CompTIA CAS-003 CompTIA Advanced Security Practitioner (CASP) Online Training
CompTIA CAS-003 Online Training
The questions for CAS-003 were last updated at Dec 19,2025.
- Exam Code: CAS-003
- Exam Name: CompTIA Advanced Security Practitioner (CASP)
- Certification Provider: CompTIA
- Latest update: Dec 19,2025
After investigating virus outbreaks that have cost the company $1000 per incident, the company’s Chief Information Security Officer (CISO) has been researching new antivirus software solutions to use and be fully supported for the next two years.
The CISO has narrowed down the potential solutions to four candidates that meet all the company’s performance and capability requirements:
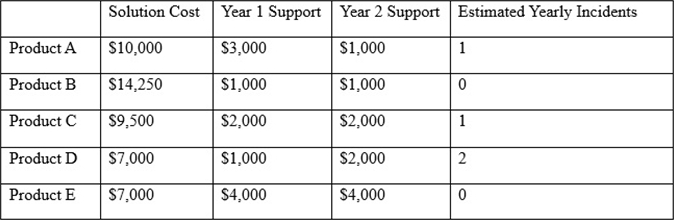
Using the table above, which of the following would be the BEST business-driven choice among five possible solutions?
- A . Product A
- B . Product B
- C . Product C
- D . Product D
- E . Product E
A security engineer is attempting to increase the randomness of numbers used in key generation in a system. The goal of the effort is to strengthen the keys against predictive analysis attacks.
Which of the following is the BEST solution?
- A . Use an entropy-as-a-service vendor to leverage larger entropy pools.
- B . Loop multiple pseudo-random number generators in a series to produce larger numbers.
- C . Increase key length by two orders of magnitude to detect brute forcing.
- D . Shift key generation algorithms to ECC algorithms.
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant.
The gap analysis reviewed all procedural and technical controls and found the following:
✑ High-impact controls implemented: 6 out of 10
✑ Medium-impact controls implemented: 409 out of 472
✑ Low-impact controls implemented: 97 out of 1000
The report includes a cost-benefit analysis for each control gap.
The analysis yielded the following information:
✑ Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000
✑ Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of the medium-impact controls will take two years to fully implement .
Which of the following conclusions could the CISO draw from the analysis?
- A . Too much emphasis has been placed on eliminating low-risk vulnerabilities in the past
- B . The enterprise security team has focused exclusively on mitigating high-level risks
- C . Because of the significant ALE for each high-risk vulnerability, efforts should be focused on those controls
- D . The cybersecurity team has balanced residual risk for both high and medium controls
A security architect is designing a system to satisfy user demand for reduced transaction time, increased security and message integrity, and improved cryptographic security. The resultant system will be used in an environment with a broad user base where many asynchronous transactions occur every minute and must be publicly verifiable.
Which of the following solutions BEST meets all of the architect’s objectives?
- A . An internal key infrastructure that allows users to digitally sign transaction logs
- B . An agreement with an entropy-as-a-service provider to increase the amount of randomness in generated keys.
- C . A publicly verified hashing algorithm that allows revalidation of message integrity at a future date.
- D . An open distributed transaction ledger that requires proof of work to append entries.
A security architect is designing a system to satisfy user demand for reduced transaction time, increased security and message integrity, and improved cryptographic security. The resultant system will be used in an environment with a broad user base where many asynchronous transactions occur every minute and must be publicly verifiable.
Which of the following solutions BEST meets all of the architect’s objectives?
- A . An internal key infrastructure that allows users to digitally sign transaction logs
- B . An agreement with an entropy-as-a-service provider to increase the amount of randomness in generated keys.
- C . A publicly verified hashing algorithm that allows revalidation of message integrity at a future date.
- D . An open distributed transaction ledger that requires proof of work to append entries.
A security architect is designing a system to satisfy user demand for reduced transaction time, increased security and message integrity, and improved cryptographic security. The resultant system will be used in an environment with a broad user base where many asynchronous transactions occur every minute and must be publicly verifiable.
Which of the following solutions BEST meets all of the architect’s objectives?
- A . An internal key infrastructure that allows users to digitally sign transaction logs
- B . An agreement with an entropy-as-a-service provider to increase the amount of randomness in generated keys.
- C . A publicly verified hashing algorithm that allows revalidation of message integrity at a future date.
- D . An open distributed transaction ledger that requires proof of work to append entries.
The data will be hosted and managed outside of the company’s geographical location
The number of users accessing the system will be small, and no sensitive data will be hosted in the solution.
As the security consultant on the project, which of the following should the project’s security consultant recommend as the NEXT step?
- A . Develop a security exemption, as it does not meet the security policies
- B . Mitigate the risk by asking the vendor to accept the in-country privacy principles
- C . Require the solution owner to accept the identified risks and consequences
- D . Review the entire procurement process to determine the lessons learned
A security assessor is working with an organization to review the policies and procedures associated with managing the organization’s virtual infrastructure. During a review of the virtual environment, the assessor determines the organization is using servers to provide more than one primary function, which violates a regulatory requirement. The assessor reviews hardening guides and determines policy allows for this configuration.
It would be MOST appropriate for the assessor to advise the organization to:
- A . segment dual-purpose systems on a hardened network segment with no external access
- B . assess the risks associated with accepting non-compliance with regulatory requirements
- C . update system implementation procedures to comply with regulations
- D . review regulatory requirements and implement new policies on any newly provisioned servers
To prepare for an upcoming audit, the Chief Information Security Officer (CISO) asks for all 1200 vulnerabilities on production servers to be remediated. The security engineer must determine which vulnerabilities represent real threats that can be exploited so resources can be prioritized to migrate the most dangerous risks. The CISO wants the security engineer to act in the same manner as would an external threat, while using vulnerability scan results to prioritize any actions.
Which of the following approaches is described?
- A . Blue team
- B . Red team
- C . Black box
- D . White team
A security administrator is troubleshooting RADIUS authentication issues from a newly implemented controller-based wireless deployment.
The RADIUS server contains the following information in its logs:
![]()
Based on this information, the administrator reconfigures the RADIUS server, which results in the following log data:
![]()
To correct this error message, the administrator makes an additional change to the RADIUS server .
Which of the following did the administrator reconfigure on the RADIUS server? (Select TWO)
- A . Added the controller address as an authorized client
- B . Registered the RADIUS server to the wireless controller
- C . Corrected a mismatched shared secret
- D . Renewed the expired client certificate
- E . Reassigned the RADIUS policy to the controller
- F . Modified the client authentication method
Latest CAS-003 Dumps Valid Version with 509 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


ddd
nnn