Cisco 400-007 Cisco Certified Design Expert Online Training
Cisco 400-007 Online Training
The questions for 400-007 were last updated at Dec 07,2025.
- Exam Code: 400-007
- Exam Name: Cisco Certified Design Expert
- Certification Provider: Cisco
- Latest update: Dec 07,2025
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two)
- A . Serialization delays are invariable because they depend only on the line rate of the interface
- B . Serialization delays are variable because they depend on the line rate of the interface and on the type of the packet being serialized.
- C . Serialization delay is the time required to transmit the packet on the physical media.
- D . Serialization delays are variable because they depend only on the size of the packet being serialized
- E . Serialization delay depends not only on the line rate of the interface but also on the size of the packet
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact.
Which implementation plan can be used to accommodate this during the migration phase?
- A . Deploy controllers, deploy SD-WAN edge routers. In the data center, and migrate branch sites.
- B . Migrate data center WAN routers, migrate branch sites, and deploy SD-WAN edge routers.
- C . Migrate branch sites, migrate data center WAN routers, and deploy controllers.
- D . Deploy SD-WAN edge routers in the data center, deploy controllers, and migrate branch sites
Refer to the exhibit.
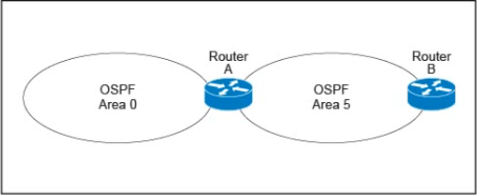
A customer runs OSPF with Area 5 between its aggregation router and an internal router When a network change occurs in the backbone. Area 5 starts having connectivity issues due to the SPF algorithm recalculating an abnormal number of times in Area 5 You are tasked to redesign this network to increase resiliency on the customer network with the caveat that Router B does not support the stub area.
How can you accomplish this task*?
- A . Increase the bandwidth on the connection between Router A and Router B
- B . Implement LSA filtering on the AB, allowing summary routes and preventing more specific routes into Area 5
- C . Create a virtual link to Area 0 from Router B to the ABR
- D . Turn on LSA throttling on all devices in Area 5
- E . Set Area 5 to stubby at the ABR anyway
You are designing a large-scale DMVPN network with more than 500 spokes using EIGRP as the IGP protocol.
Which design option eliminates potential tunnel down events on the spoke routers due to the holding time expiration?
- A . Increase the hold queue on the physical interface of the hub router.
- B . Increase the hold queue on the tunnel interface of the spoke routers
- C . Increase the hold queue on the tunnel interface of the hub router
- D . Apply QoS for pak_priority class
- E . Increase the hold queue on the physical interface of the spoke routers.
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches.
Which use case is suitable for using IPFIX probes?
- A . performance monitoring
- B . security
- C . observation of critical links
- D . capacity planning
Which design principal improves network resiliency?
- A . Added load-balancing
- B . Added redundancy
- C . Added confidentiality
- D . Added reliability
Company XYZ is designing the network for IPv6 security and they have these design requirements:
✑ A switch or router must deny access to traffic from sources with addresses that are correct, but are topologically incorrect
✑ Devices must block Neighbor Discovery Protocol resolution for destination addresses that are not found in the binding table.
Which two IPv4 security features are recommended for this company?
- A . IPv6 DHCP Guard
- B . IPv6 Source Guard
- C . IPv6 Destination Guard
- D . IPv6 Prefix Guard
- E . IPv6 RA Guard
Company XYZ has 30 sites using MPLS L3 VPN and the company is now concerned about data integrity.
The company wants to redesign the security aspect of their network based on these requirements:
• Securely transfer the corporate data over the private WAN
• Use a centralized configuration model.
• Minimize overhead on the tunneled traffic.
Which technology can be used in the new design to meet the company’s requirements?
- A . S-VTI
- B . DMVPN
- C . MGRE
- D . GET VPN
Router R1 is a BGP speaker with one peering neighbor over link "A". When the R1 link/interface "A" fails, routing announcements are terminated, which results in the tearing down of the state for all BGP routes at each end of the link.
What is this a good example of?
- A . fault isolation
- B . resiliency
- C . redundancy
- D . fate sharing
When an SDN-based model is used to transmit multimedia traffic, which aspect should an architect consider while designing the network?
- A . QoE estimation
- B . security
- C . traffic patterns
- D . flow forwarding
Latest 400-007 Dumps Valid Version with 141 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

