CWNP CWSP-207 CWNP Wireless Security Professional (CWSP) Online Training
CWNP CWSP-207 Online Training
The questions for CWSP-207 were last updated at Jul 18,2025.
- Exam Code: CWSP-207
- Exam Name: CWNP Wireless Security Professional (CWSP)
- Certification Provider: CWNP
- Latest update: Jul 18,2025
CCMP is an acronym made up of multiple components.
Which of the following is an expanded version of this acronym? (Choose all that apply)
- A . Counter Mode with Cipher-Block Chaining Message Authentication Code Protocol
- B . Counter Message with Cipher-Block Chaining Mode Authentication Code Protocol
- C . CTR with CBC-MAC Protocol
- D . Counter Mode with CBC-MAC Protocol
- E . None of these is accurate.
Which RADIUS attribute is used to protect encapsulated EAP frames within RADIUS packets?
- A . (11) Filter-Id
- B . (26) Vendor-Specific
- C . (40) Acct-Status-Type
- D . (79) EAP-Message
- E . (80) Message-Authenticator
Which of these security methods is being considered by the Wi-Fi Alliance as a replacement for PSK authentication?
- A . Per-user/per-device PSK
- B . Wi-Fi Protected Setup (WPS)
- C . Simultaneous Authentication of Equals (SAE)
- D . EAP-PSK
- E . WPA2 Personal
After consulting your written security policy, to meet the new demands of an industry standard with which your organization must be compliant, an administrator logs into your WLAN controller and changes the authentication and encryption configurations on all your APs.
The help desk becomes overwhelmed with calls from angry users stating that they can no longer access the network. One by one, the users are reconfigured to reconnect to the network, causing significant loss of time.
Which portion of a well-written security policy is most likely missing from your company’s wireless security policy that caused this problem?
- A . External influence compliance
- B . Authentication requirements
- C . Encryption compliance
- D . Change control process
- E . User notification process
After consulting your written security policy, to meet the new demands of an industry standard with which your organization must be compliant, an administrator logs into your WLAN controller and changes the authentication and encryption configurations on all your APs.
The help desk becomes overwhelmed with calls from angry users stating that they can no longer access the network. One by one, the users are reconfigured to reconnect to the network, causing significant loss of time.
Which portion of a well-written security policy is most likely missing from your company’s wireless security policy that caused this problem?
- A . External influence compliance
- B . Authentication requirements
- C . Encryption compliance
- D . Change control process
- E . User notification process
168.80.5/24
User VLANS:
VLAN 201
VLAN 202
VLAN 203
SSIDs:
SSID-1: (employee) security: (802.1X/EAP/CCMP) – VLAN 201 – BSSID (00:08:12:43:0F:30)
SSID-2 (voice) security: (PSK/TKIP and WEP) – VLAN 202 – BSSID (00:08:12:43:0F:31)
SSID-3: (guest) security: (WEP) – VLAN 203 – BSSID (00:08:12:43:0F:32)
Based on the settings on Bob’s access point, what type of WLAN security exits within the coverage area of the AP? (Choose all that apply.)
- A . Closed security network
- B . Transition security network
- C . Pre-RSNA security network
- D . Open security network
- E . Robust security network
802.11 pre-RSNA security defines which wireless security solution?
- A . Dynamic WEP
- B . 802.1X/EAP
- C . 128-bit static WEP
- D . Temporal Key Integrity Protocol
- E . CCMP/AES
Given: ABC Company has recently installed a WLAN controller and configured it to support WPA2-Enterprise security.
The administrator has configured a security profile on the WLAN controller for each group within the company (Marketing, Sales, and Engineering).
How are authenticated users assigned to groups so that they receive the correct security profile within the WLAN controller?
- A . The WLAN controller polls the RADIUS server for a complete list of authenticated users and groups after each user authentication.
- B . The RADIUS server sends a group name return list attribute to the WLAN controller during every successful user authentication.
- C . The RADIUS server forwards the request for a group attribute to an LDAP database service, and LDAP sends the group attribute to the WLAN controller.
- D . The RADIUS server sends the list of authenticated users and groups to the WLAN controller as part of a 4- Way Handshake prior to user authentication.
After viewing the frame capture in the graphic shown here, identify which type of encryption method is being used.
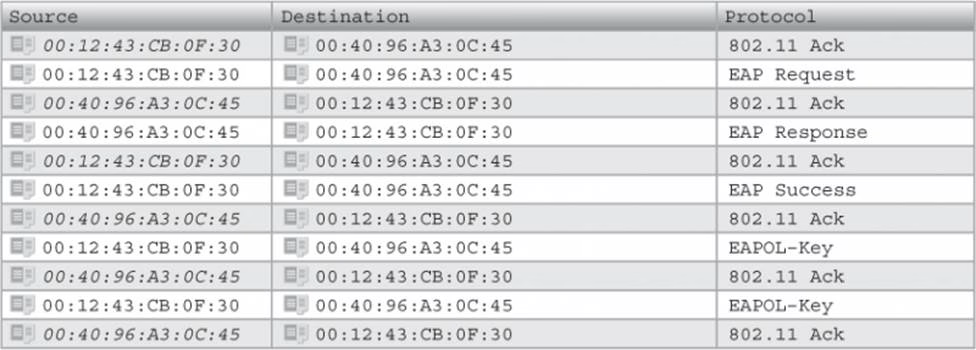
- A . TKIP
- B . CCMP
- C . xSec
- D . Fortress
- E . WEP
- F . AES
Given: In a security penetration exercise, a WLAN consultant obtains the WEP key of XYZ Corporation’s wireless network.
Demonstrating the vulnerabilities of using WEP, the consultant uses a laptop running a software AP in an attempt to hijack the authorized user’s connections. XYZ’s legacy network is using 802.11n APs with 802.11b, 11g, and 11n client devices.
With this setup, how can the consultant cause all of the authorized clients to establish Layer 2 connectivity with the software access point?
- A . All WLAN clients will reassociate to the consultant’s software AP if the consultant’s software AP provides the same SSID on any channel with a 10 dB SNR improvement over the authorized AP.
- B . A higher SSID priority value configured in the Beacon frames of the consultant’s software AP will take priority over the SSID in the authorized AP, causing the clients to reassociate.
- C . When the RF signal between the clients and the authorized AP is temporarily disrupted and the consultant’s software AP is using the same SSID on a different channel than the authorized AP, the clients will reassociate to the software AP.
- D . If the consultant’s software AP broadcasts Beacon frames that advertise 802.11g data rates that are faster rates than XYZ’s current 802.11b data rates, all WLAN clients will reassociate to the faster AP.
Latest CWSP-207 Dumps Valid Version with 440 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

