EC-Council 312-50v11 Certified Ethical Hacker Exam – C|EH v11 Online Training
EC-Council 312-50v11 Online Training
The questions for 312-50v11 were last updated at Dec 19,2025.
- Exam Code: 312-50v11
- Exam Name: Certified Ethical Hacker Exam - C|EH v11
- Certification Provider: EC-Council
- Latest update: Dec 19,2025
Peter is surfing the internet looking for information about DX Company .
Which hacking process is Peter doing?
- A . Scanning
- B . Footprinting
- C . Enumeration
- D . System Hacking
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator’s Computer to update the router configuration .
What type of an alert is this?
- A . False negative
- B . True negative
- C . True positive
- D . False positive
Study the following log extract and identify the attack.
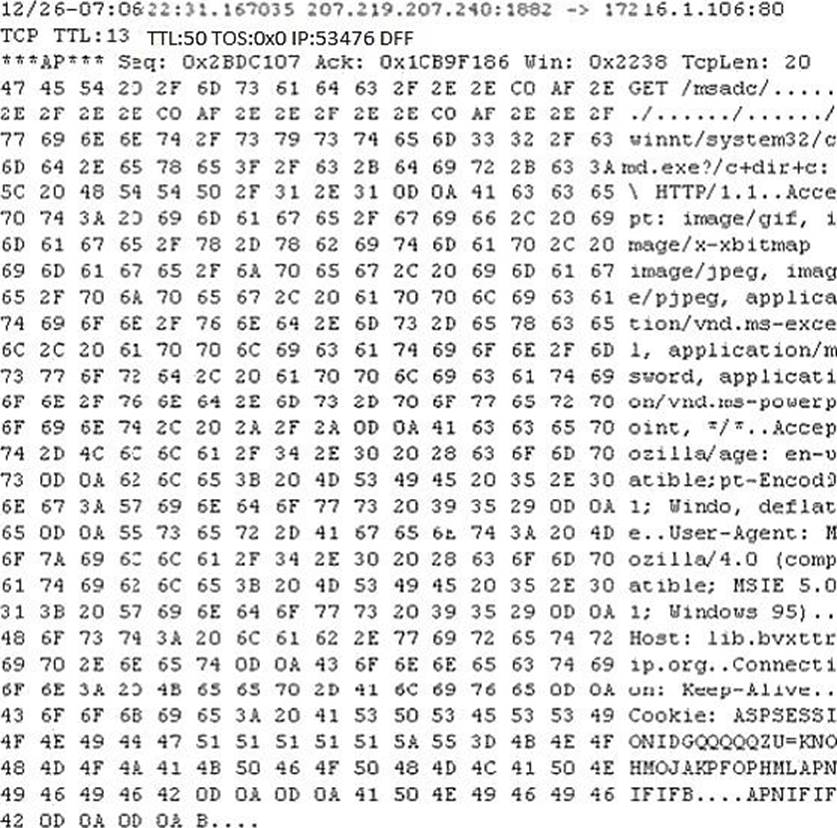
- A . Hexcode Attack
- B . Cross Site Scripting
- C . Multiple Domain Traversal Attack
- D . Unicode Directory Traversal Attack
An attacker identified that a user and an access point are both compatible with WPA2 and WPA3 encryption. The attacker installed a rogue access point with only WPA2 compatibility in the vicinity and forced the victim to go through the WPA2 four-way handshake to get connected. After the connection was established, the attacker used automated tools to crack WPA2-encrypted messages .
What is the attack performed in the above scenario?
- A . Timing-based attack
- B . Side-channel attack
- C . Downgrade security attack
- D . Cache-based attack
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
- A . Birthday
- B . Brute force
- C . Man-in-the-middle
- D . Smurf
What is the proper response for a NULL scan if the port is open?
- A . SYN
- B . ACK
- C . FIN
- D . PSH
- E . RST
- F . No response
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of these switches.
If these switches’ ARP cache is successfully flooded, what will be the result?
- A . The switches will drop into hub mode if the ARP cache is successfully flooded.
- B . If the ARP cache is flooded, the switches will drop into pix mode making it less susceptible to attacks.
- C . Depending on the switch manufacturer, the device will either delete every entry in its ARP cache or reroute packets to the nearest switch.
- D . The switches will route all traffic to the broadcast address created collisions.
What did the following commands determine?
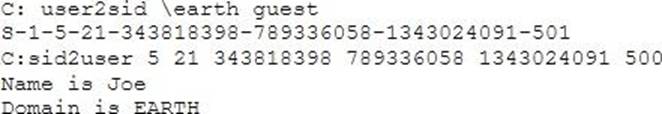
- A . That the Joe account has a SID of 500
- B . These commands demonstrate that the guest account has NOT been disabled
- C . These commands demonstrate that the guest account has been disabled
- D . That the true administrator is Joe
- E . Issued alone, these commands prove nothing
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
- A . All are hacking tools developed by the legion of doom
- B . All are tools that can be used not only by hackers, but also security personnel
- C . All are DDOS tools
- D . All are tools that are only effective against Windows
- E . All are tools that are only effective against Linux
Which of the following statements is TRUE?
- A . Packet Sniffers operate on the Layer 1 of the OSI model.
- B . Packet Sniffers operate on Layer 2 of the OSI model.
- C . Packet Sniffers operate on both Layer 2 & Layer 3 of the OSI model.
- D . Packet Sniffers operate on Layer 3 of the OSI model.
Latest 312-50v11 Dumps Valid Version with 432 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

