Cisco 350-901 Developing Applications using Cisco Core Platforms and APIs v1.0 Online Training
Cisco 350-901 Online Training
The questions for 350-901 were last updated at Sep 15,2025.
- Exam Code: 350-901
- Exam Name: Developing Applications using Cisco Core Platforms and APIs v1.0
- Certification Provider: Cisco
- Latest update: Sep 15,2025
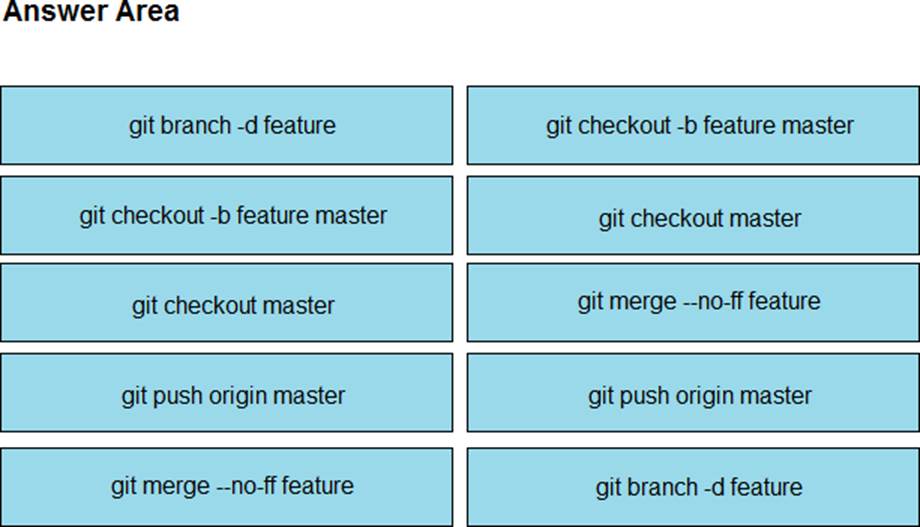
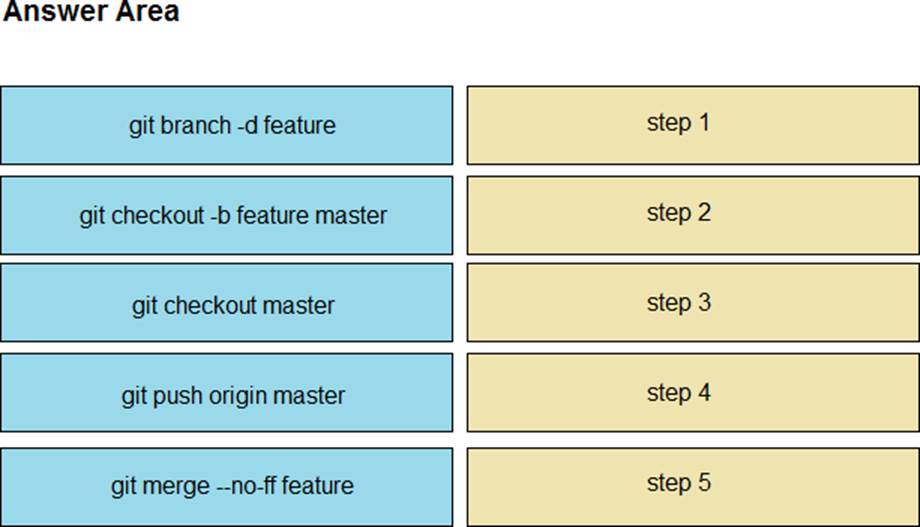
DRAG DROP
Drag and drop the git commands from the left into the correct order on the right to create a feature branch from the master and then incorporate that feature branch into the master.
Which tool is used to deploy an IOx application to a group of lOx devices at one time?
- A . ioxclient
- B . lOx local manager
- C . Fog Network Director
- D . Kubernetes
Refer to the exhibit.
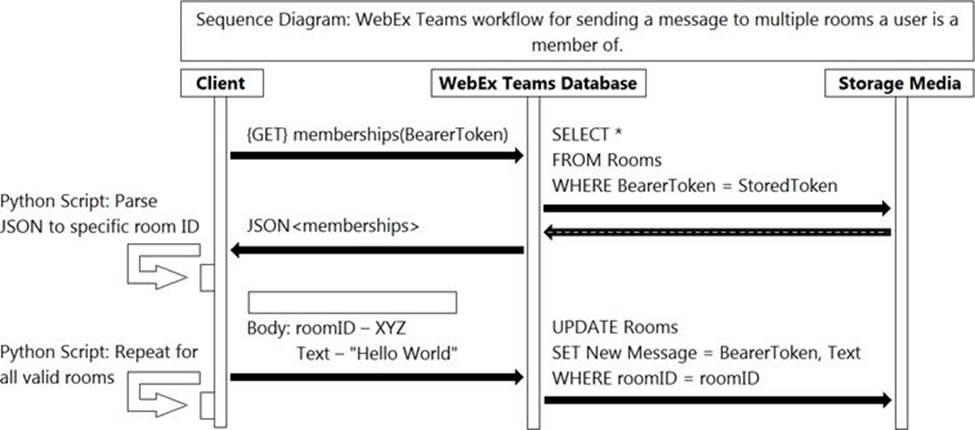
Which action will complete the workflow that represents how an API call sends multiple messages?
- A . {PUT} messages(roomID)
- B . {PUT} messages(BearerToken)
- C . {POST} messages(roomID)
- D . {POST} messages(BearerToken)
Refer to the exhibit.
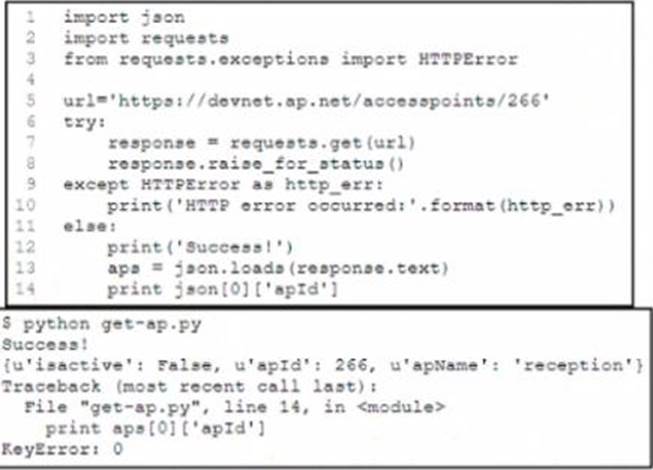
A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points. The developer is retrieving an access point ID by using a REST API. The output indicates that there was a KeyError when parsing the JSON response.
What returns the expected output of 266 at line 14?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option
- B . Option
- C . Option
- D . Option
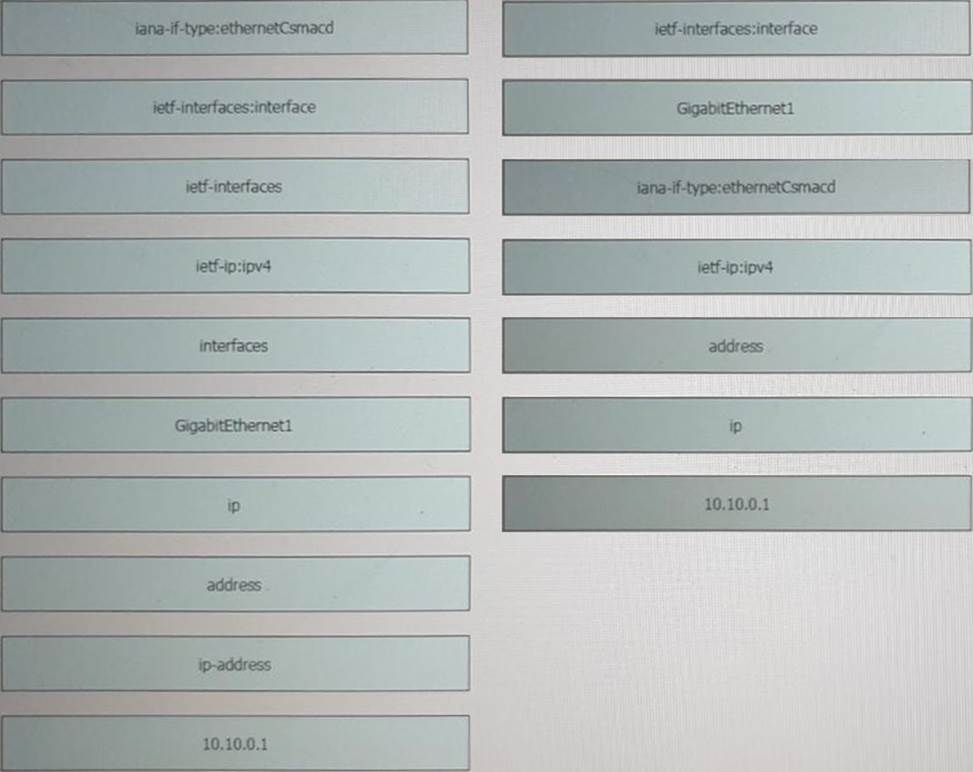
DRAG DROP
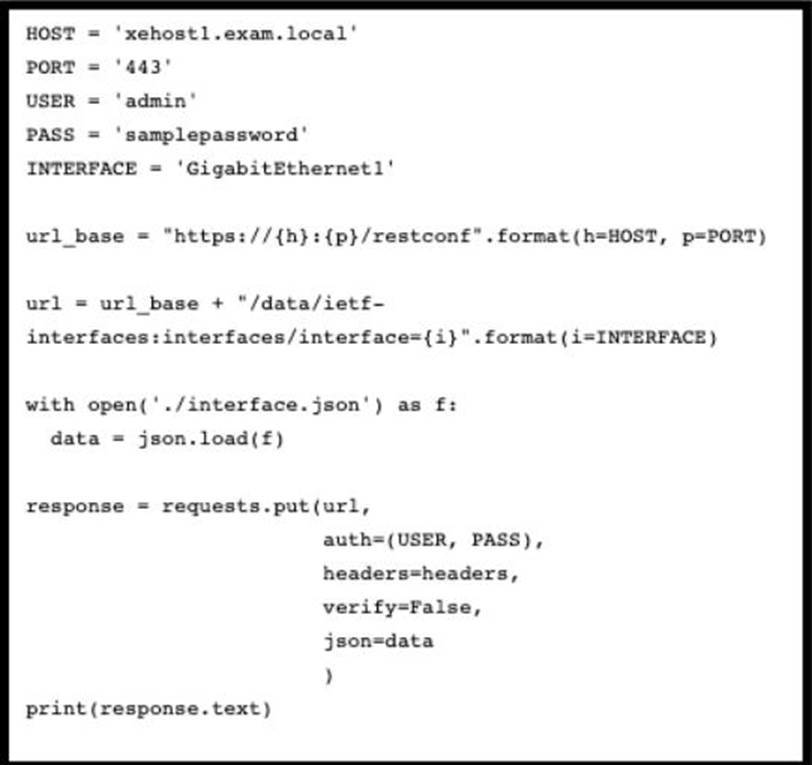
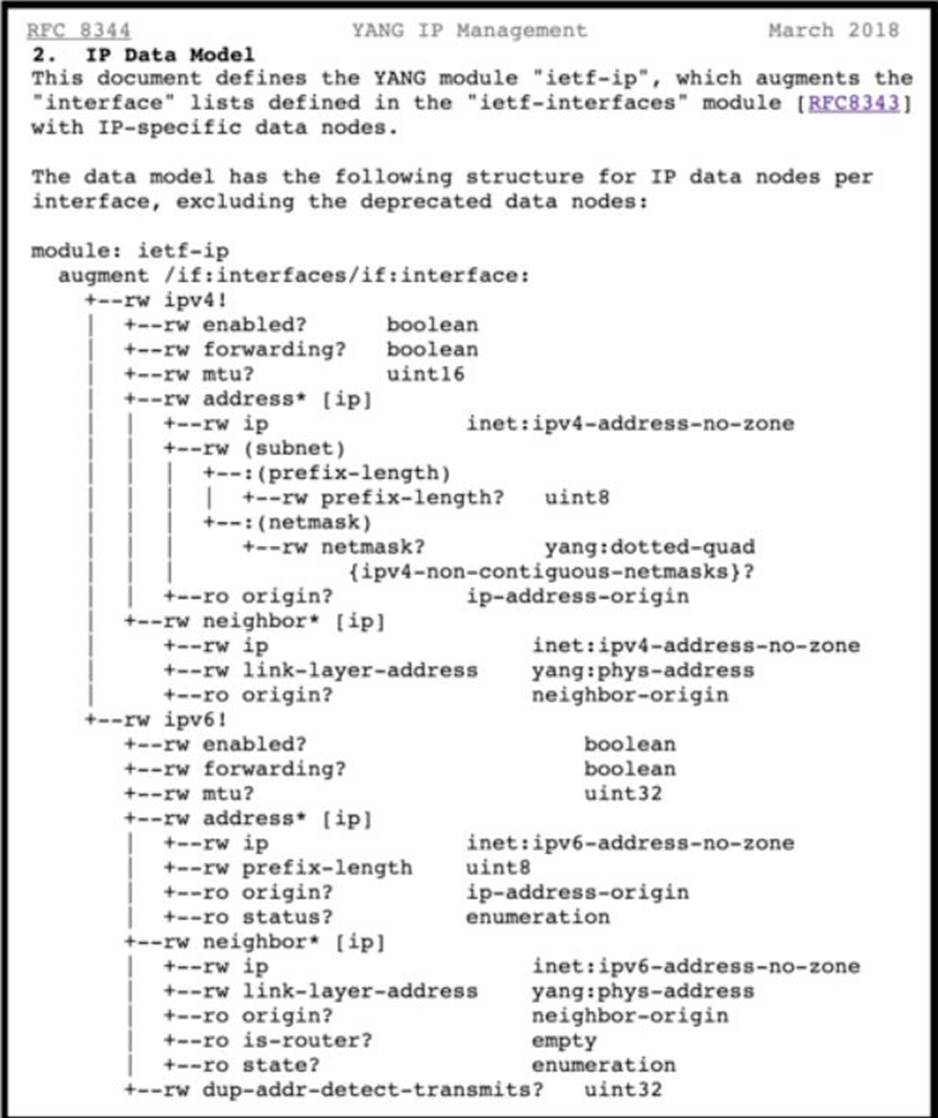
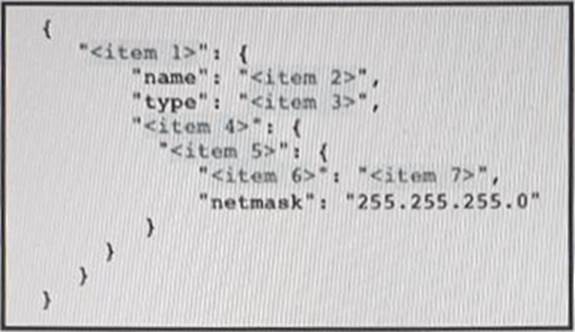
Refer to the exhibit above and click on the resource tabs in the top left corner to view an IETF TANG MODEL and a Python file that changes the configuration via RESTCONF.
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the JSON file that changes configuration of interface GigabitEthernet1 to have an IPv4 configuration of 10.10.0.1/24. Not all options are used.
Which two principles are included in the codebase tenet of the 12-factor app methodology? (Choose two.)
- A . An application is always tracked in a version control system.
- B . There are multiple codebases per application.
- C . The codebase is the same across all deploys.
- D . There can be a many-to-one correlation between codebase and application.
- E . It is only possible to have one application deployment per codebase.
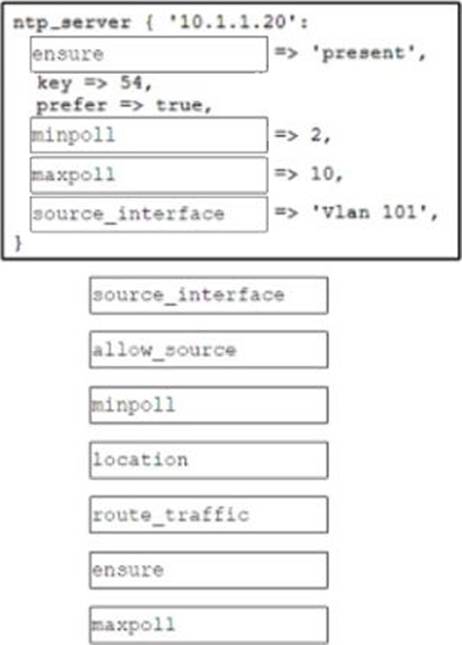
DRAG DROP
Drag and drop the code from the bottom onto the box where the code is missing to create a Puppet manifest that implements an NTP configuration when applied to a device in the master inventory. Not all options are used.

Which two encryption principles should be applied to secure APIs? (Choose two.)
- A . Use temporary files as part of the encryption and decryption process
- B . Transmit authorization information by using digitally signed payloads
- C . Use encrypted connections to protect data n transit
- D . Reuse source code that contain existing UUIDs
- E . Embed keys in code to simplify the decryption process
Refer to the exhibit, The command docker build -tag=friendlyhello . is run to build a docker image from the given Dockerfile, requirements,txt, and app.py, Then the command docker run -p 4000:80 friendlyhello is executed to run the application.
Which URL is entered in the web browser to see the content served by the application?
- A . http://localhost:4000
- B . http ://localhost:80
- C . http ://127.0.0.1:80
- D . http:///4000:80
Refer to the exhibit.
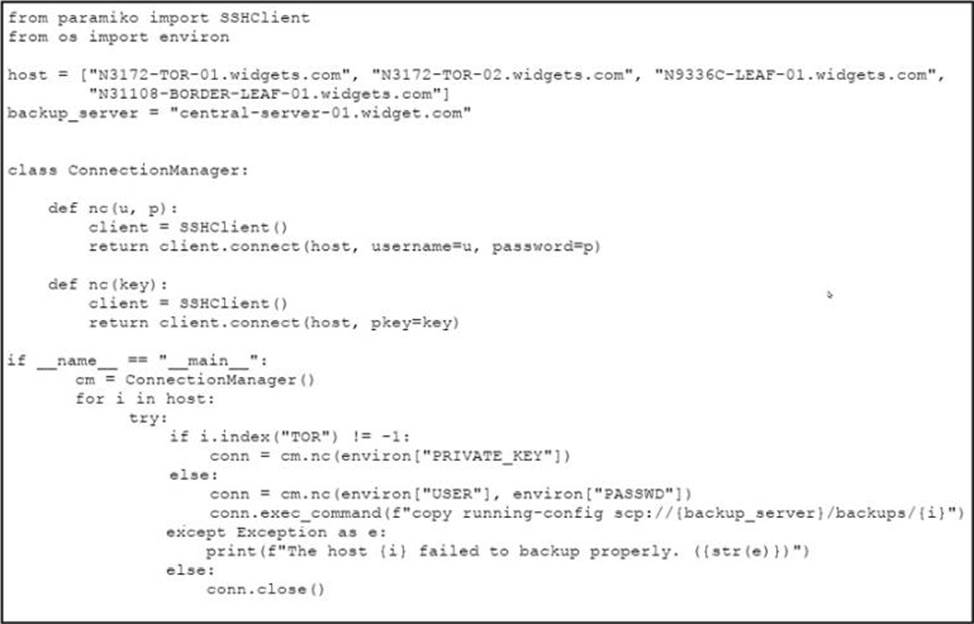
A developer must review an intern’s code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server.
When considering maintainability, which two changes must be made to the code? (Choose two.)
- A . Rename the class to "ArchiveManager".
- B . The code is incorrect because the class does not have an__init__() method.
- C . The command sent to the network device is incorrect.
- D . Refactor the code placing the "for" loop steps inside a single nc method.
- E . The intern must use IP addresses because DNS is unreliable.
Latest 350-901 Dumps Valid Version with 169 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund