EC-Council 312-50v11 Certified Ethical Hacker Exam – C|EH v11 Online Training
EC-Council 312-50v11 Online Training
The questions for 312-50v11 were last updated at Apr 20,2024.
- Exam Code: 312-50v11
- Exam Name: Certified Ethical Hacker Exam - C|EH v11
- Certification Provider: EC-Council
- Latest update: Apr 20,2024
Alice, a professional hacker, targeted an organization’s cloud services. She infiltrated the targets MSP provider by sending spear-phishing emails and distributed custom-made malware to compromise user accounts and gain remote access to the cloud service. Further, she accessed the target customer profiles with her MSP account, compressed the customer data, and stored them in the MSP. Then, she used this information to launch further attacks on the target organization .
Which of the following cloud attacks did Alice perform in the above scenario?
- A . Cloud hopper attack
- B . Cloud cryptojacking
- C . Cloudborne attack
- D . Man-in-the-cloud (MITC) attack
Which of the following types of SQL injection attacks extends the results returned by the original query, enabling attackers to run two or more statements if they have the same structure as the original one?
- A . Error-based injection
- B . Boolean-based blind SQL injection
- C . Blind SQL injection
- D . Allnion SQL injection
Which of the following tools is used to analyze the files produced by several packet-capture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
- A . tcptrace
- B . Nessus
- C . OpenVAS
- D . tcptraceroute
Ethical hacker jane Smith is attempting to perform an SQL injection attach. She wants to test the response time of a true or false response and wants to use a second command to determine whether the database will return true or false results for user IDs.
Which two SQL Injection types would give her the results she is looking for?
- A . Out of band and boolean-based
- B . Time-based and union-based
- C . union-based and error-based
- D . Time-based and boolean-based
What is the first step for a hacker conducting a DNS cache poisoning (DNS spoofing) attack against an organization?
- A . The attacker queries a nameserver using the DNS resolver.
- B . The attacker makes a request to the DNS resolver.
- C . The attacker forges a reply from the DNS resolver.
- D . The attacker uses TCP to poison the ONS resofver.
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst what would you conclude about the attack?
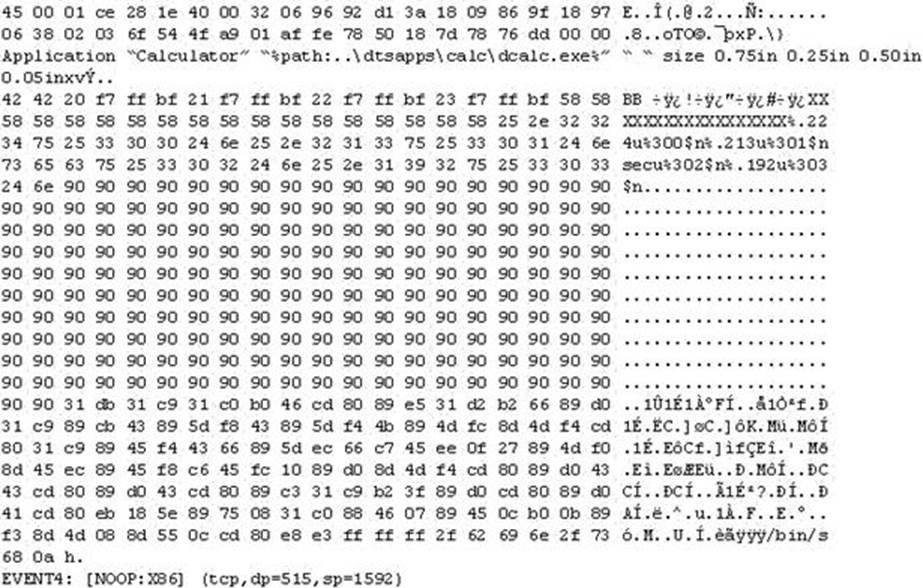
- A . The buffer overflow attack has been neutralized by the IDS
- B . The attacker is creating a directory on the compromised machine
- C . The attacker is attempting a buffer overflow attack and has succeeded
- D . The attacker is attempting an exploit that launches a command-line shell
What hacking attack is challenge/response authentication used to prevent?
- A . Replay attacks
- B . Scanning attacks
- C . Session hijacking attacks
- D . Password cracking attacks
John wants to send Marie an email that includes sensitive information, and he does not trust the network that he is connected to. Marie gives him the idea of using PGP .
What should John do to communicate correctly using this type of encryption?
- A . Use his own public key to encrypt the message.
- B . Use Marie’s public key to encrypt the message.
- C . Use his own private key to encrypt the message.
- D . Use Marie’s private key to encrypt the message.
Which of the following steps for risk assessment methodology refers to vulnerability identification?
- A . Determines if any flaws exist in systems, policies, or procedures
- B . Assigns values to risk probabilities; Impact values.
- C . Determines risk probability that vulnerability will be exploited (High. Medium, Low)
- D . Identifies sources of harm to an IT system. (Natural, Human. Environmental)
Which system consists of a publicly available set of databases that contain domain name registration contact information?
- A . WHOIS
- B . CAPTCHA
- C . IANA
- D . IETF
Latest 312-50v11 Dumps Valid Version with 432 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

