Does this meet the goal?
Topic 1, Contoso, Ltd
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answer and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The offices have the users and devices shown in the following table.
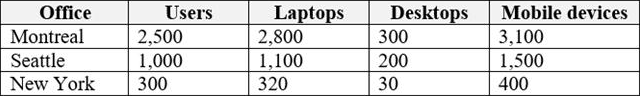
Contoso recently purchased a Microsoft 365 E5 subscription.
Existing Environment
The network contains an Active directory forest named contoso.com and a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
You recently configured the forest to sync to the Azure AD tenant.
You add and then verify adatum.com as an additional domain name.
All servers run Windows Server 2016.
All desktop computers and laptops run Windows 10 Enterprise and are joined to contoso.com.
All the mobile devices in the Montreal and Seattle offices run Android. All the mobile devices in the New York office run iOS.
Contoso has the users shown in the following table.

Contoso has the groups shown in the following table.
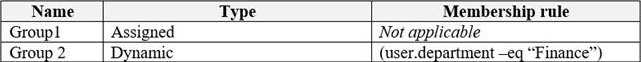
Microsoft Office 365 licenses are assigned only to Group2.
The network also contains external users from a vendor company who have Microsoft accounts that use a suffix of @outlook.com.
Requirements
Planned Changes
Contoso plans to provide email addresses for all the users in the following domains:
✑ East.adatum.com
✑ Contoso.adatum.com
✑ Humongousinsurance.com
Technical Requirements
Contoso identifies the following technical requirements:
✑ All new users must be assigned Office 365 licenses automatically.
✑ The principle of least privilege must be used whenever possible.
Security Requirements
Contoso identifies the following security requirements:
✑ Vendors must be able to authenticate by using their Microsoft account when accessing Contoso resources.
✑ User2 must be able to view reports and schedule the email delivery of security and compliance reports.
✑ The members of Group1 must be required to answer a security question before changing their password.
✑ User3 must be able to manage Office 365 connectors.
✑ User4 must be able to reset User3 password.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You need to assign User2 the required roles to meet the security requirements.
Solution: From the Office 365 admin center, you assign User2 the Security Reader role. From the Exchange admin center, you assign User2 the Compliance Management role.
Does this meet the goal?
A . Yes
B . NO
Answer: A
Explanation:
✑ User2 must be able to view reports and schedule the email delivery of security and compliance reports.
The Security Reader role can view reports.
The Compliance Management role can schedule the email delivery of security and compliance reports.
Reference: https://docs.microsoft.com/en-us/exchange/permissions-exo/permissions-exo
Latest MS-100 Dumps Valid Version with 297 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

