Cisco 350-501 Implementing and Operating Cisco Service Provider Network Core Technologies Online Training
Cisco 350-501 Online Training
The questions for 350-501 were last updated at Jan 29,2026.
- Exam Code: 350-501
- Exam Name: Implementing and Operating Cisco Service Provider Network Core Technologies
- Certification Provider: Cisco
- Latest update: Jan 29,2026
Which configuration modifies Local Packet Transport Services hardware policies?
A)

B)

C)

D)

- A . Option A
- B . Option B
- C . Option C
- D . Option D
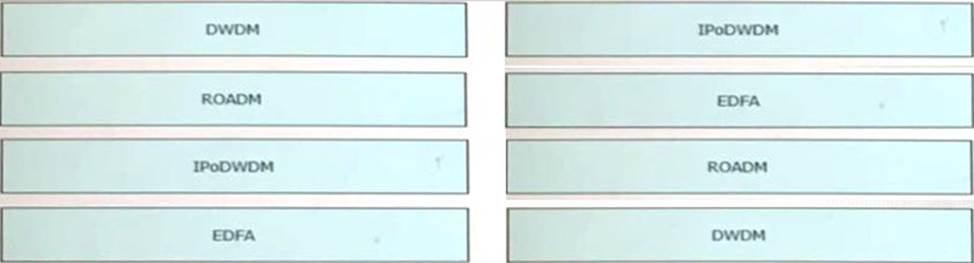
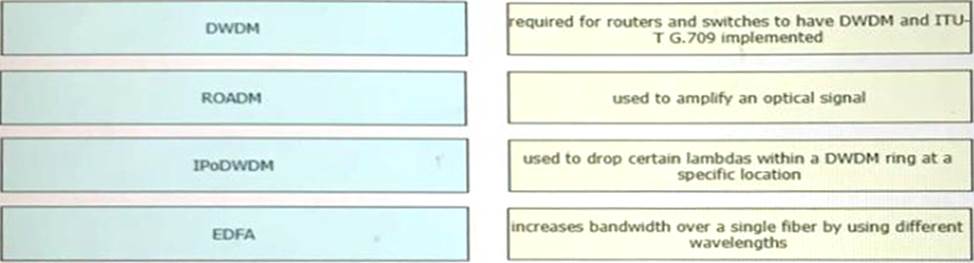
DRAG DROP
Drag and drop the technologies from the left onto the correct definitions on the right.
Which two IS-IS parameters must match before two Level 2 peers can form an adjacency? (Choose two)
- A . authentication settings
- B . area ID
- C . system ID
- D . MTU
- E . hello timer setting
Which three OSPF parameters must match before two devices can establish an OSPF adjacency? (Choose three.)
- A . IP address
- B . interface cost
- C . subnet mask
- D . process ID
- E . hello timer setting
- F . area number
Refer to the exhibit:
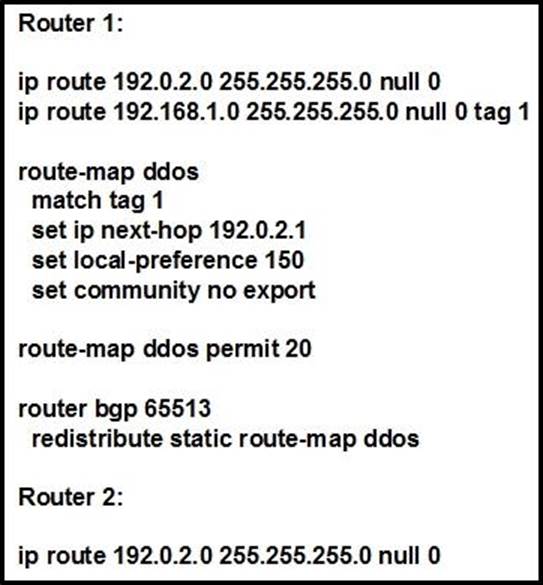
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
- A . Router 2 must configure a route to null 0 for network 192 168.1 0/24 for the RTBH implementation to be complete.
- B . Router 1 is the trigger router in a RTBH implementation.
- C . Router 1 must be configured with uRPF for the RTBH implementation to be effective.
- D . Router 2 is the router receiving the DDoS attack
Refer to the exhibits:
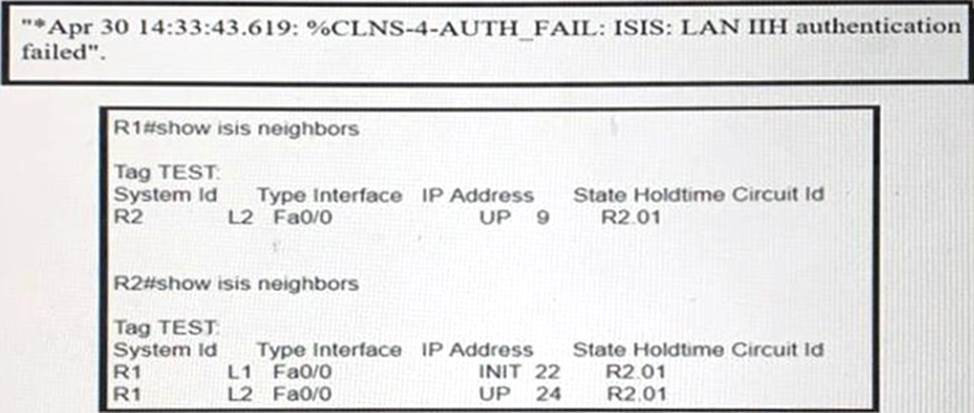
R1 and R2 are directly connected and IS-IS routing has been enabled between R1 and R2 R1 message periodically.
Based on this output, which statement is true?
- A . IS-IS neighbor authentication is failing for Level 2 first and then for Level 1 PDUs
- B . 1S-1S neighbor authentication is failing for Level 1 and Level 2 PDUs.
- C . IS-IS neighbor authentication is failing for Level 1 PDUs only
- D . IS-IS neighbor authentication is failing for Level 2 PDUs only.
Which BGP attribute is used first when determining the best path?
- A . origin
- B . AS path
- C . local preference
- D . weight
While implementing TTL security, you issue the PE (config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command.
After you issue this command, which BGP packets does the PE accept?
- A . from 2.2.2.2, with a TTL of 253 Of more
- B . from 2.2.2.2, with a TTL of less than 2
- C . to 2.2.2.2, with a TTL of less than 253
- D . to 2.2.2.2, with a TTL of 2 or more
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
- A . It is used to set up configuration to poll network data
- B . It is used to enable gRPC
- C . It is used to create a streaming subscription with a 60-second interval
- D . It is used to create a streaming subscription with a 600-second interval
What do Ansible and Salt Stack have in common?
- A . They both use DSL configuration language
- B . They both use YAML configuration language
- C . They both have agents running on the client machine
- D . They both can be designed with more than one master server
Latest 350-501 Dumps Valid Version with 248 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund