Cisco 400-251 CCIE Security Written Exam (v5.0) Online Training
Cisco 400-251 Online Training
The questions for 400-251 were last updated at Dec 19,2025.
- Exam Code: 400-251
- Exam Name: CCIE Security Written Exam (v5.0)
- Certification Provider: Cisco
- Latest update: Dec 19,2025
A device on your internal network is hard-coded with two DNS server on the Internet (1.1.1.53, 2.2.2.53).
However, you want to send all requests to your OpenDNS server (208.67.222.222).
Which set of commands do you run on the ASA to achieve this goal?
- A . Static (inside, outside) source any 1.1.1.53destination 208.61 222.222 eq domain
Static (inside, outside) source any 2.2.2.53 destination 208.67.222.222 eq domain - B . Static (inside, outside) source any 208.67.222.222 destination 1.1.1.53 eq domain
Static (inside, outside) source any 208.67.222.222 destination 2.2.2.53 eq domain - C . Static (inside, outside) source any destination 208.67.222.222 eq domain
- D . Static (outside, inside) source any 208.67.222 222 destination 1.1.1.56 eq domain
Static (outside, inside) source any 208.67.222.222 destination 2.2.2.53 eq domain - E . Net (inside, outside) source any 1. 1.1.53 destination 208.67.222 222 eq domain
Nat (inside, outside) source any 2.2.2.53 destination 208.67.222 222 eq domain - F . Object network OpenDNS
Host 208.67.222.222
!
Object network Rogue1-DNS
Host 1.1.1.53
Object network Rogue2-DNS
Host 2.2.2.53
!
Object-group network Rogue-DNS
Network-object object Rogue1-DNS
Network-object object Rogue2-DNS
!
object service udp-DNS
Service udp destination eq domain
!
object service tcp-DNS
Service tcp destination eq domain
!
nat(inside, outside) source static any interface destination static Rogue-DNS OpenDNS service udp-DNS udp-DNS
nat(inside, outside) source static any interface destination static Rogue-DNS OpenDNS service tcp-DNS tcp-DNS - G . nat (inside, outside) source static any interface destination static Rogue-DNS OpenDNS service udp-DNS udp-DNs
nat (inside, outside) source static any interface destination static Rogue-DNS OpenDNS service udp-DNS udp-DNS - H . object network OpenDNS
host 1.1.1.53
object network Rogue1-DNS
host 2.2.2.53
!
Object-group network rogue1-DNS
Network-object object Rogue1-DNS
Network-object object Rogue2-DNS
!
Object service udp-DNS
Service udp destination eq domain
!
Object service tcp-DNS
Service tcp destination eq domain
!
Nat (inside, outside) source static any interface destination static OpenDNS Rogue-DNS service udp-DNS udp-DNS
Nat (inside, outside) source static any interface destination static OpenDNS Rogue-DNS service tcp-DNS tcp-DNS
What are the advantages of using LDAP over AD is true?
- A . LDAP allows for granular policy control, whereas Ad does not
- B . LDAP provides for faster authentication
- C . LDAP can be configured to use primary and secondary server, whereas AD cannot
- D . LDAP does not require ISE to join the ad domain
- E . The closest LDAP servers are used for Authentication
In a large organization, with thousands of employees scattered across the globe, it is difficult to provision and onboard new employee devices with the correct profiles and certificates.
With ISE, it is possible to do client provided which four conditions are met. (Choose four)
- A . Endpoint operating System should be supported
- B . Client provisioning is enabled on ISE
- C . The px Grid controller should be enabled on ISE
- D . Device MAC Addresses are added to the End point Identity Group
- E . Profiling is enabled on ISE
- F . SCEP Proxy enabled on ISE
- G . Microsoft windows Server is configured with certificate services
- H . ISE should be configured as SXP listener to push SGT-To-IP map ping to network access devices
- I . Network access devices and ISE should have the PAC provisioning for CTS environment authentication
There is no ICMP connectivity from VPN_PC to Server 1 and Server 2.
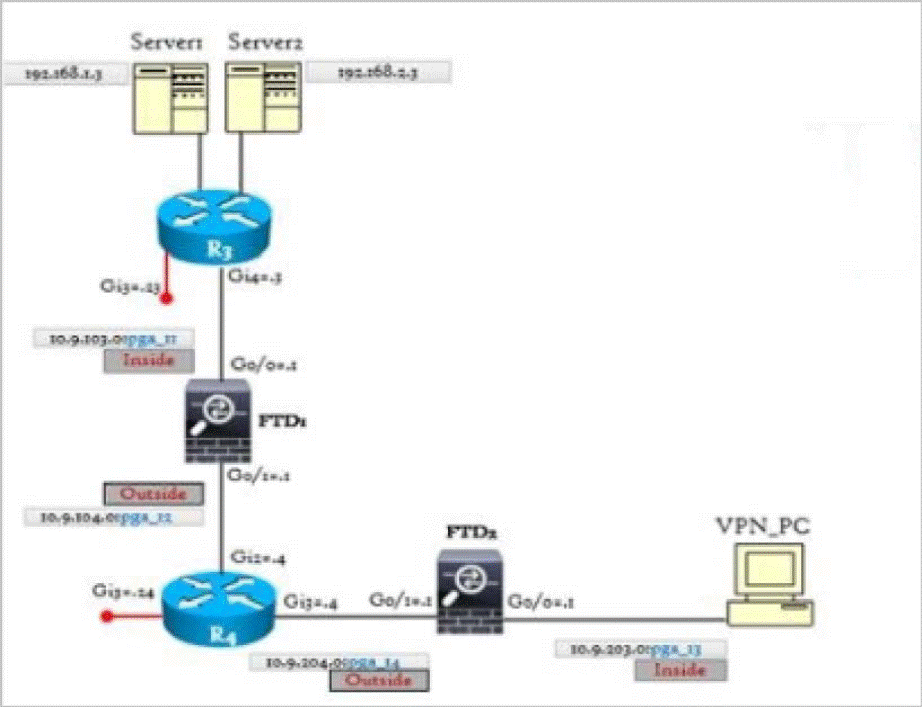
There is no ICMP connectivity from VPN_PC to Server 1 and Server 2.
What could be the possible cause?
- A . The action is incorrect in the access rule
- B . The destination port configuration missing in the access rule
- C . The server network has incorrect mask in the access rule
- D . The VLAN tags configuration missing in the access rule
E. The source network is incorrect in the access rule - E . The zone configuration missing in the access rule
- F . The network address of the servers is configured incorrectly in the access rule
In an effort to secure your enterprise campus network, any endpoint that connects to the network must authenticate before being granted access. For all corporate-owned endpoints, such as laptops, mobile phones and tables, you would like to enable 802. 1x and once authenticated allow full access to the network. For all employee owned personal devices, you would like to use web authentication, and only allow limited access to the network.
Which two authentication methods can ensure that an employee on a personal device cant use his or her Active Directory credentials to log on to the network by simply reconfiguring their supplicant to use 802.1x and getting unfettered access? (Choose two)
- A . Use PEAP-EAP-MSCHAPV2
- B . Use EAP-FAST
- C . Use EAP-TLS or EAP-TTLS
- D . Use EAP-MSCHAPv2
- E . Use PAP-CHAP-MSCHAP
Which statement about SSL policy implementation in a cisco Firepower system is true?
- A . Access control policy is optional for the SSL policy implementation
- B . If Firepower system cannot decrypt the traffic, it allows the connection
- C . Intrusion policy is mandatory to configure the SSL inspection
- D . Access control policy is responsible to handle all the encrypted traffic if SSL policy is tried to it
- E . Access control policy is invoked first before the SSL policy tied to it
- F . If SSL policy is not supported by the system then access control policy handles all the encrypted traffic
A university has hired you as a consultant to advise them on the best method to prevent DHCP starvation attacks in the campus. They have already implemented DH CP snooping and port security to control the situation but those do not fully contain the issue.
Which two actions do you suggest to fix this issue? (Choose two.)
- A . Use the ip dhcp snooping limit rate command on Trusted and Untrusted interfaces and set the rate to suitable values that are relevant to each interface respectively.
- B . Use the ip dhcp snooping verify mac-address command to ensure that the source MAC address in the DHCP request matches the client hardware address (CHADDR) sent to the DHCP server.
- C . Use the ip dhcp snooping verify mac-address command to ensure that the source MAC address in the DHCP request matches the client identifier (CLID) field sent to the DHCP server.
- D . Use the ip dhcp snooping limit rate command only to ensure that the source MAC address in the DHCP request matches the client identifier (CLID)field sent to the DHCP server.
- E . Use the ip dhcp snooping limit rate command on trusted and untrusted interfaces set to the rate same value
- F . Use the ip dhcp snooping limit rate command only on Untrusted interfaces and set the rate to suitable values that are relevant to the interface
Which statement about Sender Base reputation scoring on an ESA device is true?
- A . Application traffic from known bad sites can be throttled or blocked
- B . By default, all messages with a score below zero are dropped or throttled
- C . Mail with scores in the medium range can be automatically routed for antimalware scanning
- D . You can configure a custom score threshold for whitelisting messages
- E . A high score indicates that a message is very likely to be spam
- F . Sender reputation scores can be assigned to domains, IP addresses, and MAC addresses
Refer to the exhibit.
Router(contig)# cts sxp reconciliation period 180
Which two statements about a device with this configuration are true? (Choose two
- A . When a peer re-establishes a previous connection to the device. CTS retains all existing SGT mapping entries for 3 minutes
- B . If a peer reconnects to the device within 120 seconds of terminating a CTS-SXP connection, the reconciliation timer starts
- C . If a peer re-establishes a connection to the device before the hold-down tier expires, the device retains the SGT mapping entries it learned during the previous connection for an additional 3 minutes
- D . It sets the internal hold-down timer of the device to 3 minutes
- E . When a peer establishes a new connection to the device, CTS retains all existing SGT mapping entries for 3 minutes
- F . If a peer reconnects to the device within 180 seconds of terminating a CTs-SXP connection, the reconciliation timer starts
Which statement about stealth scan is true?
- A . It evades network auditing tools
- B . It relies on ICMP "port unreachable" message to determine if the port is open
- C . It is used to find the ports that already have an existing vulnerability to exploit
- D . It checks the firewall deployment in the path
- E . It never opens a full TCP connection
- F . It is a directed scan to a known TCP/UDP port
Latest 400-251 Dumps Valid Version with 124 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

