point-to-point Layer 2 VPNs
- B . Layer 3 VPN
- C . Internet as WAN
- D . H-VPLS
What are two benefits of including analytics in your network management design proposal? (Choose two.)
- A . Analytics can be used for troubleshooting and diagnosing network problems
- B . Analytics dynamically standardizes software and firmware versions.
- C . Analytics can allow administrators to evaluate and optimize WAN resources.
- D . Analytics dynamically makes network optimization change
You are developing a CoS policy for a service provider core network that In this scenario, which three statements are correct? (Choose three.)
- A . Core routers should use a common set of per-hop behaviors.
- B . Core routers should use shapers to ensure that customer traffic does not exceed allowed bandwidth.
- C . Core routers should use policers to ensure that customer traffic does not exceed allowed bandwidth.
- D . Core routers should use a consistent CoS configuration across the network.
- E . Core routers should use the DSCP markings already set on ingress traffic.
As a service provider network engineer, you are asked by management design a Layer 2 VPN product with a ‘’five nines’’ SLA.
Which mechanism will address this requirement?
- A . VRRP
- B . EVPN LAG
- C . GRES
- D . SyncE
What are two network management benefits of using devices in your design proposals?
- A . Virtualization allows network administrators to dynamically make configuration changes to all network devices.
- B . Virtualization can lower costs because there are fewer physical devices that need to be purchased and managed.
- C . Virtualization can increase the available network bandwidth because their interface speeds are only limited by the host device.
- D . Virtualization allows network administrators to dynamically add and remove services beingprovided
Your customer wants to enable their MX Series core so that a controller can dynamically manage their LSPs.
Which protocol provides this capability?
- A . BGP-LU
- B . PCEP
- C . PCRF
- D . BGP-LS
What are three limitations of using the Internet as the primary WAN service for enterprise organizations? (Choose three)
- A . generally higher cost
- B . no latency considerations
- C . lack of connectivity
- D . no quality of service guarantees
- E . no inherent security
Your customer’s enterprise is adding geographically dispersed branch offices and requires newWAN connections. The primary design consideration for this expansion is low cost.
Which type of WAN connection satisfies the customer’s requirement in this scenario?
- A . leased line dedicated circuit
- B . Internet connection with IPsec
- C . transparent Layer 2 service
- D . MPLS Layer 3 VPN
You are asked to create a point-to-multipoint DCI that does not overwhelm the data plane with MAC learning traffic.
Which protocol would you use in this situation?
- A . VPLS
- B . PPTP
- C . EVPN
- D . pseudowire