- All Exams Instant Download
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used
DRAG DROP
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used.
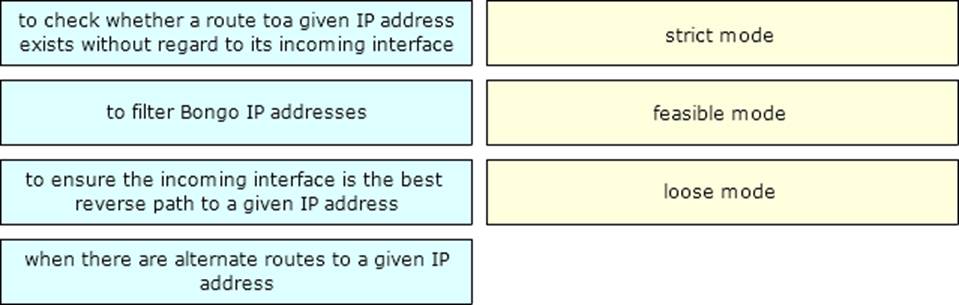
Answer: 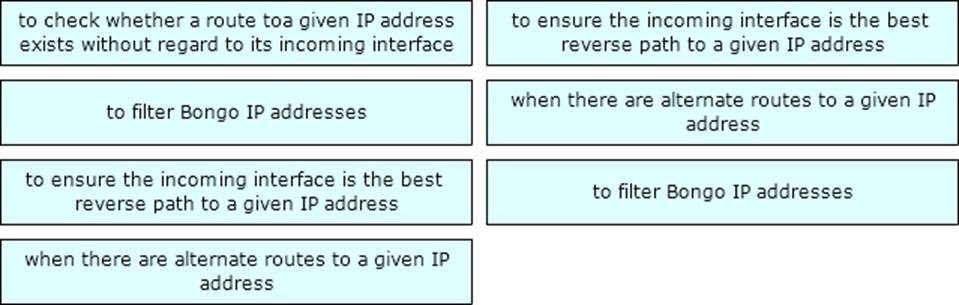
Latest 400-007 Dumps Valid Version with 141 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

