Cisco 350-501 Implementing and Operating Cisco Service Provider Network Core Technologies Online Training
Cisco 350-501 Online Training
The questions for 350-501 were last updated at Jan 29,2026.
- Exam Code: 350-501
- Exam Name: Implementing and Operating Cisco Service Provider Network Core Technologies
- Certification Provider: Cisco
- Latest update: Jan 29,2026
Refer to the exhibit:
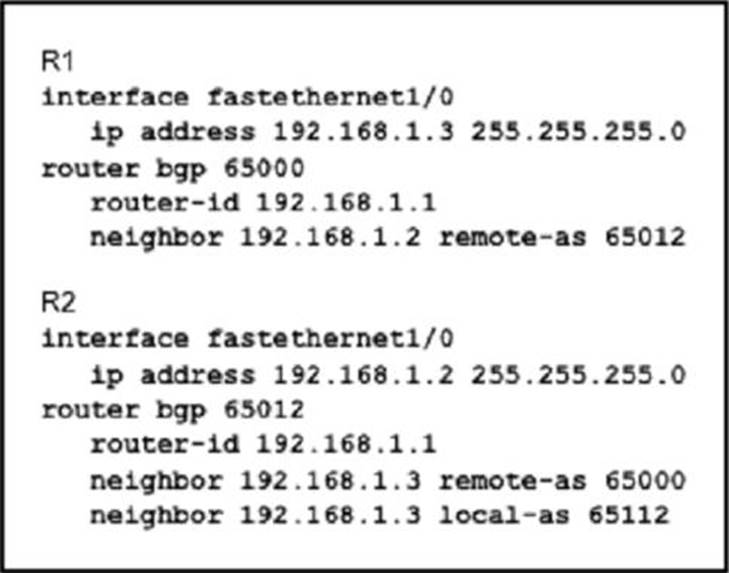
Assume all other configurations are correct and the network is otherwise operating normally.
Which conclusion can you draw about the neighbor relationship between routers R1 and R2?
- A . The neighbor relationship will be up only if the two devices have activated the correct neighbor relationships under the IPv4 address family
- B . The neighbor relationship is down because R1 believes R2 is in AS 65012.
- C . The neighbor relationship is up
- D . The neighbor relationship is down because the loco I-as value for R2 is missing in the R1 neighbor statement
Which statement about the Cisco MPLS TE forwarding adjacency feature is true?
- A . It enables the headend and tailend routers to establish a bidirectional tunnel
- B . It enables the tailend router to advertise routes to the headend router over the tunnel
- C . It enables the MPLS core to use EIGRP as the routing protocol
- D . It enables the Cisco MPLS TE tunnel to be advertised into the running IGP.
Refer to the exhibit:
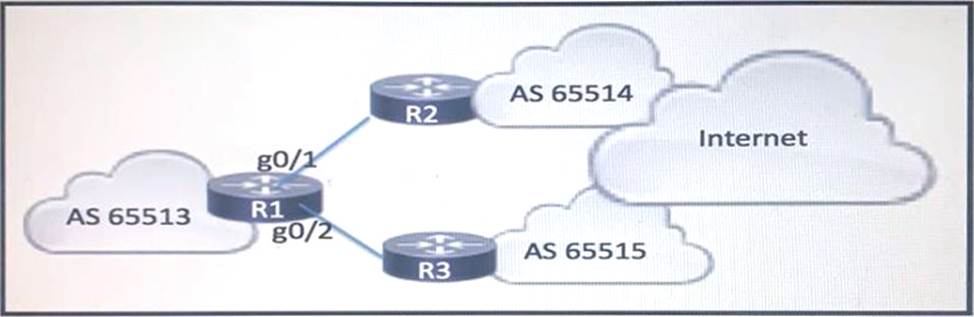
R1 is connected to two service providers and is under a DDoS attack.
Which statement about this design is true if uRPF in strict mode is configured on both interfaces?
- A . R1 accepts source addresses on interface gigabitethernet0/1 that are private addresses
- B . R1 permits asymmetric routing as long as the AS-RATH attribute entry matches the connected AS
- C . R1 drops destination addresses that are routed to a null interface on the router
- D . R1 drops all traffic that ingresses either interface that has a FIB entry that exits a different interface
A router is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization to a neighbor to establish an LDP session? (Choose three)
- A . Reconnect Timeout field
- B . Learn from Neighbor (N) flag, set to 1
- C . Graceful restart capability in OPEN message
- D . Recovery Time field
- E . Learn from Network (L.) flage, set to 1
- F . Type-9 LSA
Refer to the exhibit:

Which information is provided for traceback analysis when this configuration is applied?
- A . BGP version
- B . packet size distribution
- C . source interface
- D . IP sub flow cache
Refer to the exhibit:

Which statement describes the effect of this configuration?
- A . It applies a service policy to all interfaces remarking HTTP traffic
- B . It creates an ACL named WEB that filters HTTP traffic.
- C . It matches HTTP traffic for use in a policy map
- D . It modifies the default policy map to allow all HTTP traffic through the router
Why do Cisco MPLS TE tunnels require a link-state routing protocol?
- A . Link-state routing protocols use SPF calculations that the tunnel endpoints leverage to implement the tunnel
- B . The link-state database provides a data repository from which the tunnel endpoints can dynamically select a source ID
- C . The tunnel endpoints can use the link-state database to evaluate the entire topology and determine the best path
- D . The link state database provides segmentation by area, which improves the path-selection process
Which additional feature does MPLS DiffServ tunneling support?
- A . matching EXP and DSCP values
- B . interaction between MPLS and IGP
- C . using GRE tunnels to hide markings
- D . PHB layer management
You are writing an RPL script to accept routes only from certain autonomous systems Consider this code.
![]()
If you apply this code to BGP filters, which effect does the code have on your router?
- A . denies routes from AS 7070
- B . allows routes from AS 7077
- C . denies routes from AS 7007
- D . allows routes from AS 770
Refer to the exhibit:
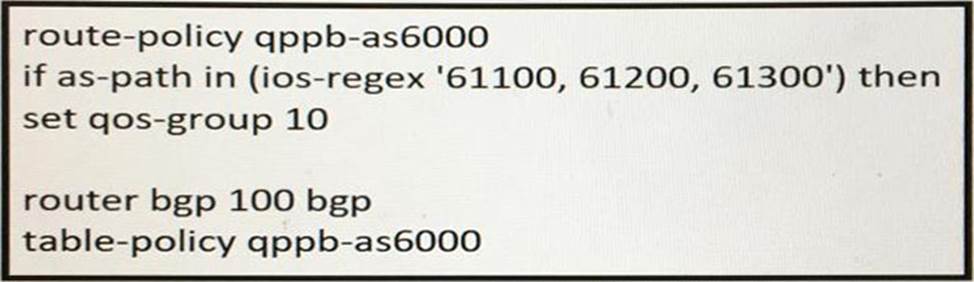
Which statement supports QPPB implementation?
- A . QoS policies are identified in the MPLS forwarding table
- B . QoS policies rely exclusively on BGP attributes to manipulate traffic
- C . QoS policies use BGP to gain full coverage on the network.
- D . QPPB policies affect only egress traffic
Latest 350-501 Dumps Valid Version with 248 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

