EC-Council CEH-001 Certified Ethical Hacker (CEH) Online Training
EC-Council CEH-001 Online Training
The questions for CEH-001 were last updated at Apr 16,2024.
- Exam Code: CEH-001
- Exam Name: Certified Ethical Hacker (CEH)
- Certification Provider: EC-Council
- Latest update: Apr 16,2024
Consider the following code:
URL: http://www.certified.com/search.pl?
text=<script>alert(document.cookie)</script>
If an attacker can trick a victim user to click a link like this, and the Web application does not validate input, then the victim’s browser will pop up an alert showing the users current set of cookies. An attacker can do much more damage, including stealing passwords, resetting your home page, or redirecting the user to another Web site.
What is the countermeasure against XSS scripting?
- A . Create an IP access list and restrict connections based on port number
- B . Replace "<" and ">" characters with "& l t;" and "& g t;" using server scripts
- C . Disable Javascript in IE and Firefox browsers
- D . Connect to the server using HTTPS protocol instead of HTTP
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network.
How can she accomplish this?
- A . Jayden can use the commanD. ip binding set.
- B . Jayden can use the commanD. no ip spoofing.
- C . She should use the commanD. no dhcp spoofing.
- D . She can use the commanD. ip dhcp snooping binding.
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network.
How can she accomplish this?
- A . Jayden can use the commanD. ip binding set.
- B . Jayden can use the commanD. no ip spoofing.
- C . She should use the commanD. no dhcp spoofing.
- D . She can use the commanD. ip dhcp snooping binding.
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network.
How can she accomplish this?
- A . Jayden can use the commanD. ip binding set.
- B . Jayden can use the commanD. no ip spoofing.
- C . She should use the commanD. no dhcp spoofing.
- D . She can use the commanD. ip dhcp snooping binding.
Jayden is a network administrator for her company. Jayden wants to prevent MAC spoofing on all the Cisco switches in the network.
How can she accomplish this?
- A . Jayden can use the commanD. ip binding set.
- B . Jayden can use the commanD. no ip spoofing.
- C . She should use the commanD. no dhcp spoofing.
- D . She can use the commanD. ip dhcp snooping binding.
As a normal three-way handshake mechanism system A should send an ACK packet to system B, however, system A does not send an ACK packet to system B. In this case client B is waiting for an ACK packet from client A.
This status of client B is called _________________
- A . "half-closed"
- B . "half open"
- C . "full-open"
- D . "xmas-open"
You just purchased the latest DELL computer, which comes pre-installed with Windows 7, McAfee antivirus software and a host of other applications. You want to connect Ethernet wire to your cable modem and start using the computer immediately. Windows is dangerously insecure when unpacked from the box, and there are a few things that you must do before you use it.
- A . New installation of Windows should be patched by installing the latest service packs and hotfixes
- B . Key applications such as Adobe Acrobat, Macromedia Flash, Java, Winzip etc., must have the latest security patches installed
- C . Install a personal firewall and lock down unused ports from connecting to your computer
- D . Install the latest signatures for Antivirus software
- E . Configure "Windows Update" to automatic
- F . Create a non-admin user with a complex password and logon to this account
- G . You can start using your computer as vendors such as DELL, HP and IBM would have already installed the latest service packs.
What is the problem with this ASP script (login.asp)?
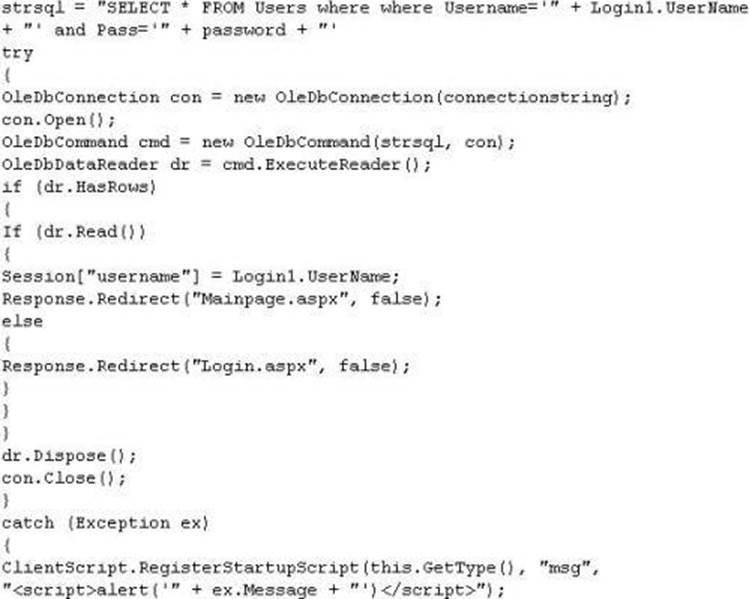
- A . The ASP script is vulnerable to Cross Site Scripting attack
- B . The ASP script is vulnerable to Session Splice attack
- C . The ASP script is vulnerable to XSS attack
- D . The ASP script is vulnerable to SQL Injection attack
Bob has set up three web servers on Windows Server 2008 IIS 7.0. Bob has followed all the recommendations for securing the operating system and IIS. These servers are going to run numerous e-commerce websites that are projected to bring in thousands of dollars a day. Bob is still concerned about the security of these servers because of the potential for financial loss. Bob has asked his company’s firewall administrator to set the firewall to inspect all incoming traffic on ports 80 and 443 to ensure that no malicious data is getting into the network.
Why will this not be possible?
- A . Firewalls cannot inspect traffic coming through port 443
- B . Firewalls can only inspect outbound traffic
- C . Firewalls cannot inspect traffic at all, they can only block or allow certain ports
- D . Firewalls cannot inspect traffic coming through port 80
What file system vulnerability does the following command take advantage of?
type c:anyfile.exe > c:winntsystem32calc.exe: anyfile.exe
- A . HFS
- B . Backdoor access
- C . XFS
- D . ADS
Latest CEH-001 Dumps Valid Version with 878 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

