CyberArk CAU201 CyberArk Defender Online Training
CyberArk CAU201 Online Training
The questions for CAU201 were last updated at Dec 10,2025.
- Exam Code: CAU201
- Exam Name: CyberArk Defender
- Certification Provider: CyberArk
- Latest update: Dec 10,2025
When managing SSH keys, the CPM stores the Public Key
- A . In the Vault
- B . On the target server
- C . A & B
- D . Nowhere because the public key can always be generated from the private key.
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
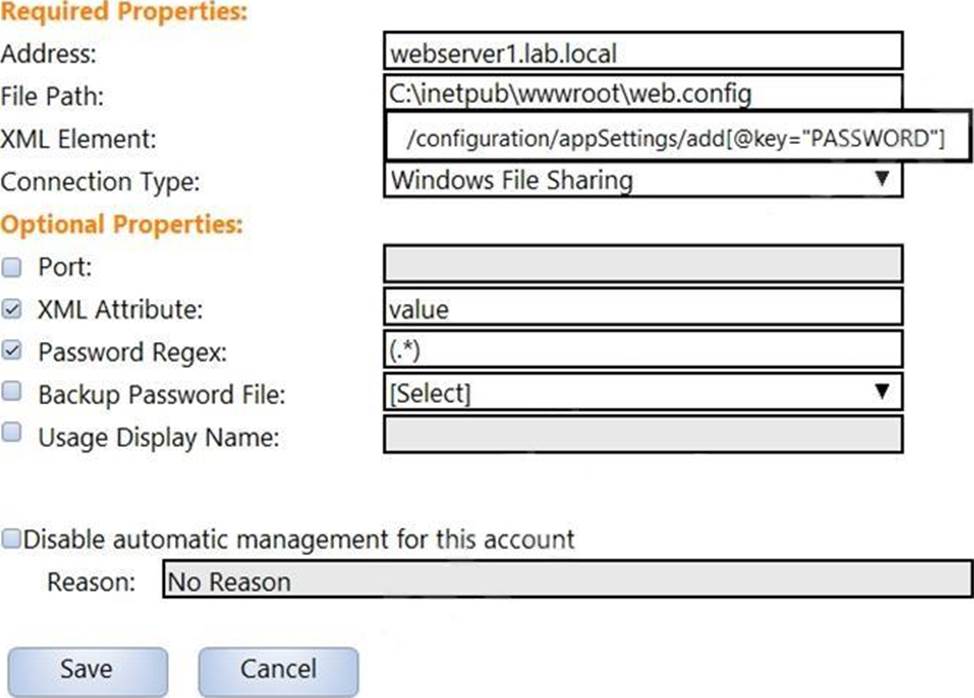
What is the least intrusive way to accomplish this?
- A . Use the “change” button on the usage’s details page.
- B . Use the “change” button on the parent account’s details page.
- C . Use the “sync” button on the usage’s details page.
- D . Use the “reconcile” button on the parent account’s details page.
What is the maximum number of levels of authorization you can set up in Dual Control?
- A . 1
- B . 2
- C . 3
- D . 4
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment.
Which security configuration should you recommend?
- A . Configure one-time passwords for the appropriate platform in Master Policy.
- B . Configure shared account mode on the appropriate safe.
- C . Configure both one-time passwords and exclusive access for the appropriate platform in Master Policy.
- D . Configure object level access control on the appropriate safe.
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
- A . Vault Replicator
- B . PAS Reporter
- C . Remote Control Agent
- D . Syslog
Which utilities could you use to change debugging levels on the vault without having to restart the vault. Select all that apply.
- A . PAR Agent
- B . PrivateArk Server Central Administration
- C . Edit DBParm.ini in a text editor.
- D . Setup.exe
CyberArk recommends implementing object level access control on all Safes.
- A . True
- B . False
Within the Vault each password is encrypted by:
- A . the server key
- B . the recovery public key
- C . the recovery private key
- D . its own unique key
VAULT authorizations may be granted to_____.
- A . Vault Users
- B . Vault Groups
- C . LDAP Users
- D . LDAP Groups
Latest CAU201 Dumps Valid Version with 112 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

