CORRECT TEXT
CORRECT TEXT
Cluster: scanner
Master node: controlplane
Worker node: worker1
You can switch the cluster/configuration context using the following command:
[desk@cli] $ kubectl config use-context scanner
Given:
You may use Trivy’s documentation.
Task:
Use the Trivy open-source container scanner to detect images with severe vulnerabilities used by Pods in the namespace nato.
Look for images with High or Critical severity vulnerabilities and delete the Pods that use those images.
Trivy is pre-installed on the cluster’s master node. Use cluster’s master node to use Trivy.
Answer: [controlplane@cli] $ k get pods -n nato -o yaml | grep "image: "[controlplane@cli] $ trivy image <image-name>[controlplane@cli] $ k delete pod <vulnerable-pod> -n nato
[desk@cli] $ ssh controlnode[controlplane@cli] $ k get pods -n nato
NAME READY STATUS RESTARTS AGE
alohmora 1/1 Running 0 3m7s
c3d3 1/1 Running 0 2m54s
neon-pod 1/1 Running 0 2m11s
thor 1/1 Running 0 58s
[controlplane@cli] $ k get pods -n nato -o yaml | grep "image: "
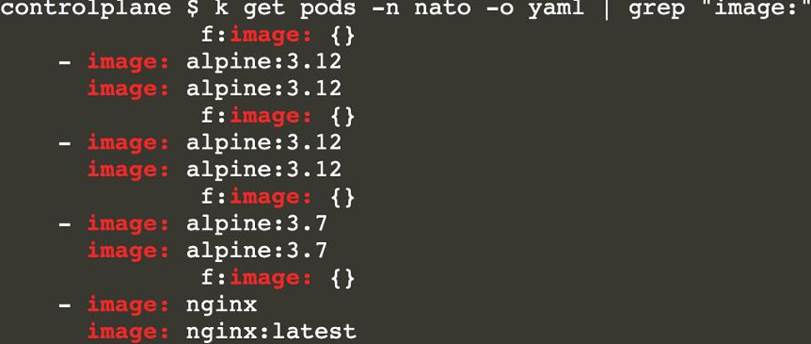
Text
Description automatically generated[controlplane@cli] $ trivy image <image-name>
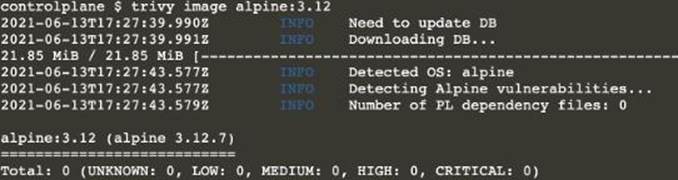
Text
Description automatically generated
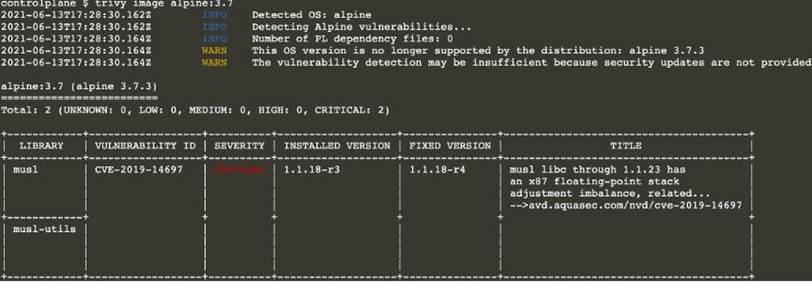
Text
Description automatically generated
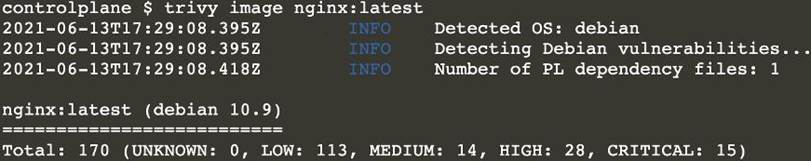
Text
Description automatically generatedNote: As there are 2 images have vulnerability with severity Hight & Critical. Delete containers for nginx:latest & alpine:3.7 [controlplane@cli] $ k delete pod thor -n nato
Latest CKS Dumps Valid Version with 44 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

