CompTIA CAS-003 CompTIA Advanced Security Practitioner (CASP) Online Training
CompTIA CAS-003 Online Training
The questions for CAS-003 were last updated at Dec 19,2025.
- Exam Code: CAS-003
- Exam Name: CompTIA Advanced Security Practitioner (CASP)
- Certification Provider: CompTIA
- Latest update: Dec 19,2025
Access to the corporate applications
Which of the following solution components should be deployed to BEST meet the requirements? (Select three.)
- A . IPSec VPN
- B . HIDS
- C . Wireless controller
- D . Rights management
- E . SSL VPN
- F . NAC
- G . WAF
- H . Load balancer
The marketing department has developed a new marketing campaign involving significant social media outreach. The campaign includes allowing employees and customers to submit blog posts and pictures of their day-to-day experiences at the company. The information security manager has been asked to provide an informative letter to all participants regarding the security risks and how to avoid privacy and operational security issues .
Which of the following is the MOST important information to reference in the letter?
- A . After-action reports from prior incidents.
- B . Social engineering techniques
- C . Company policies and employee NDAs
- D . Data classification processes
A security analyst who is concerned about sensitive data exfiltration reviews the following:

Which of the following tools would allow the analyst to confirm if data exfiltration is occuring?
- A . Port scanner
- B . SCAP tool
- C . File integrity monitor
- D . Protocol analyzer
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor’s cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications .
Which of the following does the organization plan to leverage?
- A . SaaS
- B . PaaS
- C . IaaS
- D . Hybrid cloud
- E . Network virtualization
A security analyst is troubleshooting a scenario in which an operator should only be allowed to reboot remote hosts but not perform other activities.
The analyst inspects the following portions of different configuration files:
Configuration file 1:
Operator ALL=/sbin/reboot
Configuration file 2:
Command=”/sbin/shutdown now”, no-x11-forwarding, no-pty, ssh-dss
Configuration file 3:
Operator:x:1000:1000::/home/operator:/bin/bash
Which of the following explains why an intended operator cannot perform the intended action?
- A . The sudoers file is locked down to an incorrect command
- B . SSH command shell restrictions are misconfigured
- C . The passwd file is misconfigured
- D . The SSH command is not allowing a pty session
Following a security assessment, the Chief Information Security Officer (CISO) is reviewing the results of the assessment and evaluating potential risk treatment strategies. As part of the CISO’s evaluation, a judgment of potential impact based on the identified risk is performed. To prioritize response actions, the CISO uses past experience to take into account the exposure factor as well as the external accessibility of the weakness identified.
Which of the following is the CISO performing?
- A . Documentation of lessons learned
- B . Quantitative risk assessment
- C . Qualitative assessment of risk
- D . Business impact scoring
- E . Threat modeling
Security policies that are in place at an organization prohibit USB drives from being utilized across the entire enterprise, with adequate technical controls in place to block them. As a way to still be able to work from various locations on different computing resources, several sales staff members have signed up for a web-based storage solution without the consent of the IT department. However, the operations department is required to use the same service to transmit certain business partner documents.
Which of the following would BEST allow the IT department to monitor and control this behavior?
- A . Enabling AAA
- B . Deploying a CASB
- C . Configuring an NGFW
- D . Installing a WAF
- E . Utilizing a vTPM
As part of the development process for a new system, the organization plans to perform requirements analysis and risk assessment. The new system will replace a legacy system, which the organization has used to perform data analytics .
Which of the following is MOST likely to be part of the activities conducted by management during this phase of the project?
- A . Static code analysis and peer review of all application code
- B . Validation of expectations relating to system performance and security
- C . Load testing the system to ensure response times is acceptable to stakeholders
- D . Design reviews and user acceptance testing to ensure the system has been deployed properly
- E . Regression testing to evaluate interoperability with the legacy system during the deployment
Management is reviewing the results of a recent risk assessment of the organization’s policies and procedures. During the risk assessment it is determined that procedures associated with background checks have not been effectively implemented. In response to this risk, the organization elects to revise policies and procedures related to background checks and use a third-party to perform background checks on all new employees.
Which of the following risk management strategies has the organization employed?
- A . Transfer
- B . Mitigate
- C . Accept
- D . Avoid
- E . Reject
Latest CAS-003 Dumps Valid Version with 509 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

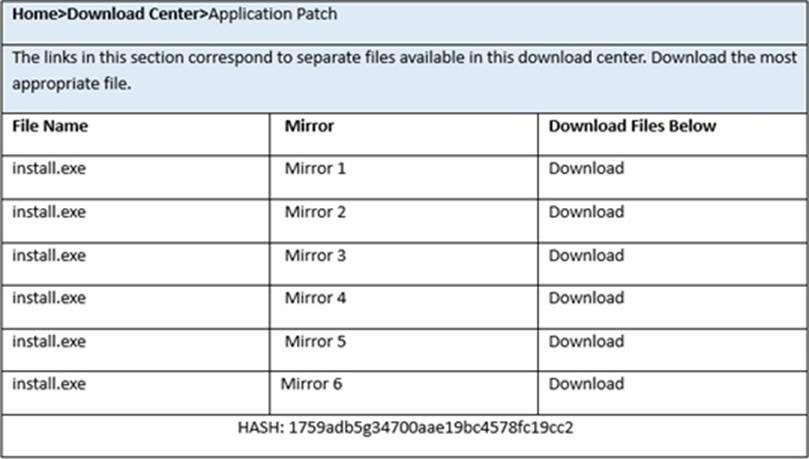
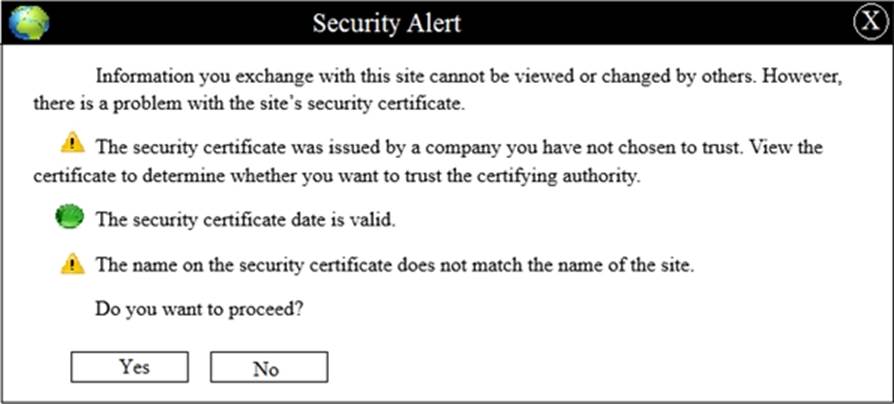
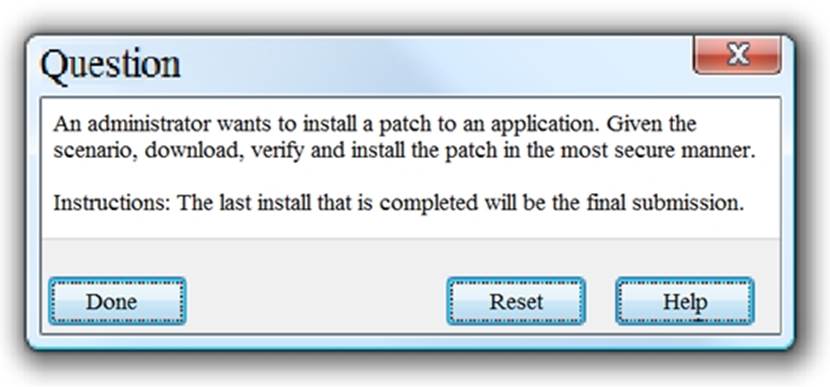

ddd
nnn