CWNP CWSP-207 CWNP Wireless Security Professional (CWSP) Online Training
CWNP CWSP-207 Online Training
The questions for CWSP-207 were last updated at Jul 19,2025.
- Exam Code: CWSP-207
- Exam Name: CWNP Wireless Security Professional (CWSP)
- Certification Provider: CWNP
- Latest update: Jul 19,2025
What security vulnerabilities may result from a lack of staging, change management, and installation procedures for WLAN infrastructure equipment? (Choose 2)
- A . The WLAN system may be open to RF Denial-of-Service attacks
- B . WIPS may not classify authorized, rogue, and neighbor APs accurately
- C . Authentication cracking of 64-bit Hex WPA-Personal PSK
- D . Management interface exploits due to the use of default usernames and passwords for AP management
- E . AES-CCMP encryption keys may be decrypted
In a point-to-point bridge environment where 802.1X/EAP is used for bridge authentication, what device in the network acts as the 802.1X supplicant?
- A . Nonroot bridge
- B . WLAN controller
- C . Root bridge
- D . RADIUS server
- E . Layer 3 core switch
What are some of the recommendations that might be made to a customer after a successful WLAN security audit? (Choose all that apply.)
- A . Physical security
- B . Employee training
- C . Dynamic RF configuration
- D . Monitoring capabilities
- E . AP and client power settings
What encryption methods are defined by the IEEE 802.11-2012 standard? (Choose all that apply.)
- A . 3DES
- B . WPA-2
- C . SSL
- D . TKIP
- E . CCMP
- F . WEP
Evan has configured a laptop and an AP, each with two WEP keys. WEP key 1 is the same on both devices, and WEP key 2 is the same on both devices.
He configured the laptop to use WEP key 1 to encrypt its data. He configured the AP to use WEP key 2 to encrypt its data. Will this configuration work?
- A . No, since there is only one WEP key on each device.
- B . No, since the value of the WEP key must be identical on both the laptop and the AP.
- C . Yes, as long as the value of WEP key 1 is identical on both computers and the value of WEP key 2 is identical on both computers.
- D . Yes. The laptop and AP will only use the first WEP key, so as long as the value of these keys is identical, the configuration will work.
- E . Yes. The laptop and AP will attempt to use each of the WEP keys when decrypting a frame.
What is the main purpose of using a WLAN protocol analyzer during the Layer 2 analysis of a WLAN security audit? (Choose all that apply.)
- A . Identifying unauthorized devices
- B . Auditing the wired infrastructure
- C . Performing penetration testing
- D . Validating security compliance of authorized devices
- E . Auditing the WIPS
What type of WLAN security is depicted by this graphic?
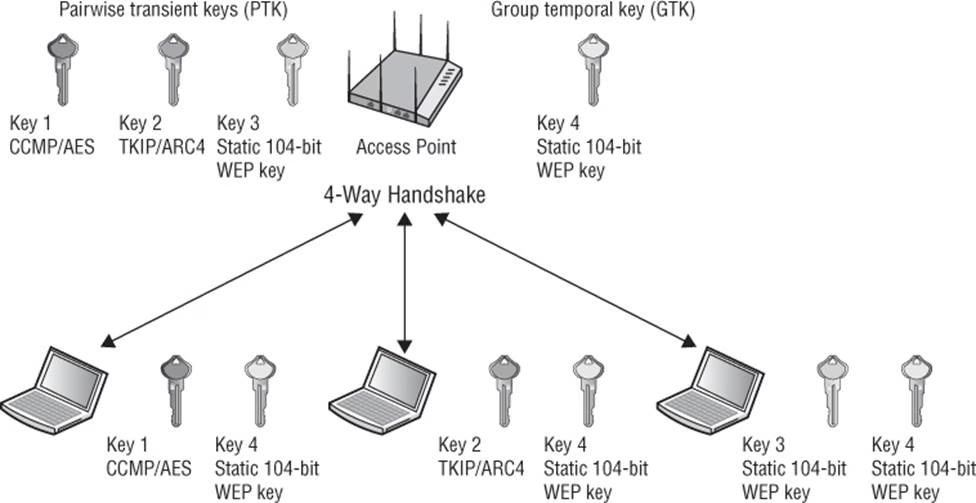
- A . RSN
- B . TSN
- C . VPN
- D . WPS
- E . WMM
What disadvantage does EAP-TLS have when compared with PEAPv0 EAP/MSCHAPv2 as an 802.11 WLAN security solution?
- A . Fast/secure roaming in an 802.11 RSN is significantly longer when EAP-TLS is in use.
- B . EAP-TLS does not protect the client’s username and password inside an encrypted tunnel.
- C . EAP-TLS cannot establish a secure tunnel for internal EAP authentication.
- D . EAP-TLS is supported only by Cisco wireless infrastructure and client devices.
- E . EAP-TLS requires extensive PKI use to create X.509 certificates for both the server and all clients, which increases administrative overhead.
ABC Company uses the wireless network for highly sensitive network traffic. For that reason, they intend to protect their network in all possible ways.
They are continually researching new network threats and new preventative measures. They are interested in the security benefits of 802.11w, but would like to know its limitations.
What types of wireless attacks are protected by 802.11w? (Choose 2)
- A . RF DoS attacks
- B . Layer 2 Disassociation attacks
- C . Robust management frame replay attacks
- D . Social engineering attacks
Which method of guest management can be used by a company to gather valuable personal information about guest users?
- A . Social login
- B . Kiosk mode
- C . Receptionist registration
- D . Self-registration
- E . Employee sponsorship
Latest CWSP-207 Dumps Valid Version with 440 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

