CWNP CWSP-207 CWNP Wireless Security Professional (CWSP) Online Training
CWNP CWSP-207 Online Training
The questions for CWSP-207 were last updated at Dec 13,2025.
- Exam Code: CWSP-207
- Exam Name: CWNP Wireless Security Professional (CWSP)
- Certification Provider: CWNP
- Latest update: Dec 13,2025
The IEEE 802.11-2012 standard requires an authentication and key management protocol (AKMP) that can be either a preshared (PSK) or an EAP protocol used during 802.1X/EAP authentication.
What is another name for PSK authentication? (Choose all that apply.)
- A . Wi-Fi Protected Setup
- B . WPA/WPA2-Personal
- C . WPA/WPA2-PSK
- D . WPA/WPA2-Preshared Key
- E . WPA/WPA2-Passphrase
When two client stations are already associated to an AP, which handshake is used to create a different unicast key that the two client stations can use for a private conversation while they remain associated to the AP?
- A . Mesh Group Key Handshake
- B . Group Key Handshake
- C . 4-Way Handshake
- D . 2-Way Handshake
- E . TDLS Peer Key Handshake
What operations must occur before the virtual controlled port of the authenticator becomes unblocked? (Choose all that apply.)
- A . 802.1X/EAP authentication
- B . 4-Way Handshake
- C . 2-Way Handshake
- D . RADIUS proxy
Bob the WLAN administrator is troubleshooting an IPsec VPN problem that has been deployed as the security solution over a point-to-point 802.11 wireless bridge link between two buildings. Bob cannot get the VPN tunnel to establish and notices that there is a certificate error during the IKE Phase 1 exchange.
What are the possible causes of this problem? (Choose all that apply.)
- A . The VPN server behind the root bridge is using AES-256 encryption, and the VPN endpoint device behind the nonroot bridge is using AES-192 encryption.
- B . The VPN server behind the root bridge is using SHA-1 hash for data integrity, and the VPN endpoint device behind the nonroot bridge is using MD-5 for data integrity.
- C . The root CA certificate installed on the VPN device behind the nonroot bridge was not used to sign the server certificate on the VPN server behind the root bridge.
- D . The clock settings of the VPN server that is deployed behind the root bridge predate the creation of the server certificate.
- E . The public/private IP address settings are misconfigured on the VPN device behind the nonroot bridge.
Which of the following are the security measures that are needed to maintain the security of wireless LAN?
Each correct answer represents a complete solution. Choose all that apply.
- A . WIDS
- B . Firewalls
- C . WLAN controller
- D . WIPS
This graphic shows a WLAN discovery tool screen capture.
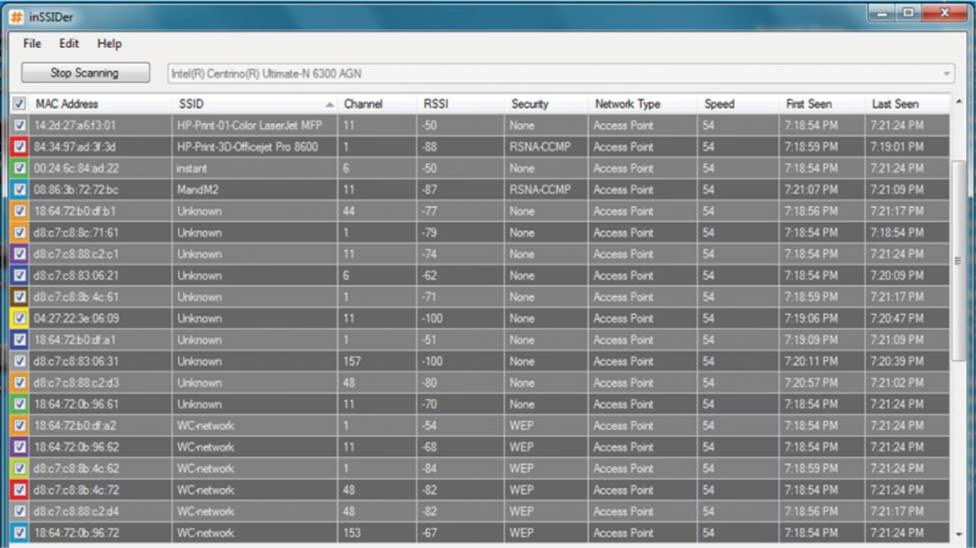
How many SSIDs are configured with cloaking enabled? (Choose all that apply.)
- A . None
- B . At least ten
- C . One
- D . Ten
- E . Exact number cannot be determined
Which technologies use the RC4 or ARC4 cipher? (Choose all that apply.)
- A . Static WEP
- B . Dynamic WEP
- C . PPTP
- D . L2TP
- E . MPPE
You have been tasked with configuring a secure WLAN for 600 APs at the corporate offices. All the APs and employee Windows laptops have been configured for 802.1X/EAP.
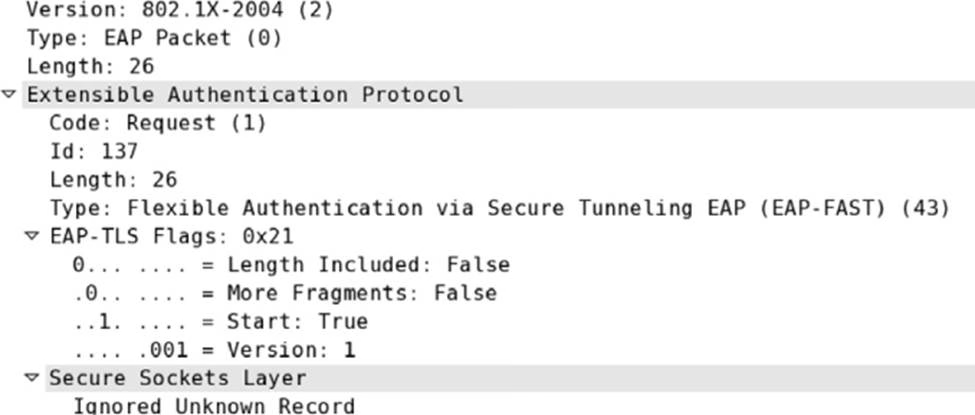
The domain user accounts are failing authentication with every attempt. After looking at some packet captures of the authentication failures, you have determined that an SSL/TLS tunnel is never created.
After viewing the graphic shown here, determine the possible causes of the problem. (Choose all that apply.)
- A . The Windows laptops are missing a client certificate.
- B . The incorrect root certificate is selected in the supplicant.
- C . The server certificate has expired.
- D . PACs have not been provisioned properly.
- E . The root certificate has expired.
You must locate non-compliant 802.11 devices.
Which one of the following tools will you use and why?
- A . A spectrum analyzer, because it can show the energy footprint of a device using WPA differently from a device using WPA2.
- B . A spectrum analyzer, because it can decode the PHY preamble of a non-compliant device.
- C . A protocol analyzer, because it can be used to view the spectrum energy of non-compliant 802.11 devices, which is always different from compliant devices.
- D . A protocol analyzer, because it can be used to report on security settings and regulatory or rule compliance
What is one advantage of using EAP-TTLS instead of EAP-TLS as an authentication mechanism in an 802.11 WLAN?
- A . EAP-TTLS sends encrypted supplicant credentials to the authentication server, but EAP-TLS uses unencrypted user credentials.
- B . EAP-TTLS supports client certificates, but EAP-TLS does not.
- C . EAP-TTLS does not require an authentication server, but EAP-TLS does.
- D . EAP-TTLS does not require the use of a certificate for each STA as authentication credentials, but EAP-TLS does.
Latest CWSP-207 Dumps Valid Version with 440 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

